A critical flaw in the Mobile Security Framework (MobSF) has been discovered, allowing authenticated attackers to upload and execute malicious files by exploiting improper path validation.
The vulnerability, present in version 4.4.0 and patched in 4.4.1, underscores the importance of rigorous sanitization when handling user‐supplied file paths and archives.
Key Takeaways
1. MobSF v4.4.0 allowed attackers to exploit file path flaws to access sensitive files.
2. These vulnerabilities risked data leaks and system corruption.
3. Update and secure the platform.
Directory Traversal Vulnerability (CVE-2025-58161)
The first issue resides in the download handler implemented in MobSF/views/home.py. The function naively strips the /download/ prefix and concatenates the remaining string to the configured settings.DWD_DIR using Python’s Path API:
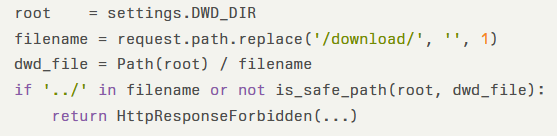
Here, is_safe_path() uses os.path.commonprefix() to verify that the resolved check_path begins with the safe_root.
However, since commonprefix compares raw strings, a sibling directory named /home/mobsf/.MobSF/downloads_bak is incorrectly considered inside /home/mobsf/.MobSF/downloads. By issuing a request like:
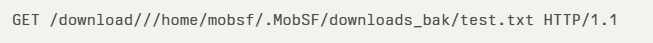
An attacker can retrieve any file with an allowed extension from the sibling directory.
This Directory Traversal vulnerability (CVE-2025-58161) carries a Low severity rating (CVSS 3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:N) and affects all installations using version 4.4.0 of the mobsf package.
Absolute Path Slip Vulnerability
A second, more severe weakness (CVE-2025-58162) affects the AR archive extraction logic in mobsf/StaticAnalyzer/views/common/shared_func.py.
The ar_extract() function decodes each archive member name and filters only for relative‐path traversals (.., %2e%2e, etc.), neglecting absolute filenames:
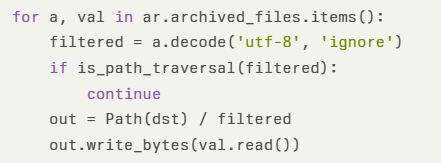
When filtered begins with /, Path(dst) / filtered resolves to the absolute path. An attacker-controlled .a archive containing a member like /home/mobsf/.MobSF/db.sqlite3 results in overwriting the database file outside the intended static_objects directory.
Demonstrations showed that uploading a crafted archive triggers a server error and corrupts the SQLite database, leading to malfunctioning scans and potential Stored XSS by tampering with static templates.
This Moderate severity flaw (CVSS 3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:H) enables arbitrary file writes under the MobSF process’s privileges, risking distortion of analysis results, integrity compromise, and service disruption.
| CVE ID | Title | CVSS 3.1 Score | Severity |
| CVE-2025-58161 | Path Traversal in MobSF Download Route | 0 | Low |
| CVE-2025-58162 | Arbitrary File Write via .a Archive Extraction | 7.4 | Moderate |
Mitigation
Credit for discovering these vulnerabilities goes to Vasily Leshchenko (Solar AppSec) and the reporter noname1337h1.
Both issues have been addressed in MobSF 4.4.1. Users should upgrade immediately. Recommended fixes include:
- Rejecting absolute paths by normalizing input with os.path.isabs() checks.
- Using os.path.commonpath() instead of commonprefix() for robust directory boundary enforcement.
- Ensuring archive extraction always verifies that normalized target paths remain under the intended root.
Find this Story Interesting! Follow us on Google News, LinkedIn, and X to Get More Instant Updates.
