A previously unknown cyber espionage hacking group named ‘AeroBlade’ was discovered targeting organizations in the United States aerospace sector.
The campaign, discovered by BlackBerry, unfolded in two phases: a testing wave in September 2022 and a more advanced attack in July 2023.
The attacks employ spear-phishing with weaponized documents to achieve initial access to corporate networks, dropping a reverse-shell payload capable of file listing and data theft.
BlackBerry assesses with mid to high confidence that the goal of the attacks was commercial cyber espionage, aiming to gather valuable information.
Campaign details
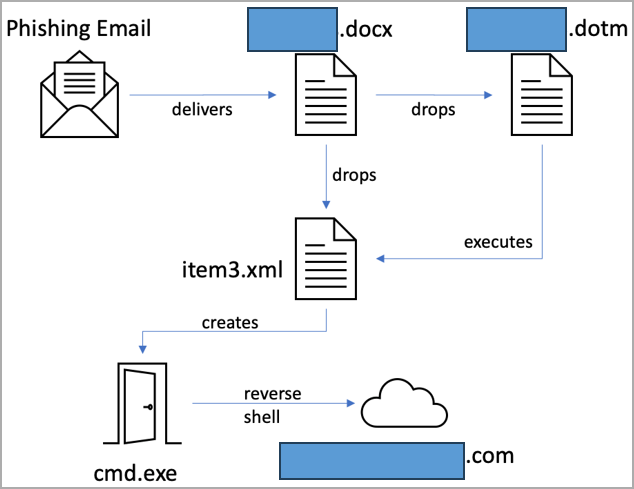
The first attacks attributed to AeroBlade occurred in September 2022, using phishing emails with a document (docx) attachment that employs remote template injection to download the second-stage DOTM file.
The second stage executes malicious macros that create a reverse shell on the target’s system, which connects to the attacker’s command and control (C2) server.
Source: BlackBerry
“Once the victim opens the file and executes it by manually clicking the “Enable Content” lure message, the [redacted].dotm document discretely drops a new file to the system and opens it,” explains BlackBerry.
“The newly downloaded document is readable, leading the victim to believe that the file initially received by email is legitimate.”
Source: BlackBerry
The reverse shell payload is a heavily obfuscated DLL that lists all directories on the compromised computer to aid its operators in planning their next steps in data theft.
The DLL file features anti-analysis mechanisms, including sandbox detection, custom string encoding, disassembly protection via dead code and control flow obfuscation, and API hashing to mask Windows function abuse.
The payload also establishes persistence on the system via the Windows Task Scheduler, adding a task named ‘WinUpdate2,’ so foothold on breached devices survives system reboot.
Early samples of the DLL payload missed most evasion mechanisms seen in the 2023 samples and the ability to list directories and exfiltrate data.
This indicates that the threat actors continue evolving their tools for more sophisticated attacks, while the 2022 attempts focused more on testing the intrusion and infection chain.
In both attacks, the final payload was a reverse shell connecting to the same C2 IP address, and the threat actors used the same lure documents in the phishing stage.
BlackBerry has been unable to determine the origin of AeroBlade or the precise objective of the attacks.
The researchers speculate that the intent was to steal data to sell it, provide it to international aerospace competitors, or use the information as leverage for extortion against victims.
