A new Android banking trojan named Sturnus can capture communication from end-to-end encrypted messaging platforms like Signal, WhatsApp, and Telegram, as well as take complete control of the device.
Although still under development, the malware is fully functional and has been configured to target accounts at multiple financial organizations in Europe by using “region-specific overlay templates.”
Sturnus is a more advanced threat than current Android malware families, using a mix of plaintext, RSA, and AES-encrypted communication with the command-and-control (C2) server.

Full Android device takeover
A report from online fraud prevention and threat intelligence solutions ThreaFabric explains that Sturnus can steal messages from secure messaging apps after the decryption stage by capturing the content from the device screen.
The malware can also steal banking account credentials using HTML overlays and includes support for full, real-time remote control via VNC session.
Based on the indicators of compromise in ThreatFabric’s report, the malware is likely disguised as Google Chrome or Preemix Box applications. However, the researchers have not discovered how the malware is distributed.
After installation, the malware connects to the C2 infrastructure to register the victim via a cryptographic exchange.
It establishes an encrypted HTTPS channel for commands and data exfiltration, and an AES-encrypted WebSocket channel for real-time VNC operations and live monitoring.
By abusing the Accessibility services on the device, Sturnus can start reading on-screen text, capture the victim’s inputs, observe the UI structure, detect app launches, press buttons, scroll, inject text, and navigate the phone.
To gain full control of the device, Sturnus obtains Android Device Administrator privileges, which let it keep track of password changes and unlock attempts, and lock the device remotely.
The malware also tries to prevent the user from removing its privileges or uninstalling it from the device.
“Until its administrator rights are manually revoked, both ordinary uninstallation and removal through tools like ADB are blocked, giving the malware strong protection against cleanup attempts” – ThreatFabric
When the user opens WhatsApp, Telegram, or Signal, Sturnus uses its permissions to detect message content, typed text, contact names, and conversation contents.
Source: Threat Fabric
“Because it relies on Accessibility Service logging rather than network interception, the malware can read everything that appears on screen—including contacts, full conversation threads, and the content of incoming and outgoing messages—in real time,” the researchers say in the report.
“This makes the capability particularly dangerous: it completely sidesteps end-to-end encryption by accessing messages after they are decrypted by the legitimate app, giving the attacker a direct view into supposedly private conversations.”
The VNC mode enables the attackers to click buttons, enter text, scroll, and navigate the phone OS and apps, all powered by Accessibility.
Source: Threat Fabric
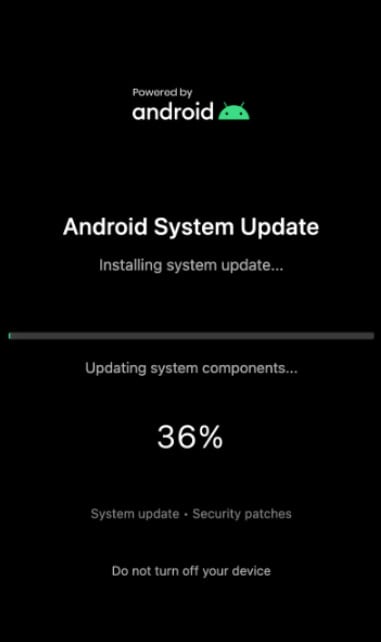
When ready, they enable a black overlay and perform actions that stay hidden from the victim, and may include money transfers from banking apps, confirming dialogs, approving multi-factor authentication screens, changing settings, or installing new apps.
ThreatFabric’s report shows an example of an overlay for a fake Android System Update screen, displayed to hide malicious actions running in the background.
Source: Threat Fabric
The researchers comment that Sturnus is still in its early development stage, deployed sporadically, likely for testing, rather than in full-scale campaigns.
Still, its combination of advanced features, commonly found in top-tier Android malware, and its “ready to scale” architecture makes this a dangerous threat to look out for.
ThreatFabric detected Sturnus attacks in low-volume, mostly targeting users in Southern and Central Europe, which may indicate that the threat actor is running tests for larger campaigns
Android users are advised to avoid downloading APK files from outside Google Play, keep Play Protect active, and avoid granting Accessibility permissions unless truly needed.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.




