FortiGuard Labs has discovered a sophisticated new ransomware strain called NailaoLocker that represents a significant departure from conventional encryption malware.
This Windows-targeting threat introduces the first documented use of China’s SM2 cryptographic standard in ransomware operations, marking a notable shift toward region-specific cryptographic implementations in cybercriminal activities.
The malware’s name, derived from the Chinese word for “cheese,” may hint at its true purpose as either a functional weapon or an elaborate trap designed to mislead security researchers and victims alike.
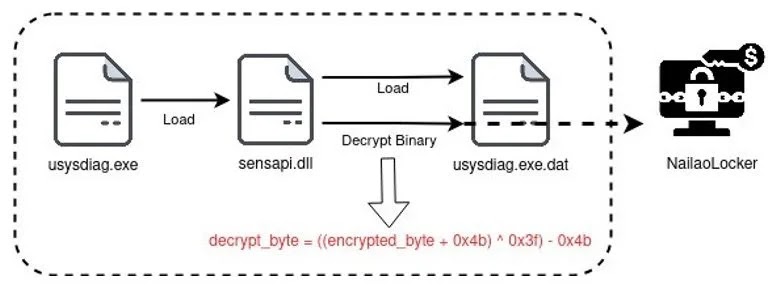
NailaoLocker employs a multi-component delivery system consisting of three carefully orchestrated files: a legitimate executable (usysdiag.exe) used for DLL side-loading, a malicious loader (sensapi.dll), and an obfuscated payload (usysdiag.exe.dat).
This sophisticated deployment mechanism allows the ransomware to execute with minimal detection while immediately cleaning up forensic traces by deleting the loader component after successful execution.
The malware creates a mutex named “lockv7” to prevent multiple instances and launches a console window that openly displays its encryption progress, suggesting no intention to conceal its activities from infected users.
Fortinet analysts identified several unique characteristics that distinguish NailaoLocker from traditional ransomware families.
Most notably, the malware incorporates hard-coded SM2 key pairs embedded in ASN.1 DER format alongside a built-in decryption function, an extremely rare combination that raises questions about its intended purpose.
.webp)
While conventional ransomware typically uses RSA to protect file encryption keys, NailaoLocker pioneers the use of SM2 elliptic curve cryptography to secure its AES-256-CBC encryption keys, representing the first documented instance of this approach in the ransomware landscape.
Advanced Encryption Architecture and Multi-Threading Implementation
The ransomware’s technical sophistication extends to its execution architecture, which leverages Windows I/O Completion Ports (IOCP) to implement high-performance multi-threaded encryption operations.
This design enables NailaoLocker to efficiently distribute file processing across multiple CPU cores, with the malware creating a minimum of eight worker threads regardless of system specifications to ensure optimal performance even on lower-end hardware configurations.
During the encryption process, NailaoLocker generates unique cryptographic material for each target file using the Windows BCryptGenRandom() function to create 32-byte AES keys and 16-byte initialization vectors.
The malware then uses its embedded SM2 public key to encrypt these symmetric encryption components, storing the variable-length encrypted keys in a structured footer that begins with the marker “LV7.”
This footer contains the encrypted AES key size, the encrypted key itself, the encrypted IV size, and the encrypted IV, along with any overflow data that results from the encryption padding process.
Testing revealed that while the embedded SM2 private key appears non-functional in practice, the decryption logic operates correctly when supplied with valid AES material captured during encryption.
This discovery, combined with the malware‘s deliberate exclusion of critical system files and directories, suggests NailaoLocker may represent an in-development strain or internal testing build rather than an active deployment ready for widespread distribution.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now
