In what seems a phishing attack targeted at a certain audience, scammers are impersonating Netflix and reaching out to marketing staff.
The initial mail looks like what you might expect from a headhunter or a human resources (HR) recruitment specialist.
“I hope this note finds you well,” the email begins. “Your reputation as a visionary marketing leader has caught out attention, and I’d like to share an extraordinary opportunity with you at Netflix.”
Undoubtedly this email is crafted by AI and based on real-life examples. The role offered in the email as VP of Marketing would be a fitting role for the person that received this email, so it looks as if the scammers have done their research before reaching out.
Replying to the initial mail—which is not recommended, unless you like letting scammers know you exist and encouraging them to send you more phishes—got us one step closer to landing the exciting new job at Netflix.
We received an invitation to set up an interview with the ‘Netflix HR team’.
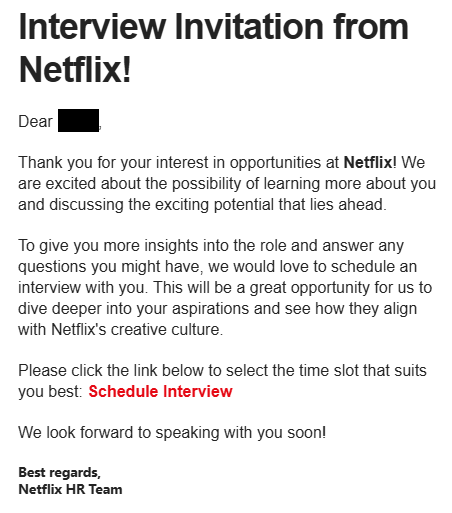
Following the link under “Schedule Interview” gets us a block by Malwarebytes web protection.
![Netflix scammers target jobseekers to trick them into handing over their Facebook logins 3 Malwarebytes blocks hiring.growwithusnetflx[.]com](https://www.malwarebytes.com/wp-content/uploads/sites/2/2025/08/growwithusnetflixcomblock.png)
Again, not something we would want our readers to do but in the interest of learning more about the scam, we bypass that block and proceed to the website.
We find that there are 20 openings, all more or less in the same fields of social media and marketing.
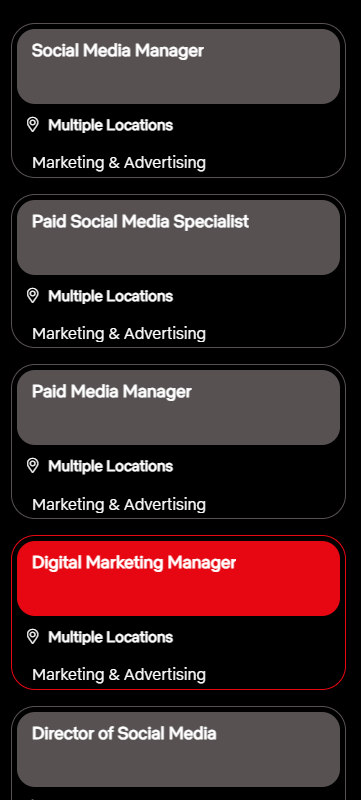
The website itself is a mix of content copied from the actual Netflix site and of the phishing campaign.
Back to scheduling our interview. We’re given an option to choose our interview slot:

Regardless of which of the two buttons you use on the screen, you’ll be asked to sign in to your existing “Career Profile” or create a new one.

At this stage, all red flags should go up. It doesn’t matter if you choose “Continue with Facebook” or whether you enter your email and click “Continue with Email” the next screen will ask you to sign in to your Facebook account.
The only difference is that the second option fills out your email in the login screen.

That doesn’t make a lot of sense—Facebook is not known to keep track of your calendar. It does keep track of a lot of things, but your meeting schedule isn’t one of them. Besides, if you look at the address bar, you’ll see I’m still at the fake Netflix site.
However, it’s very normal practice to offer the option of logging in with Facebook on third party sites, so it would be understandable for the jobseeker to click that link.
When you enter the credentials and click on “Log In”, it will take a while and then you’ll be notified that “The password you’ve entered is incorrect. Please try again!”
This login page is also the part that makes this attack a very sophisticated one. The phishers use a websocket method that allows them to intercept submissions live as they are entered. This allows them to try the credentials and if your password works, they can log into your real Facebook account within seconds. They could potentially ask for multi-factor authentication (MFA) confirmation if that’s necessary, too.
Imagine that the phisher can instantly see the credentials you submitted, tests them at the real Facebook login page, and subsequently sends you the appropriate response. (In my case “wrong password” since I had no intention of feeding them valid credentials.)
You’d have no idea that they were accessing your Facebook account and they’d have bought some time to log you out, spam your friends, or whatever else they wanted to do with your account.
We often see phishing campaigns like these that are explicitly designed to steal the credentials of marketing managers, social media staff, and especially those who have access to company Facebook Pages or business accounts.
Compromising a business account can allow attackers to run malicious ads using the company’s payment methods, demand a ransom for return of control over the account, or use the company’s reputation to spread more scams.
What to do
If you suspect your credentials may have been compromised, immediately change your passwords, enable multi-factor authentication, and notify your IT/security team if you have one.
You can stay safe from these attacks by:
- Be super cautious at engaging in job offers that you have not applied for.
- Carefully check the URLs, both in the email and on the website, before you click them (did you notice the missing “i” in the domain name?)
- Check if the address in the browser bar matches what you expect to see, along with the content of the website.
- Learn how to spot and recognize phishing attempts. Phishing mails are getting harder to identify now that cybercriminals are using Artificial Intelligence (AI).
- Keep your browser, your Operating System, and other software up to date.
- Use an up-to-date real-time anti-malware solution with web protection.
Since the phishing campaign was hosted behind Cloudflare’s services, we have notified Netflix and Cloudflare about this campaign.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
