
Internet security watchdog Shadowserver tracks nearly 800,000 IP addresses with Telnet fingerprints amid ongoing attacks exploiting a critical authentication bypass vulnerability in the GNU InetUtils telnetd server.
The security flaw (CVE-2026-24061) impacts GNU InetUtils versions 1.9.3 (released 11 years ago in 2015) through 2.7 and was patched in version 2.8 (released on January 20).
“The telnetd server invokes /usr/bin/login (normally running as root) passing the value of the USER environment variable received from the client as the last parameter,” explained open-source contributor Simon Josefsson, who reported it.

“If the client supply a carefully crafted USER environment value being the string “-f root”, and passes the telnet(1) -a or –login parameter to send this USER environment to the server, the client will be automatically logged in as root bypassing normal authentication processes.”
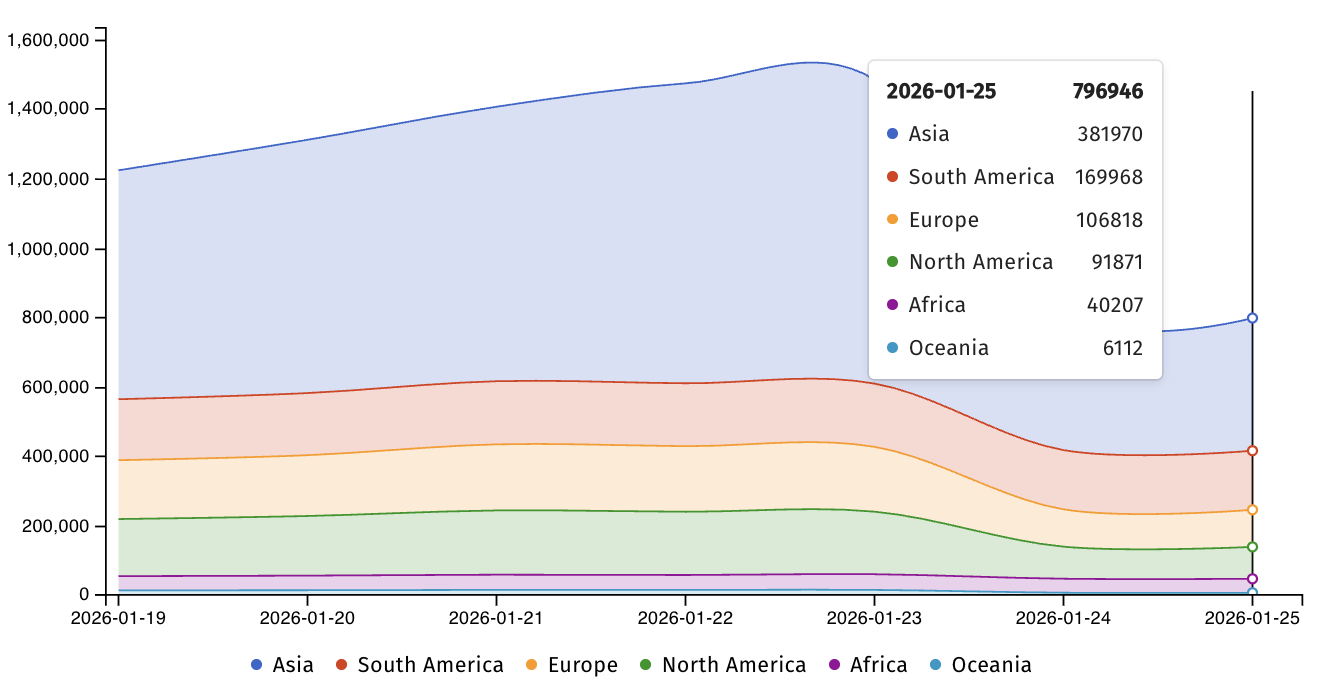
Today, Shadowserver said that it’s tracking nearly 800,000 IP addresses with Telnet fingerprints, over 380,000 from Asia, almost 170,000 from South America, and just over 100,000 from Europe. However, there is no information regarding how many of these devices have been secured against CVE-2026-24061 attacks.
“We are ~800K telnet instances exposed globally – naturally, they should not be. [..] Telnet should not be publicly exposed, but often is especially on legacy iot devices,” said Shadowserver Foundation CEO Piotr Kijewski.
GNU InetUtils is a collection of network utilities (including telnet/telnetd, ftp/ftpd, rsh/rshd, ping, and traceroute) used across multiple Linux distributions that can run without updates for more than a decade on many legacy and embedded devices. This explains its presence in IoT devices, as noted by Kijewski.
On Thursday, days after CVE-2026-24061 was disclosed, cybersecurity company GreyNoise reported that it had already detected exploits for CVE-2026-24061 being used in limited attacks.
The malicious activity started on January 21 (one day after the vulnerability was patched) and originated from 18 IP addresses across 60 Telnet sessions, abusing the Telnet IAC option negotiation to inject ‘USER=-f
While these attacks varied in terminal speed and X11 DISPLAY values, they targeted the ‘root’ user in 83.3% of the cases. Also, even though most of them appear automated, GreyNoise observed some “human-at-keyboard” cases.
After gaining access, the attackers also attempted to deploy Python malware following automated reconnaissance, but these attempts failed due to missing directories and binaries.
Admins who can’t immediately upgrade their devices to the patched release are advised to disable the vulnerable telnetd service or block TCP port 23 on all firewalls.

It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
