The private code signing keys for the multinational Taiwanese technology business Micro-Star International (MSI) Co., Ltd. have been made public on a dark website by the threat actors that launched the ransomware attack against it last month.
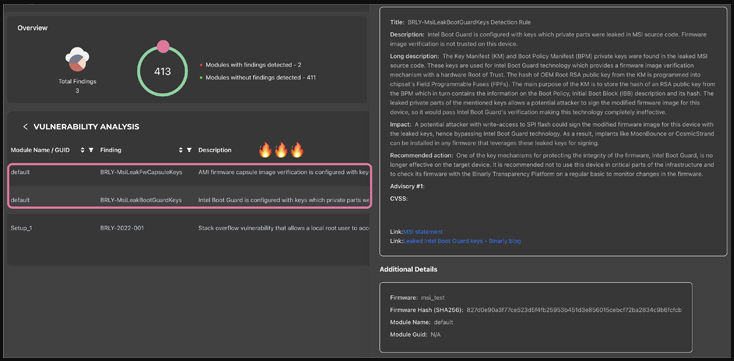
“Confirmed, Intel OEM private key leaked, causing an impact on the entire ecosystem,” Firmware security company Binarly’s founder and CEO, Alex Matrosov, stated in a tweet.
“It appears that Intel Boot Guard may not be effective on certain devices based on the 11th Tiger Lake, 12th Adler Lake, and 13th Raptor Lake.”
Intel BootGuard Private Keys Leaked
Reports say private signing keys for Intel Boot Guard used on 116 MSI devices and firmware image signing keys connected to 57 PCs are also included in the stolen data.

A hardware-based security mechanism, Intel Boot Guard, prevents computers from running tampered UEFI firmware.
It’s thought that the MSI Boot Guard keys will affect several hardware manufacturers, including Intel, Lenovo, and Supermicro.
Supermicro stated that it had studied the dangers of releasing Intel Boot Guard keys and that its devices are unaffected.
“Based on our current review and investigation, Supermicro products are not affected,” a spokesperson for the San Jose-based company said.
A month ago, a new ransomware group called Money Message attacked MSI with double extortion ransomware attacks.
MSI’s regulatory filing states, “the affected systems have gradually resumed normal operations, with no significant impact on financial business.”
Nevertheless, the company recommended consumers avoid downloading files from other sources and only get firmware and BIOS upgrades from its official website.
The disclosure of the Intel Boot Guard keys offers substantial dangers since it compromises a critical firmware integrity check, allowing threat actors to sign malicious updates and other payloads and distribute them on targeted devices without raising any red flags.
MSI also urged users to watch out for fake communications posing as from the company and aimed at the online gaming community under the pretext of a potential partnership.
The UEFI firmware code has previously been made available to the public. The leak of the private signing key used for Boot Guard as well as the Alder Lake BIOS source code by a third party, was acknowledged by Intel in October 2022.
Struggling to Apply The Security Patch in Your System? –
Try All-in-One Patch Manager Plus

