A new Android malware posing as an antivirus tool software created by Russia’s Federal Security Services agency (FSB) is being used to target executives of Russian businesses.
In a new report from Russian mobile security firm Dr. Web, researchers track the new spyware as ‘Android.Backdoor.916.origin,’ finding no links to known malware families.
Among its various capabilities, the malware can snoop on conversations, stream from the phone’s camera, log user input with a keylogger, or exfiltrate communication data from messenger apps.
Dr. Web reports that, since the initial discovery of this malware in January 2025, it has sampled multiple subsequent versions, indicating continuous development.
Based on the distribution lures, infection methods, and the fact that its interface only offers the Russian language option, the researchers believe it was designed for targeted attacks against Russian businesses.
Dr. Web has seen two main branding attempts, one named “GuardCB,” impersonating the Central Bank of the Russian Federation, and two variants named “SECURITY_FSB” and “ФСБ” (FSB), supposedly attempting to impersonate software from the Russian intelligence agency.
“At the same time, its interface provides only one language – Russian. That is, the malicious program is entirely focused on Russian users,” reports Dr. Web.
“This is confirmed by other detected modifications with file names such as “SECURITY_FSB”, “FSB” and others, which cybercriminals are trying to pass off as security programs allegedly related to Russian law enforcement agencies.”
Although the antivirus tool lacks security-related features, it attempts to mimic a genuine security tool to prevent the victim from removing it from their device.
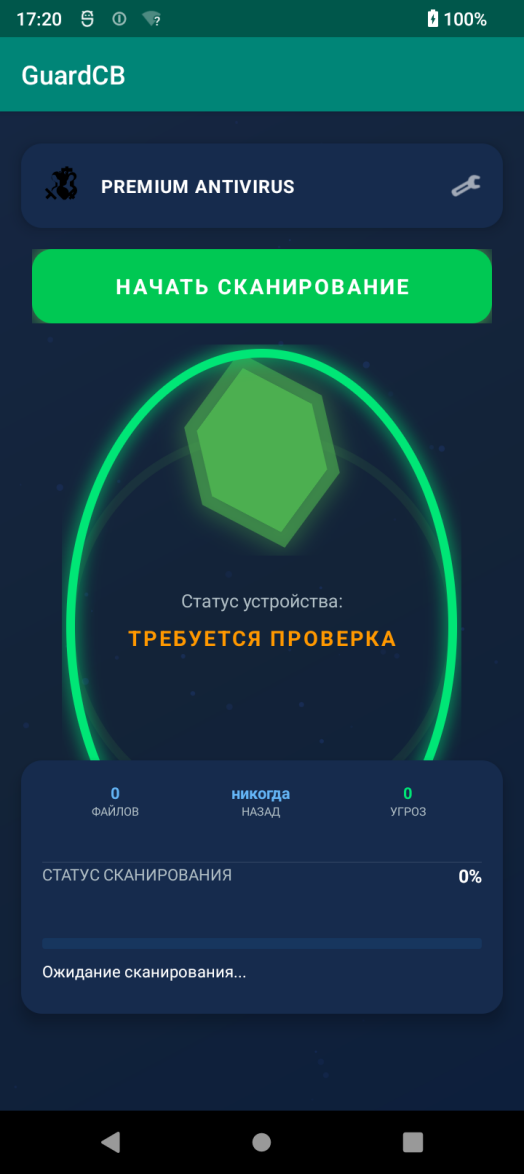
Source: Dr. Web
When the user clicks on ‘scan,’ the interface displays a simulation programmed to return a fake positive result in 30% of the time, with the number of fake detections ranging (randomly) between 1 and 3.
Upon installation, the malware requests granting several high-risk permissions like geo-location, access to SMS and media files, camera and audio recording, Accessibility Service, and permission to run in the background at all times.
