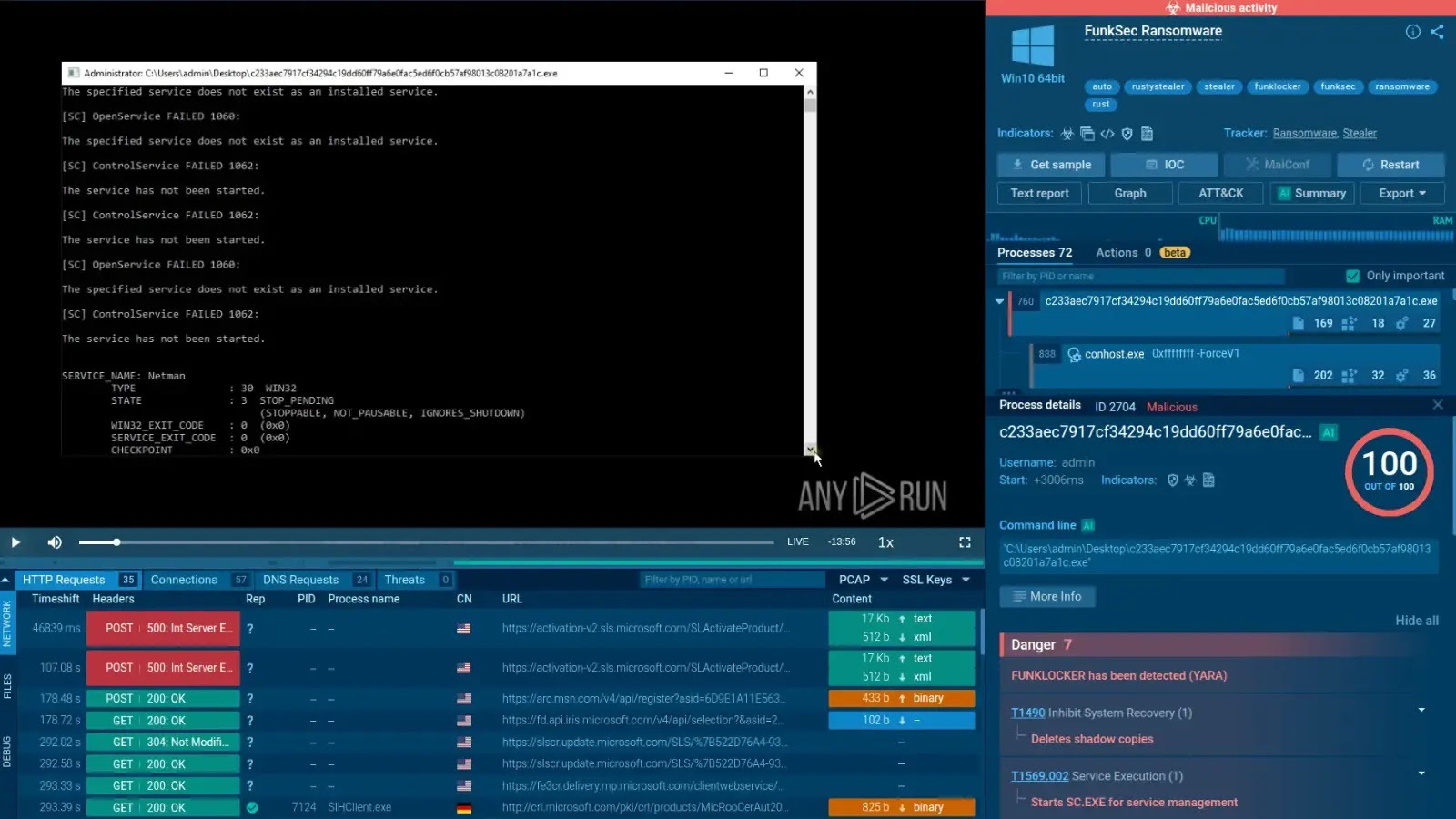
Multiple critical vulnerabilities were identified by the Veritas Technologies in its Enterprise Vault software that allows attackers to execute remote code on affected servers.
These vulnerabilities, disclosed on November 15, 2024, are due to the deserialization of untrusted data and have been classified as critical with a CVSS v3.1 base score of 9.8, indicating a high level of risk.
The vulnerabilities affect the .NET Remoting service used by the Enterprise Vault application. Upon startup, the application initiates several services that listen for commands on random TCP ports.
These ports can be exploited by attackers who gain access to the network, allowing them to execute malicious code remotely.
The vulnerabilities were reported by Trend Micro’s Zero-Day Initiative (ZDI) and involve seven separate issues identified as “ZDI-CAN-24334” through “ZDI-CAN-24405.”
.webp)
To exploit these vulnerabilities, an attacker must meet specific conditions:
- Remote Desktop Protocol (RDP) Access: The attacker must have RDP access to a virtual machine within the network, requiring membership in the Remote Desktop Users group.
- Knowledge of Network Details: The attacker needs to know the IP address of the Enterprise Vault server, its process IDs, dynamic TCP ports, and remoteable object URIs.
- Firewall Configuration: The server’s firewall must be improperly configured to allow exploitation.
Security experts at Veritas Technologies identified that if these conditions are met, attackers can send specially crafted data to the vulnerable server, leading to remote code execution.
Leveraging 2024 MITRE ATT&CK Results for SME & MSP Cybersecurity Leaders – Attend Free Webinar
Affected Versions
All currently supported versions of Enterprise Vault are affected, including versions 15.1 down to 14.0. Older versions might also be vulnerable but are no longer supported.
Veritas has outlined several mitigation strategies to protect against these vulnerabilities:-
- Restrict server access to only Enterprise Vault administrators.
- Limit RDP access to trusted users only.
- Ensure proper firewall configuration and activation.
- Install the latest Windows updates on the Enterprise Vault server.
Veritas plans to release a patch addressing these vulnerabilities in version 15.2 of Enterprise Vault, expected in the third quarter of 2025.
Until then, IT administrators are advised to implement these temporary countermeasures to reduce the risk of exploitation. Veritas acknowledges ‘Sina Kheirkhah’ from Trend Micro’s ZDI for reporting these vulnerabilities.
This critical security advisory highlights the importance of maintaining robust security protocols and staying informed about software vulnerabilities that could impact organizational data integrity and security.
Analyze cyber threats with ANYRUN's powerful sandbox. Black Friday Deals : Get up to 3 Free Licenses.