A new malware-as-a-service (MaaS) platform named ‘SuperCard X’ has emerged, targeting Android devices via NFC relay attacks that enable point-of-sale and ATM transactions using compromised payment card data.
SuperCard X is linked to Chinese-speaking threat actors and shows code similarities with the open-source project NFCGate and its malicious spawn, NGate, which has facilitated attacks in Europe since last year.
The malware-as-a-service platform is promoted through Telegram channels that also offer direct support to “customers.”
SuperCard X was discovered by mobile security firm Cleafy, which reports seeing attacks utilizing this Android malware in Italy. These attacks involved multiple samples with subtle differences, indicating that affiliates are offered the option of custom builds tailored to regional or other specific needs.
How SuperCard X attacks unfold
The attack begins with the victim receiving a fake SMS or WhatsApp message impersonating their bank, claiming they need to call a number to resolve issues caused by a suspicious transaction.
The call is answered by a scammer posing as bank support, who uses social engineering to trick the victim into “confirming” their card number and PIN. They then attempt to convince the user to remove spending limits via their banking app.
Finally, the threat actors convince users to install a malicious app (Reader) disguised as a security or verification tool that contains the SuperCard X malware.
Upon installation, the Reader app requests only minimal permissions, mainly access to the NFC module, which is enough to perform the data theft.
The scammer instructs the victim to tap their payment card to their phone to verify their cards, allowing the malware to read the card chip data and send it to the attackers.
The attackers receive this data on their Android device, which runs another app called Tapper, which emulates the victim’s card using the stolen data.
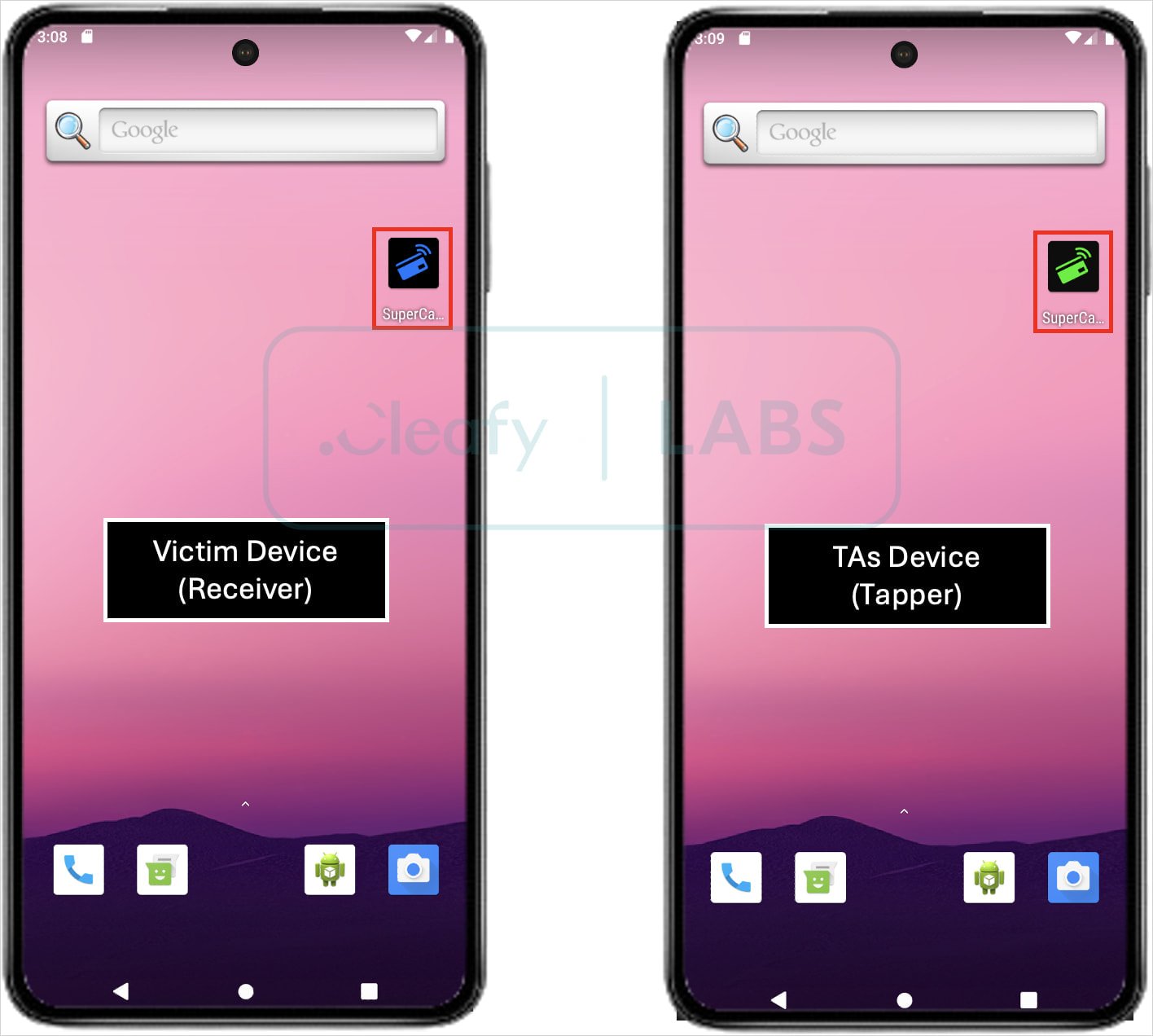
Source: Cleafy
These ’emulated’ cards allow attackers to make contactless payments at stores and ATM withdrawals, though amount limits apply. As these small transactions are instant and appear legitimate to the banks, they’re harder to flag and reverse.
