The Iranian state-sponsored threat actor MuddyWater has been observed exploiting a legitimate remote monitoring and management (RMM) tool, Atera Agent, to conduct a sophisticated malware delivery campaign.
This alarming trend has been under scrutiny since the beginning of 2024, with a notable increase in activity since October 2023, coinciding with the Hamas attack during the same period.
MuddyWater, recognized for its state-sponsored cyber activities, has a history of leveraging legitimate RMM software to deploy initial payloads in its cyberattacks.
This tactic has been a part of their modus operandi since at least 2021.
According to the Harfang Lab report, the group’s strategic use of RMM tools allows it to maintain a low profile, making its malicious activities more complicated to detect as they blend in with regular network traffic.
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide
MuddyWater Hackers
The MuddyWater group, also known as SeedWorm or TEMP.Zagros, has been active since 2017 and is known for its espionage campaigns that primarily target entities in the Middle East.
However, their activities have expanded globally, affecting various sectors, including telecommunications, government, and oil industries.
The group’s sophisticated techniques and state backing make them a formidable threat in the cyber domain.
The RMM tool, Atera Agent, is designed to help IT professionals manage networks and provide remote support.
While such tools are invaluable for legitimate IT operations, they also present an attractive vector for cyber attackers.
MuddyWater’s exploitation of Atera Agent demonstrates how threat actors can subvert trusted software to gain unauthorized access to systems and networks.
MuddyWater’s campaign uses the Atera Agent to deliver malware to compromised systems.
By abusing the trust in RMM tools, the group can deploy malicious payloads without raising immediate suspicion.
This approach facilitates the initial breach and aids in establishing persistence within the targeted networks, enabling long-term access and data exfiltration.
Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
Atera Agent
In recent campaigns, the Atera Agent has become a tool of choice for MuddyWater.
The software’s legitimate nature allows threat actors to conduct their operations under the guise of regular administrative activity.
This has significant implications for cybersecurity defenses, as distinguishing between legitimate and malicious use of such tools becomes increasingly challenging.
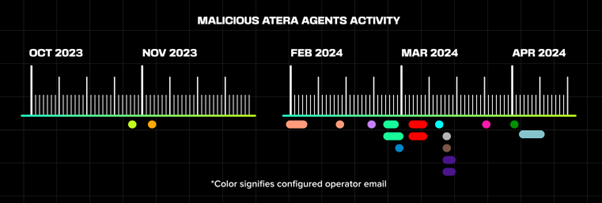
The campaign’s timeline traces back to October 2023, when malicious activities surged following the Hamas attack.
This suggests a possible strategic alignment or opportunistic exploitation of the chaotic digital environment post-attack.
The timeline reflects MuddyWater’s evolving tactics as it adapts and refines its methods to exploit the latest software vulnerabilities and operational blind spots.
The revelation of MuddyWater’s latest campaign underscores the need for heightened vigilance and robust cybersecurity measures.
Organizations must be aware of the potential misuse of legitimate tools within their environment and implement strategies to detect and mitigate such threats.
As threat actors evolve, so must the defenses of those they target.