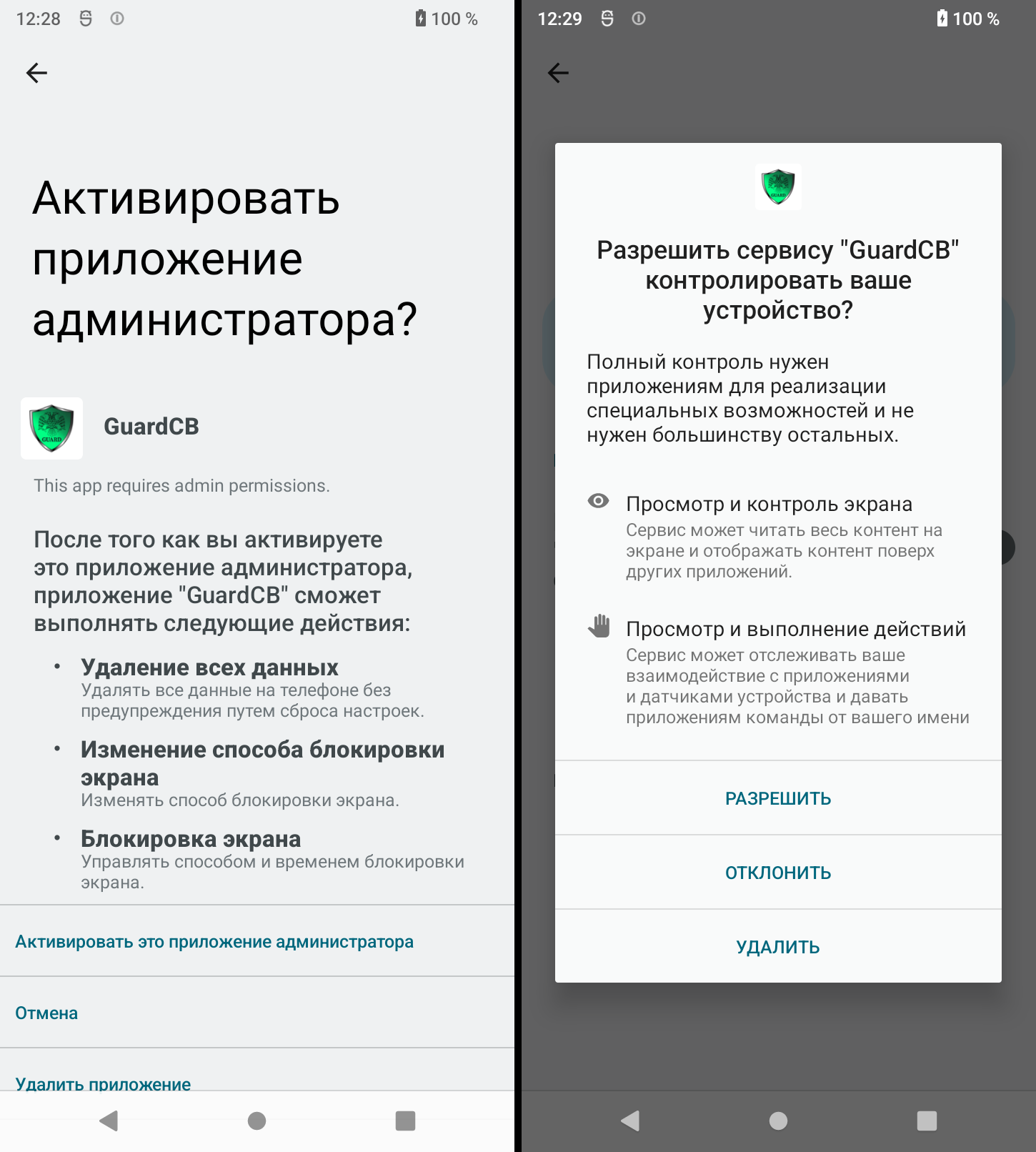
Source: Dr. Web
Next, it launches multiple services through which it connects to the command and control (C2) to receive commands such as:
- Exfiltrate SMS, contacts, call history, geo-location, and stored images
- Activate the microphone, camera, and screen streaming
- Capture text input and messenger or browser content (Telegram, WhatsApp, Gmail, Chrome, Yandex apps)
- Execute shell commands, maintain persistence, and enable self-protection
Dr. Web found that the malware can switch between up to 15 hosting providers, and though this function isn’t currently active, it shows the malware is designed for resilience.
The analysts shared the complete indicators of compromise related to Android.Backdoor.916.origin on this GitHub repository.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.