The cyberthreat landscape witnessed a concerning evolution in 2025 as the notorious Muddled Libra threat group dramatically shifted their attack methodology, pivoting from traditional phishing campaigns to sophisticated voice-based social engineering targeting organizational call centers and help desks.
This Western-based collective, comprising primarily young English-speaking cybercriminals, has transformed their operational approach to achieve unprecedented speed and impact in corporate infiltrations.
The group’s new modus operandi centers on exploiting the fundamental trust relationships between employees and IT support personnel.
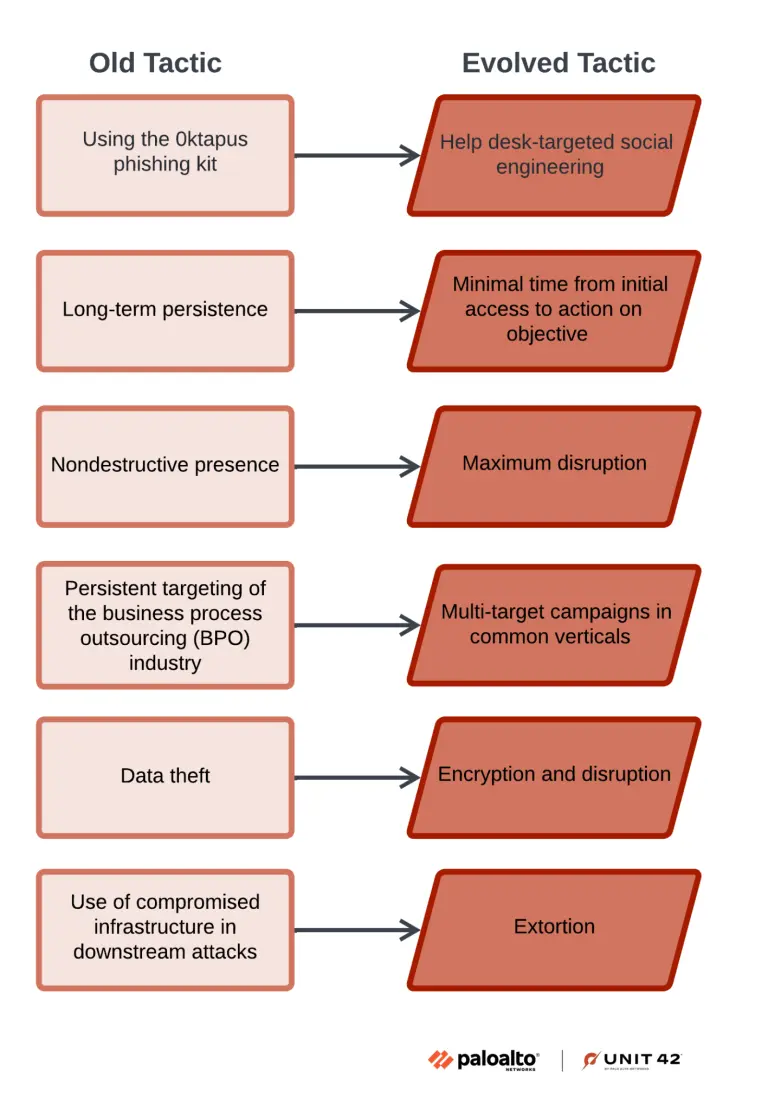
Rather than relying on their previously favored Oktapus phishing kit, Muddled Libra actors now engage in direct human manipulation through carefully orchestrated voice calls to organizational help desks.
