The cybersecurity community is sounding the alarm about the growing risk of a “mobile NotPetya” event – a self-propagating mobile malware outbreak that could have devastating consequences.
Over the past year, the alarming increase in the discovery and exploitation of zero-click vulnerabilities in mobile operating systems drives this concern.
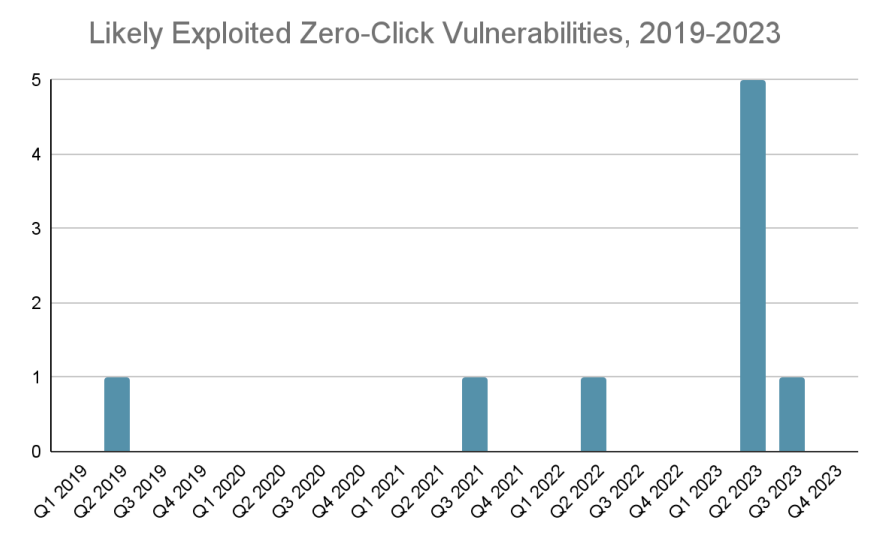
In 2023 alone, more zero-click vulnerabilities were disclosed than combined in the prior four years.

Experts warn that the conditions are ripe for a mobile malware event on the scale of the 2017 NotPetya ransomware attack, which caused over $10 billion in damages worldwide.
Free Live Webinar for DIFR/SOC Teams: Securing the Top 3 SME Cyber Attack Vectors - Register Here.
The Rise of Zero-click Exploits
The critical ingredient for a “mobile NotPetya” is malware’s ability to spread autonomously through zero-click vulnerabilities without requiring user interaction.
Over the past few years, there has been a troubling surge in the discovery and exploitation of such vulnerabilities:
- In May 2019, a WhatsApp zero-click vulnerability (CVE-2019-3568) allowed attackers to deliver Pegasus spyware to victims via malicious RTCP packets.
- In December 2020, Citizen Lab reported on the “KISMET” zero-click exploit, which abused iOS 13.5’s messaging components to infect devices with Pegasus.
- In September 2021, Citizen Lab disclosed the “FORCEDENTRY” zero-click exploit, which targeted a vulnerability (CVE-2021-30860) in Apple’s image rendering library.
- In April 2023, Apple patched a zero-click vulnerability (CVE-2023-28205) in iOS that may have been actively exploited.
- In June 2023, Kaspersky disclosed the “Operation Triangulation” campaign, which exploited six zero-day vulnerabilities, including one that could write to unknown hardware registers.
The number of disclosed zero-click exploits has skyrocketed, from just 3 in 2019-2022 to 6 in the first two quarters of 2023 alone.
Experts warn that this trend will continue as spyware firms and other threat actors dedicate resources to finding and exploiting these vulnerabilities.
Recorded Future recently released an article highlighting the surge in zero-click vulnerabilities in the Mobile NotPetya malware.
The article also discusses the favorable conditions for such vulnerabilities to be exploited.
Conditions Ripe for a “Mobile NotPetya”
The key elements for a devastating mobile malware outbreak are all in place:
- Zero-click exploits: Spyware firms’ ongoing development of zero-click vulnerabilities allows malware to spread autonomously.
- Autonomous spread: Mobile malware could abuse contact lists and Bluetooth to propagate to new victims.
- Monoculture landscape: Android and iOS dominate the mobile OS market, meaning a single vulnerability could have an outsized impact.
- Lack of effective mitigations: Measures like Apple’s Lockdown Mode are unlikely to be widely adopted, and tech companies have no clear public plans to stop a mobile malware outbreak.
- Heightened motivations: Geopolitical tensions and the sophistication of cybercriminal groups increase the risk of a mobile malware attack being deployed deliberately or accidentally.
Experts believe telecommunications providers and device manufacturers may have some tools to stop a mobile NotPetya in its tracks, such as:
- Filtering messages based on header information that is consistent across malicious messages
- Blocking messages originating from geographic clusters of infected devices
However, these measures have not been tested at scale and may only be implemented once an outbreak is underway, limiting their effectiveness.
The cybersecurity community is sounding the alarm – the conditions are ripe for a devastating “mobile NotPetya” event.
The risk of a large-scale mobile malware outbreak is growing with the surge in zero-click vulnerabilities and the lack of clear mitigation strategies.
Tech companies, governments, and the security community must urgently address this emerging threat before it’s too late.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAP




