The UK’s National Cyber Security Centre (NCSC) has introduced a set of six core principles to help organizations embed strong cybersecurity practices into their everyday operations. Developed in collaboration with government and industry leaders, this guidance aims to instill a lasting culture of security—one that prioritizes both technical controls and human behaviors to achieve sustainable cyber resilience.
Rather than focusing solely on compliance or isolated training efforts, the NCSC’s approach encourages organizations to foster a mindset of cyber hygiene, awareness, and responsibility at all levels. These core principles provide a flexible framework to guide cultural transformation and are tailored to suit organizations of all sizes and industries.
Why Culture Matters in Cybersecurity
Cybersecurity culture encompasses the collective values, behaviors, and norms that shape how individuals think about and respond to security risks. According to the NCSC, successful outcomes are not just the result of technological defenses but emerge when secure behaviors are routinely understood, encouraged, and practiced across the workforce.
The guidance is especially valuable for both cybersecurity professionals and leadership teams. While security teams may define strategies and implement controls, long-term cultural change requires buy-in from leadership—those who shape priorities, influence workplace norms, and model secure behaviors.
The Six Core Principles from NCSC
Frame Cybersecurity as an Enabler
Organizations should align cybersecurity with their mission and objectives. Instead of viewing security as a hindrance, leaders must integrate it as a function that supports productivity, innovation, and trust. For example, framing secure practices as essential to protecting customer trust can create alignment between operational goals and cyber hygiene. When leadership communicates the value of security, it fosters a sense of shared purpose.
Encourage Openness Through Trust and Safety
Creating psychological safety is key to encouraging secure behavior. Employees should feel comfortable reporting incidents, admitting mistakes, or asking questions, without fear of blame. Organizations that foster open communication and transparent incident handling are more agile and responsive to threats. “When people don’t fear punishment for reporting errors, they are more likely to contribute to organizational learning,” says the NCSC.
Adapt to Change to Improve Resilience
Cyber threats evolve quickly, and security must evolve too. This principle encourages organizations to treat change as an opportunity for progress, not a threat. Whether updating policies or introducing new tools, the process should include collaboration across departments. Routine threat monitoring and employee feedback loops can help identify areas for improvement. Importantly, organizations must avoid “change fatigue” by ensuring that updates serve meaningful, strategic purposes.
Acknowledge the Role of Social Norms
Informal behaviors often shape security more than formal rules. Social norms—like sharing passwords or circumventing protocols—can undermine well-intentioned policies if left unchecked. The NCSC recommends identifying both helpful and harmful norms and using positive peer influence to encourage secure behavior. For example, newcomers who see colleagues practicing good cyber hygiene are more likely to adopt those habits themselves.
Recognize Leadership’s Role in Cultural Change
Leadership plays a crucial role in cultivating a secure culture. Leaders must model secure behavior, communicate its value, and build trust. When senior staff demonstrate openness about past mistakes or security challenges, they normalize learning and reduce fear. In contrast, when leadership ignores or bypasses policies, it sets a dangerous precedent. “Leadership sets the tone for the organization and can drive alignment between business and security objectives,” the NCSC notes.
Maintain Accessible and Clear Security Guidance
Security policies must be practical, understandable, and accessible. Overly complex or outdated guidelines not only confuse employees but also increase vulnerability. Policies should be written in plain language, tested in real-world scenarios, and regularly updated. Embedding these rules into onboarding and ongoing training helps reinforce good practices. Clear signage, simple language, and timely updates all contribute to effective governance.
Putting the Principles into Practice
Each principle is accompanied by real-world examples and practical suggestions. For instance:
- Principle 1: Instead of security blocking sales efforts, sales and IT teams collaborate to create secure, efficient workflows.
- Principle 2: Employees are encouraged to flag suspicious activity without fear of repercussions.
- Principle 3: Cross-functional teams work together to find secure alternatives to unauthorized tools.
- Principle 4: Guests are directed to a secure Wi-Fi network instead of being granted internal access.
- Principle 5: Executives avoid excessive permissions, reinforcing best practices in access control.
- Principle 6: Outdated pandemic-era policies are reviewed, updated, and clearly communicated.
Tools to Support Cultural Change
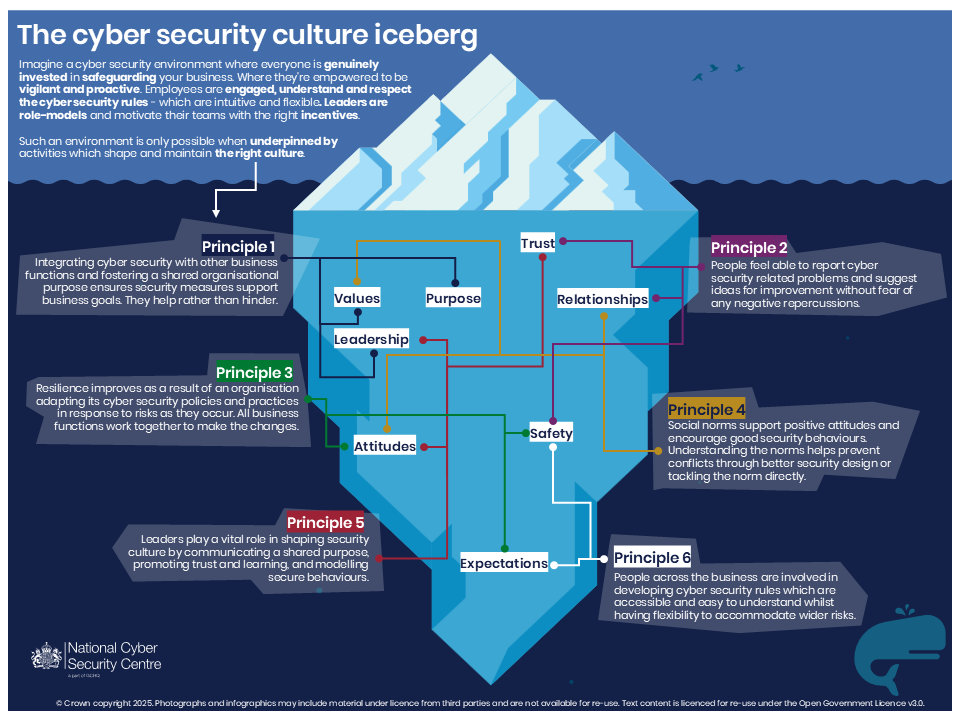
The NCSC also offers the “Cyber Security Culture Iceberg” infographic, illustrating the visible and hidden elements that influence behavior. Surface-level actions—like following password policies—are supported by deeper organizational values, leadership practices, and team dynamics.
- To reinforce these core principles, organizations are encouraged to:
- Establish clear feedback mechanisms to evaluate current practices.
- Bring together diverse stakeholders to collaboratively develop or refine policies.
- Align rules with business goals and ensure they are user-friendly.
- Celebrate secure behavior and use incentives to reinforce good habits.
Related
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
