A new threat has emerged in the cybersecurity landscape as security experts discover a private Out-of-Band Application Security Testing (OAST) service operating on Google Cloud infrastructure.
This mystery operation stands out from typical exploit scanning activities because it uses custom infrastructure rather than relying on public services. The attackers have been running a focused campaign that targets specific regions with over 200 different vulnerabilities.
Between October and November 2025, researchers observed roughly 1,400 exploit attempts spanning more than 200 CVEs linked to this operation.
Unlike most attackers who use public OAST services like oast.fun or interact.sh, this threat actor operates their own private OAST domain at detectors-testing.com.
This unusual setup caught attention when callbacks started appearing to subdomains of i-sh.detectors-testing.com, a domain not associated with any known OAST provider or popular scanning framework.
VulnCheck security researchers identified this operation after noticing unusual patterns in their Canary Intelligence traffic.
The campaign combines standard Nuclei scanning templates with custom payloads to expand their reach. What makes this operation particularly interesting is that all observed activity targeted systems deployed in Brazil, suggesting a clear regional focus.
While the same attacker IP addresses were flagged in Serbia and Turkey through AbuseIPDB reports, VulnCheck’s dataset showed activity concentrated entirely on Brazilian targets.
The infrastructure behind this operation consists of multiple Google Cloud IP addresses, with six addresses used as exploit scanners and one as the OAST host.
Using Google Cloud provides practical advantages for attackers since defenders rarely block major US cloud providers, and traffic to Google networks easily blends with normal background communication.
The operation has been running since at least November 2024, indicating a long-term sustained effort rather than quick opportunistic scans.
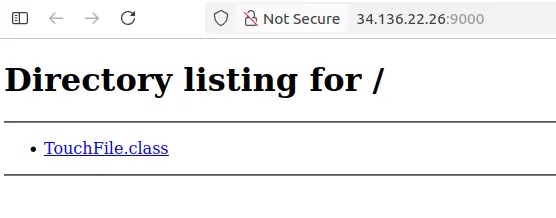
Evidence from an open directory on port 9000 revealed a modified Java class file called TouchFile.class, originally documented in Fastjson 1.2.47 exploitation examples.
The attackers extended the basic version to accept custom commands and HTTP requests through parameters, showing they actively modify publicly available exploit tools rather than using them unchanged.
The decompiled code shows that if no parameters are provided, it runs a default command to touch /tmp/success3125, but when cmd or http parameters are present, it executes those commands or makes outbound HTTP requests instead.
Technical Breakdown of the Exploit Mechanism
The attackers use a mix of current and outdated Nuclei templates to probe for vulnerabilities. One example is the old grafana-file-read.yaml template, which was removed from the official nuclei-templates repository in early October 2025.
Finding this older template in active use suggests the attackers either use third-party Nuclei-based scanners like dddd or simply have not updated their scanning tools.
This combination of old and new templates helps them cast a wider net across different vulnerability types.
.webp)
The exploit payloads follow a standard pattern where successful exploitation triggers the compromised host to make HTTP requests back to the attacker-controlled OAST subdomains.
For instance, in an attempt against CVE-2025-4428 affecting Ivanti Endpoint Manager Mobile, the payload would force the victim system to contact d4bqsd6e47mo47d93lpgq55d3j111y6em.i-sh.detectors-testing.com.
This callback mechanism allows attackers to verify which systems are vulnerable without needing direct access, making detection more challenging for defenders.
The OAST host at 34.136.22.26 consistently presents Interactsh services across ports 80, 443, and 389, confirming its role as a dedicated command and control endpoint for collecting exploit verification callbacks from compromised systems worldwide.
Follow us on Google News, LinkedIn, and X to Get More Instant Updates, Set CSN as a Preferred Source in Google.
