Security researchers at Palo Alto Networks Unit 42 have identified a newly emerging ransomware family, 01flip, that represents a significant shift in malware development tactics.
Discovered in June 2025, this sophisticated threat is entirely written in Rust a modern programming language that enables cross-platform compatibility and currently targets a limited set of victims across the Asia-Pacific region.
The discovery underscores the growing trend of cybercriminals adopting advanced programming languages to expand their operational reach across diverse systems and platforms.
Unit 42 researchers first identified 01flip ransomware when investigating a suspicious Windows executable that demonstrated ransomware-like behavior in sandbox testing environments.
The executable’s nomenclature derives from two distinct artifacts: the file extension appended to encrypted files (.01flip) and the contact email address (01Flip@proton[.]me) included in ransom notes.
The threat actor responsible for this campaign is currently tracked as CL-CRI-1036, representing a cluster of financially motivated cybercriminal activity linked to alleged data exfiltration operations.
Subsequent investigation revealed a Linux variant of 01flip, which remained undetected by antivirus platforms for approximately three months after initial submission to VirusTotal.
This extended detection evasion period highlights the effectiveness of Rust-compiled malware in evading conventional security detection mechanisms.
Observed victims include organizations managing critical infrastructure in Southeast Asia, with suspected compromises in the Philippines and Taiwan based on threat actor communications discovered on dark web forums.
Technical Architecture and Capabilities
The 01flip ransomware demonstrates sophisticated multi-platform functionality through leveraging Rust’s cross-compilation capabilities.
Both Windows and Linux variants share substantially identical core functionality, utilizing the same dependencies and library versions with only minor architecture-specific variations.
The ransomware implements several key operational capabilities: comprehensive drive enumeration, mass ransom note creation across accessible directories, file encryption using AES-128-CBC algorithms combined with RSA-2048 key encryption, and automated self-deletion procedures to remove forensic evidence.
The malware employs defense evasion techniques including the use of low-level APIs and system calls that blend seamlessly with legitimate operating system activity.
Additionally, critical strings within the ransomware binary including ransom note content, extension lists, and RSA public keys are encoded and decrypted only at runtime.
Both variants implement anti-sandbox mechanisms, with samples containing the filename string “01flip” proceeding directly to indicator removal without executing file encryption routines.
The threat actors conducting these campaigns gained initial access by exploiting older vulnerabilities, including CVE-2019-11580, against internet-facing applications beginning in April 2025.
Following successful compromise, attackers deployed Sliver, a publicly available cross-platform adversary emulation framework written in Go, to establish persistent network access.
The threat actors subsequently performed lateral movement across network infrastructure before deploying multiple 01flip ransomware instances to both Windows and Linux systems in late May 2025.
Possible Threat Actor Overlap
During technical analysis, researchers discovered a “lockbit” extension in 01flip’s file encryption exclusion list an unusual artifact suggesting potential overlap between CL-CRI-1036 operators and the LockBit ransomware group tracked as Flighty Scorpius.
Ransom notes contain contact information and cipher data that is required to obtain a key to decrypt a victim’s files.
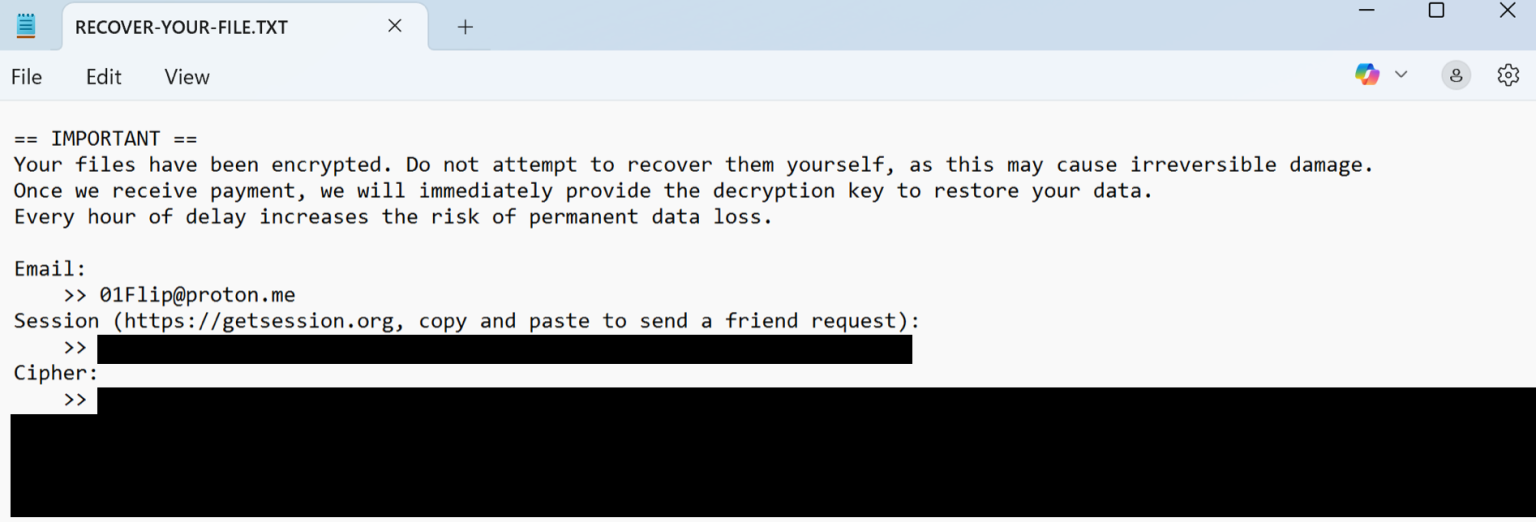
However, no substantive technical connections between the two ransomware families have been identified beyond this anomaly, and further investigation is required to establish any operational relationships definitively.
Organizations should implement comprehensive endpoint detection and response solutions capable of identifying Rust-compiled malware behaviors and monitor for indicators associated with CL-CRI-1036 activity.
Palo Alto Networks customers benefit from protection through Advanced WildFire, Cortex XDR, XSIAM, and Cortex Xpanse platforms.
Organizations suspecting compromise should contact specialized incident response teams immediately for threat investigation and remediation assistance.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
