A sophisticated new Android banking Trojan named Herodotus has emerged as a significant threat to mobile users, introducing a novel approach that deliberately mimics human typing patterns to evade behavioral biometrics detection systems.
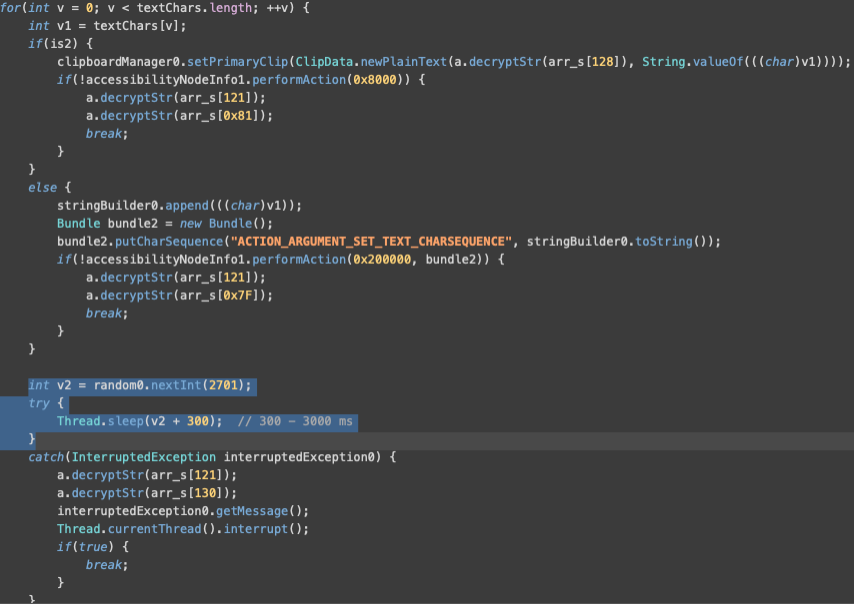
The malware’s sophisticated approach to avoiding detection marks it apart from conventional banking Trojans, incorporating randomized time intervals between text inputs—ranging from 300 to 3,000 milliseconds—to simulate authentic user behavior.
Discovered by ThreatFabric’s Mobile Threat Intelligence team during routine monitoring of malicious distribution infrastructure, Herodotus represents a concerning evolution in Device-Takeover attacks, now available as a Malware-as-a-Service offering under development by threat actor “K1R0.”
This deliberate humanization of automated actions suggests that cybercriminals are actively working to circumvent increasingly intelligent fraud detection systems that analyze behavioral patterns and keystroke dynamics.
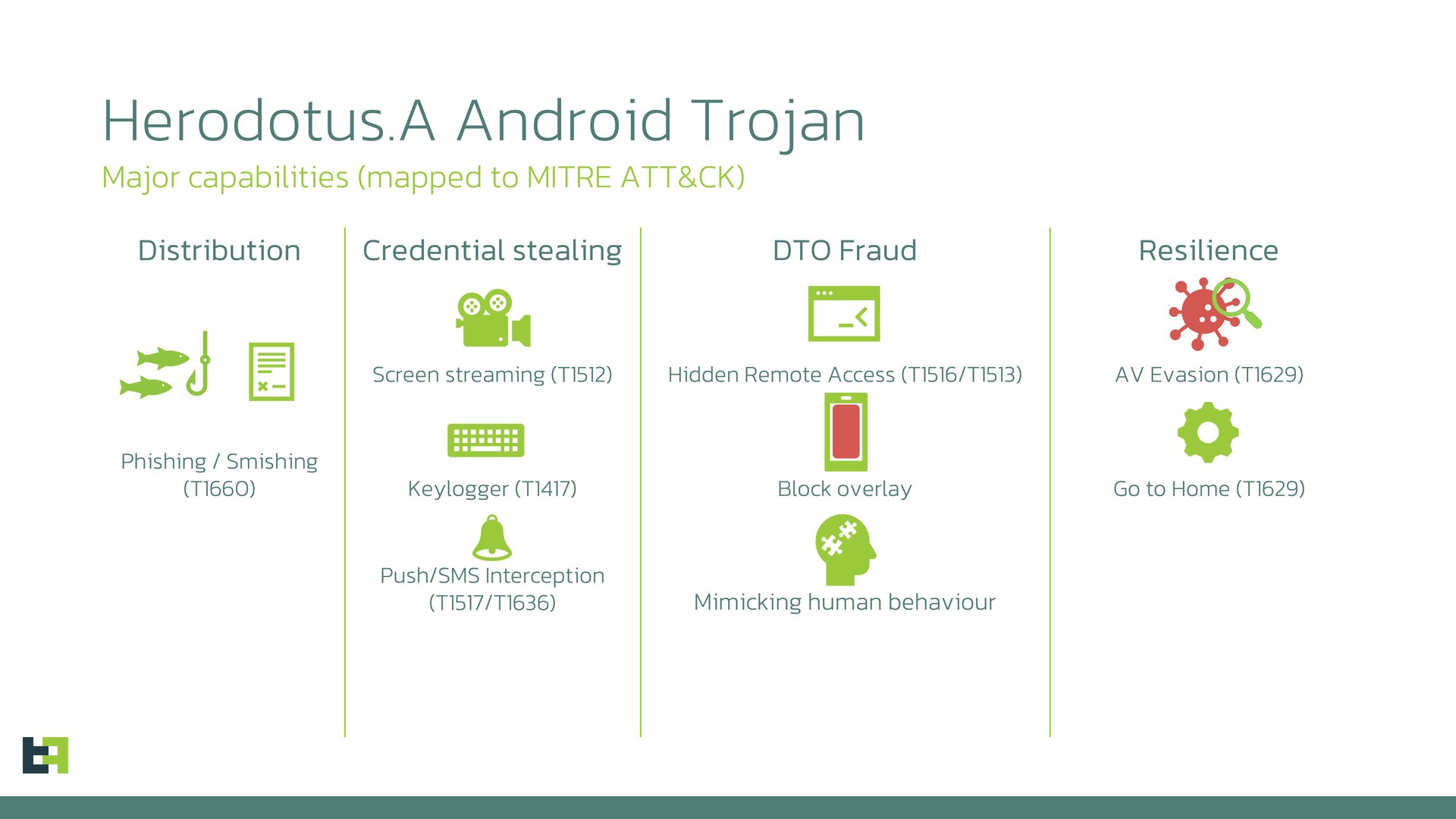
Herodotus operates through a multi-stage infection chain beginning with SMiShing campaigns distributing dropper applications.
