In its latest cyber attack on European nations, the pro-Russian hacker group NoName has claimed to launch a Distributed Denial-of-Service (DDoS) attack against critical infrastructures in Poland.
The hacker collective has targeted key institutions, including the National Bank of Poland and the website of the Polish Computer Security Incident Response Team (CSIRT GOV). The bank, also called Narodowy Bank Polski (NBP), reportedly failed to defend the DDoS attack.
National Bank of Poland cyber attack
Several threat intelligence services reported that the website was inactive for some time on Sunday after the alleged National Bank of Poland cyber attack. The website became live at the time of publishing this report.
The National Bank of Poland cyber attack is the latest DDoS strikes in the list of several Polish organizations named by the hacker group in the recent past.
The Cyber Express has reached out to the bank for an official statement regarding the reported cyber attack on the National Bank of Poland. We will updates the report once their response is received.
In a Telegram post, after claiming the attack on CSIRT GOV, the the NoName hacker group wrote, “The website of the Polish company CSIRT GOV, which monitors computer security incidents and is headed by the head of the internal security agency, was slammed.”
NoName Havoc: National Bank of Poland Cyber Attack and 843 Others
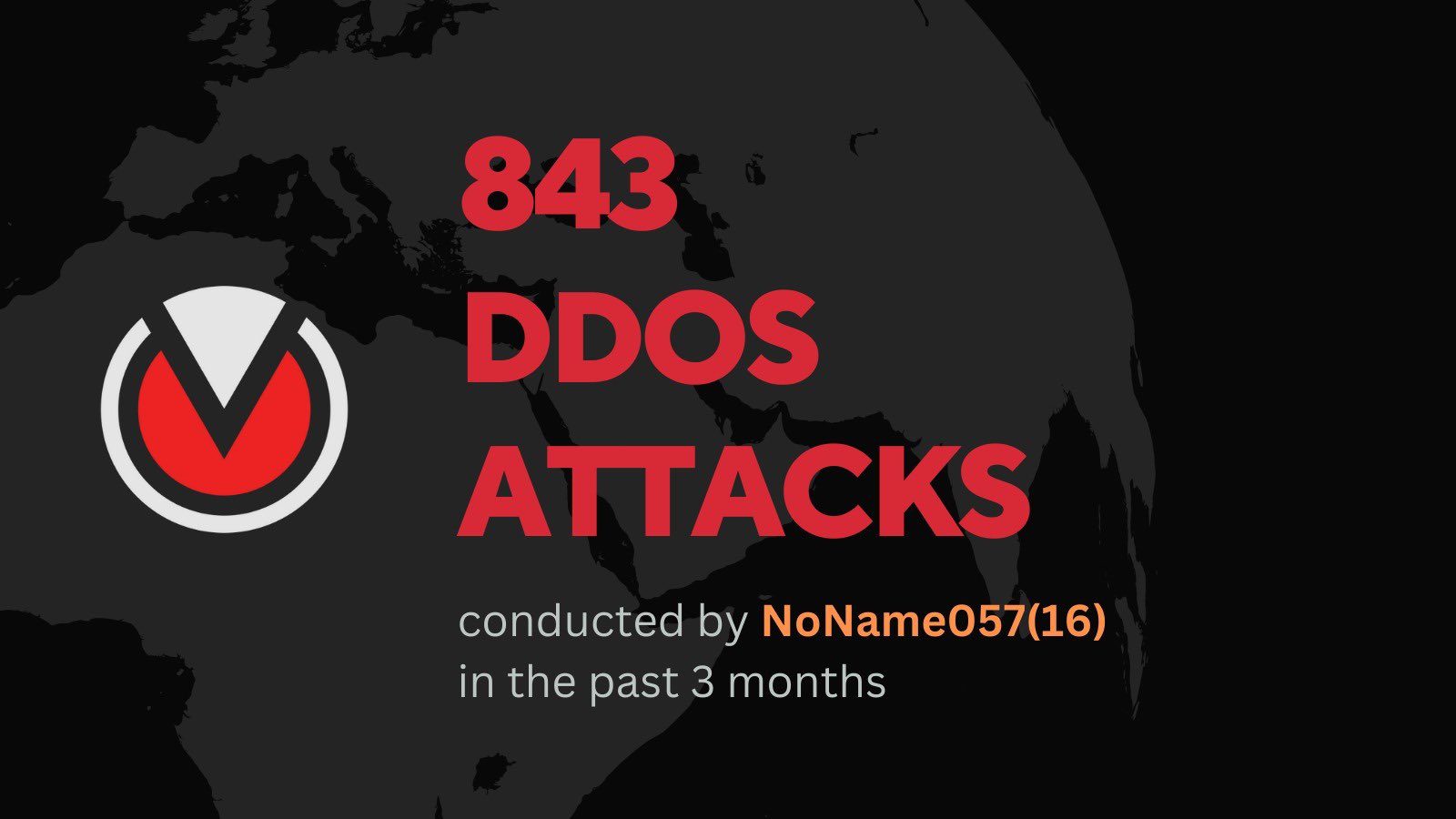
According to threat intelligence service Falcon Feeds, NoName executed close to 850 DDoS attacks in the past three months, including the cyber attack on the National Bank of Poland, under its DDosia project.

The pro-Russian hackers have been inviting criminals to join DDosia, which is a crowdsourced model to launch DDoS attacks.
The group was reported to be offering nearly 80,000 Roubles ($1,200) via cryptocurrency for successful DDoS attacks on the targeted organizations, according to a TechMonitor report.
Its botnet increased to over 1,000 targeting Ukrainian and NATO organizations.
Addressing the incentive in an effort to strengthen its hacker group, Martin Chlumecky, a Malware Researcher at Avast said, “For some people, it may be tempting to earn some extra money quickly,” as reported by TechMonitor report.
“We saw that some users in countries like Canada and Germany wanted to join the NoName(057)16 hacker group by trying to download the DDosia executable file and thus carry out DDoS attacks,” Martin added.
Among the European targets, NoName has been attacking government organizations, critical infrastructure, and banks among others.
NoName cyber attacks and the DDoSia project
NoName has been using an updated version of the DDoSia attack tool that can fetch a list of targets for sending a multitude of junk HTTP requests to crash the systems. The new variant is written in the Go programming language.
The DDoSia attack tool was primarily used to launch attacks against Ukraine and NATO countries, specifically those in the Eastern Flank such as Lithuania, Poland, the Czech Republic, and Latvia.
Additionally, major targets of the tool-assisted DDoS attacks included France, the United Kingdom, Italy, Canada, and other European Union nations. These countries were singled out due to their political, military, and economic support for Ukraine throughout the Russian invasion.
NoName057(16) relied on their Telegram channels for communication regarding the DDoSia tool. The hacker group maintained two channels—one in Russian with over 45,000 subscribers and another in English.
NoName’s tools with cross-platform capabilities have been found to impact Windows, Linux, and macOS systems.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.