Indicators of compromise (IOCs)
Hashes (SHA-256)
9b49d6640f5f0f1d68f649252a96052f1d2e0822feadd7ebe3ab6a3cadd75985|Atera Agent5d7eb6c36d261adeef1a59bde9eb965f5d8d7f56a2e607da913e782167ba6cb6|Atera Agent
14c270cf53a50867e42120250abca863675d37abf39d60689e58288a9e870144|Atera Agent, Tejasnetworks.com.webinar.msi
638c7a4f833dc95dbab5f0a81ef03b7d83704e30b5cdc630702475cc9fff86a2|Atera Agent, Polaristek.msi
dd2675e2f6835f8a8a0e65e9dbc763ca9229b55af7d212da38b949051ae296a5|Atera Agent, karel.com.tr.telekomünikasyonWebsemineri.msi / comviva.com.webinar.msi
165a80f6856487b3b4f41225ac60eed99c3d603f5a35febab8235757a273d1fd|Atera Agent, setup_aleh_aleh.msi
d22fd0cdd6ace24e117d7330e9996a2809c2c2cb280b12f9ea43c484d2bfcfd4|Atera Agent, setup_aleh_aleh (1).msi
f9c1a117de8519060a3bf189e72277e895345b8fece73fc0d750946c7f288367|Atera Agent, BLUMENTAL.WEBINAR.msi
2722e289767ae391e3c3773b8640a8b9f6eb24c6a9d6e541f29c8765f7a8944b|Atera Agent, IronSword.msi
ffbe988fd797cbb9a1eedb705cf00ebc8277cdbd9a21b6efb40a8bc22c7a43f0|Atera Agent
2ae6c5c2b71361f71ded4ad90bbf6ef0b0f4778caf54078c928e2017302fbe69|Atera Agent
c6128f222f844e699760e32695d405bd5931635ec38ae50eddc17a0976ccefb4|Atera Agent, מילגה.msi
ff2ae62ba88e7068fa142bbe67d7b9398e8ae737a43cf36ace1fcf809776c909|Atera Agent, תוכנת תיירות.msi
c2f95299d8aa912e1b753f3f0780a00ea6e8b5dab0245d77fcf3b6499677c328|Atera Agent, Leonardo Hotels-tourism software.msi
e89f48a7351c01cbf2f8e31c65a67f76a5ead689bb11e9d4918090a165d4425f|Atera Agent, Salary.msi
326dd85d76d33f3f04cbe7eef6d10ea73f800c84bfc3ed6f3963403c981bbb6e|Atera Agent, virtual-library.msi
ec553e14b84ccca9b84e96a9ed19188a1ba5f4bf1ca278ab88f928f0b00b9bd0|Atera Agent
09e09503962a2a8022859e72b86ad8c69dcbf79839b71897c0bf8a4c4b9f4dd6|Atera Agent, digitalform.msi
fb58c54a6d0ed24e85b213f0c487f8df05e421d7b07bd2bece3a925a855be93a|Atera Agent, תכנית מועצת מחוז גולן.msi
4b41b605ffc0e31bd9d460d5a296ac6e8cfd56a215dc131e90ec2654f0ffe31b|Malicious Zip archive, karel.com.tr.telekomünikasyonWebsemineri.zip
85103955e35a1355ce68a92eaedd8f9376de1927d95bf12657b348dea6a8077b|Malicious Zip archive, Tejasnetworks.com.webinar.zip
bab601635aafeae5fbfe1c1f7204de17b189b345efd91c46001f6d83efbb3c5a|Malicious Zip archive, comviva.com.webinar.zip
900d08037d303d9b3d4a855e1a97d1f9283c28fe279e67eefe9997f856eeb439|Malicious Zip archive
cc8be1d525853403f6cfabcf0fc3bd0ca398ece559388102a7fc55e9f3aa9b33|Malicious Zip archive
7daab239271e088f04cae95627cc0066f48a1b178a1ff60b1140aa729126e928|Malicious Zip archive, Leonardo Hotels-tourism software.zip
cc4cc20b558096855c5d492f7a79b160a809355798be2b824525c98964450492|Malicious Zip archive, Salary.zip
31591fcf677a2da2834d2cc99a00ab500918b53900318f6b19ea708eba2b38ab|Malicious Zip archive, תכנית מועצת מחוז גולן.zip
f17f6866f4748e6e762752062acdf983d3b083371db83503686b91512b9bcae3|Malicious Zip archive, digitalform.zip
7e6a5e32596b99f45ea9099a14507a82c10a460c56585499d7cd640f2625567f|Malicious Zip archive, Polaristek.zip
fb02e97d52a00fca1580ca71ed152dd28dd5ae28ab0a9c8e7b32cebd7f1998a1|Malicious Zip archive, מילגה.zip
Combat Email Threats with Easy-to-Launch Phishing Simulations: Email Security Awareness Training -> Try Free Demo