Once installed, the malware requests Accessibility Service permissions by displaying fake loading screens that obscure the actual permission grants from users.
After gaining these elevated privileges, the Trojan collects installed packages and communicates with its command-and-control infrastructure via MQTT protocol to receive targeting instructions and overlay pages for credential harvesting.
What distinguishes Herodotus from existing banking malware is its conscious effort to appear human during remote control sessions.
Rather than using rapid automated input or direct text-setting methods that behavioral analytics engines can easily identify as machine-generated, Herodotus splits text inputs into individual characters and introduces randomized delays between each keystroke.
This sophisticated technique directly targets behavior-based anti-fraud solutions that measure input timing as an indicator of Device-Takeover attacks.
The malware operators access a control panel featuring specific buttons labeled “SEND 1” and “SEND 2” with a “Delayed text” checkbox, giving them granular control over whether inputs appear human-like or automated.
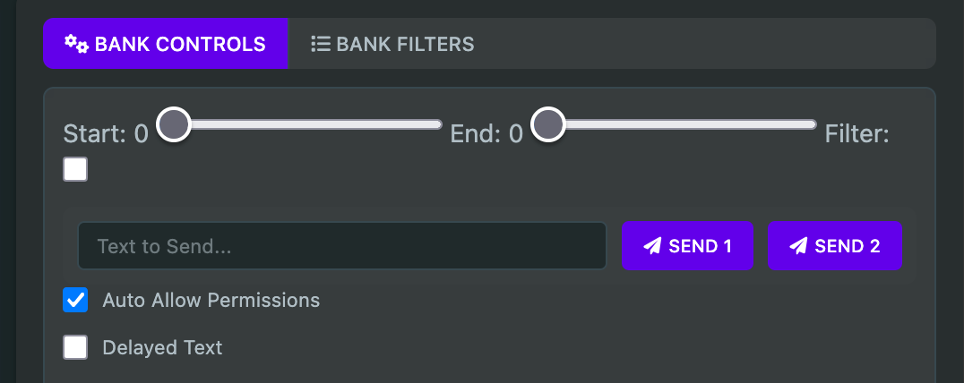

This deliberate feature demonstrates the developers’ understanding of how modern fraud detection systems operate and their commitment to bypassing them.
Global Campaigns and Technical Heritage
Mobile Threat Intelligence researchers observed active Herodotus campaigns targeting users in Italy and Brazil, with the Italian variant masquerading as “Banca Sicura” and the Brazilian iteration posing as a security module for the Stone payment acquirer.
Delay specified is in range of 300 – 3000 milliseconds (0,3 – 3 seconds). Such a randomisation of delay between text input events does align with how a user would input text.

Researchers also discovered overlay pages targeting financial organizations in the United States, Turkey, the United Kingdom, Poland, as well as cryptocurrency platforms, suggesting widespread campaign preparation.
Analysis reveals significant technical connections to Brokewell, another banking malware discovered in April 2024.
Herodotus incorporates Brokewell’s string encryption techniques and dynamically loads modules from the predecessor malware, invoking specific methods for element clicking and coordinate-based interactions.
However, the current implementation cannot fully leverage Brokewell’s broader capabilities, indicating that Herodotus developers may possess access to partial source code rather than complete codebases.
Implications for Financial Security
The emergence of Herodotus underscores a critical vulnerability in fraud detection strategies relying primarily on interaction tempo and keystroke cadence analysis.
While behavioral biometrics remain valuable components of security architecture, this malware demonstrates that such defenses cannot operate in isolation.
Financial institutions must adopt layered detection approaches that analyze not only user behavior patterns but also device environment indicators, enabling systems to identify compromised devices regardless of how convincingly malware operators manipulate interaction patterns.
As Herodotus continues active development and expands its global presence through Malware-as-a-Service channels, organizations must evolve their threat detection capabilities to stay ahead of increasingly sophisticated adversaries.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