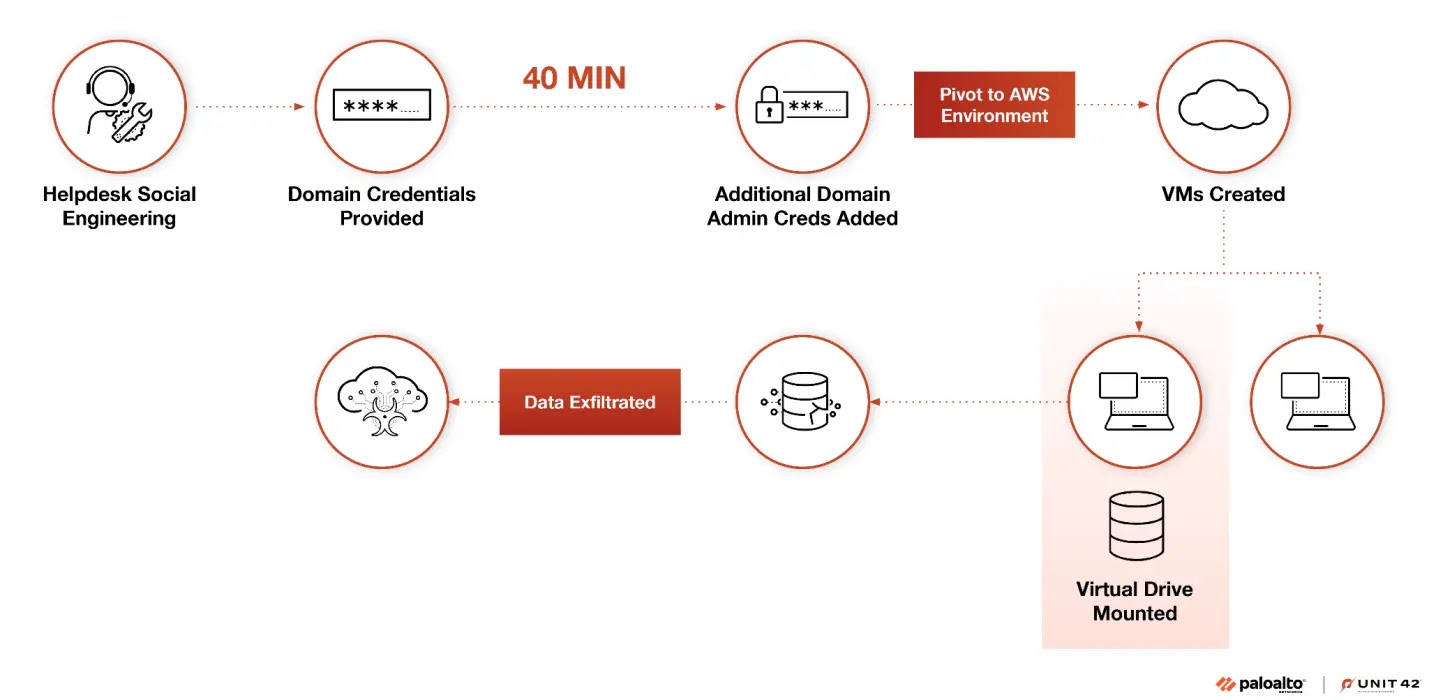
This tactical evolution has proven devastatingly effective, reducing their average intrusion timeline to just 1 day, 8 hours, and 43 minutes from initial access to containment.
Palo Alto Networks researchers identified this strategic shift as part of Muddled Libra’s broader evolution toward maximum disruption and rapid monetization.
The threat actors have demonstrated remarkable adaptability, moving from long-term persistent campaigns to lightning-fast operations that achieve domain administrator privileges within approximately 40 minutes of initial access.
.webp)
Their targeting scope has expanded significantly throughout 2025, encompassing government entities from January through March, followed by concentrated attacks on insurance sectors from April through July, alongside simultaneous campaigns against retail and aviation industries.
Voice-Based Social Engineering: The New Attack Vector
The cornerstone of Muddled Libra’s enhanced capabilities lies in their sophisticated voice-based phishing (vishing) operations, classified under MITRE ATT&CK technique T1566.004.
Intelligence analysis reveals that over 70 percent of the phone numbers utilized by this group in 2025 leveraged Google Voice as their Voice Over Internet Protocol service, providing anonymity and scalability for their operations.
The attack methodology follows a predictable yet effective pattern where threat actors contact organizational help desks while impersonating legitimate employees who have purportedly lost access to their multi-factor authentication devices.
By exploiting the natural inclination of help desk personnel to provide assistance, attackers manipulate these gatekeepers into bypassing established authentication controls and resetting both user credentials and MFA methods.
.webp)
In alternative scenarios, the actors reverse the social engineering dynamic by directly contacting victims while masquerading as internal IT support staff, convincing targets to install remote management software that provides immediate system access.
This voice-centric approach has enabled Muddled Libra to establish persistence through various remote monitoring and management tools while simultaneously targeting existing systems management platforms and endpoint detection response solutions.
The group’s cloud-first mentality drives them to immediately pivot toward Microsoft 365 and SharePoint environments for internal reconnaissance, often culminating in massive data exfiltration operations exceeding 100 gigabytes within two-day periods before deploying DragonForce ransomware through their partnership with the Slippery Scorpius RaaS program.
Experience faster, more accurate phishing detection and enhanced protection for your business with real-time sandbox analysis-> Try ANY.RUN now