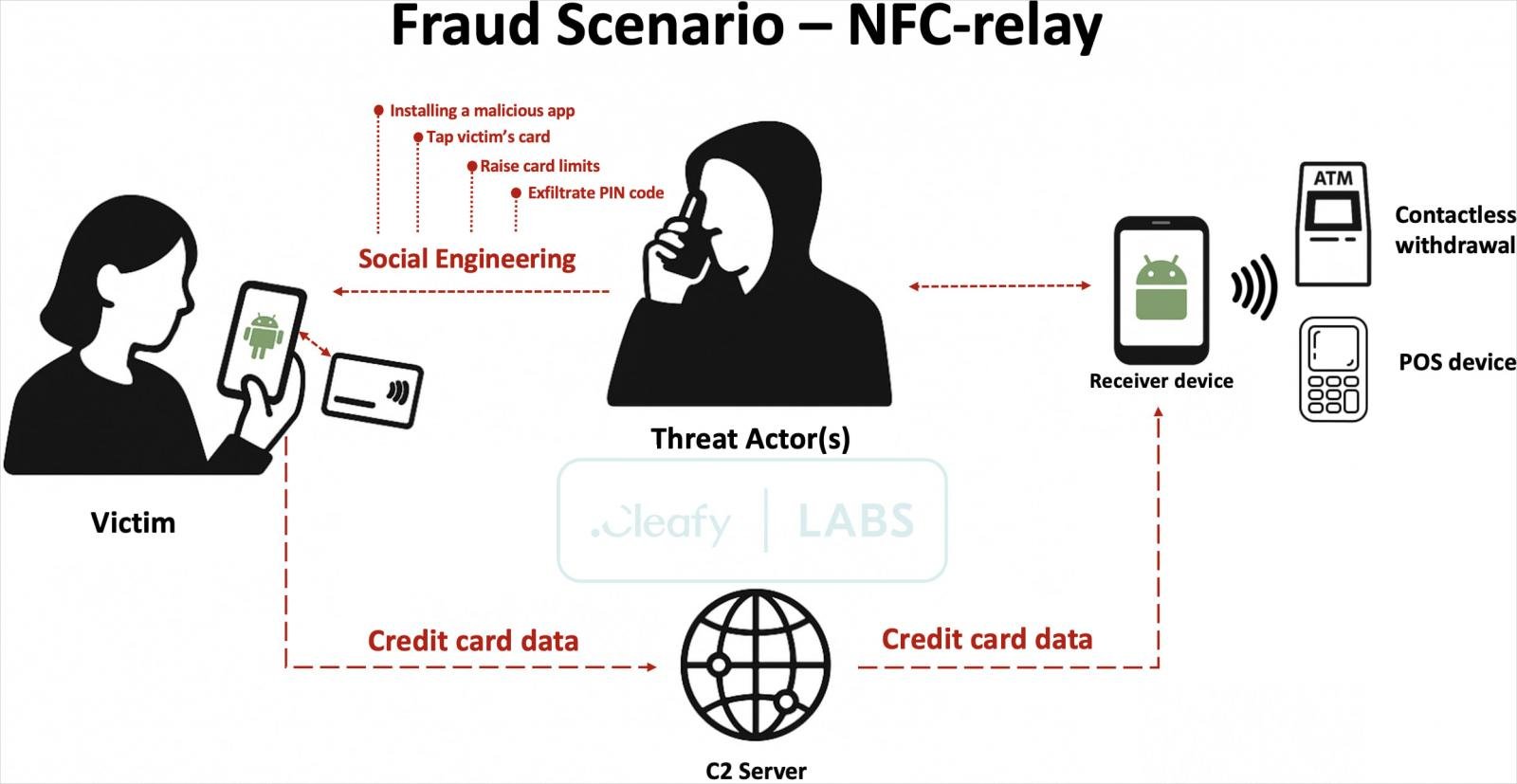
Source: Cleafy
Evasive malware
Cleafy notes that SuperCard X is currently not flagged by any antivirus engines on VirusTotal and the absence of risky permission requests and aggressive attack features like screen overlaying ensures it stays off the radar of heuristic scans.
The emulation of the card is ATR-based (Answer to Reset), which makes the card appear legitimate to payment terminals and shows technical maturity and understanding of smartcard protocols.
Another notable technical aspect is the use of mutual TLS (mTLS) for certificate-based client/server authentication, securing C2 communications from interception and analysis by researchers or law enforcement.
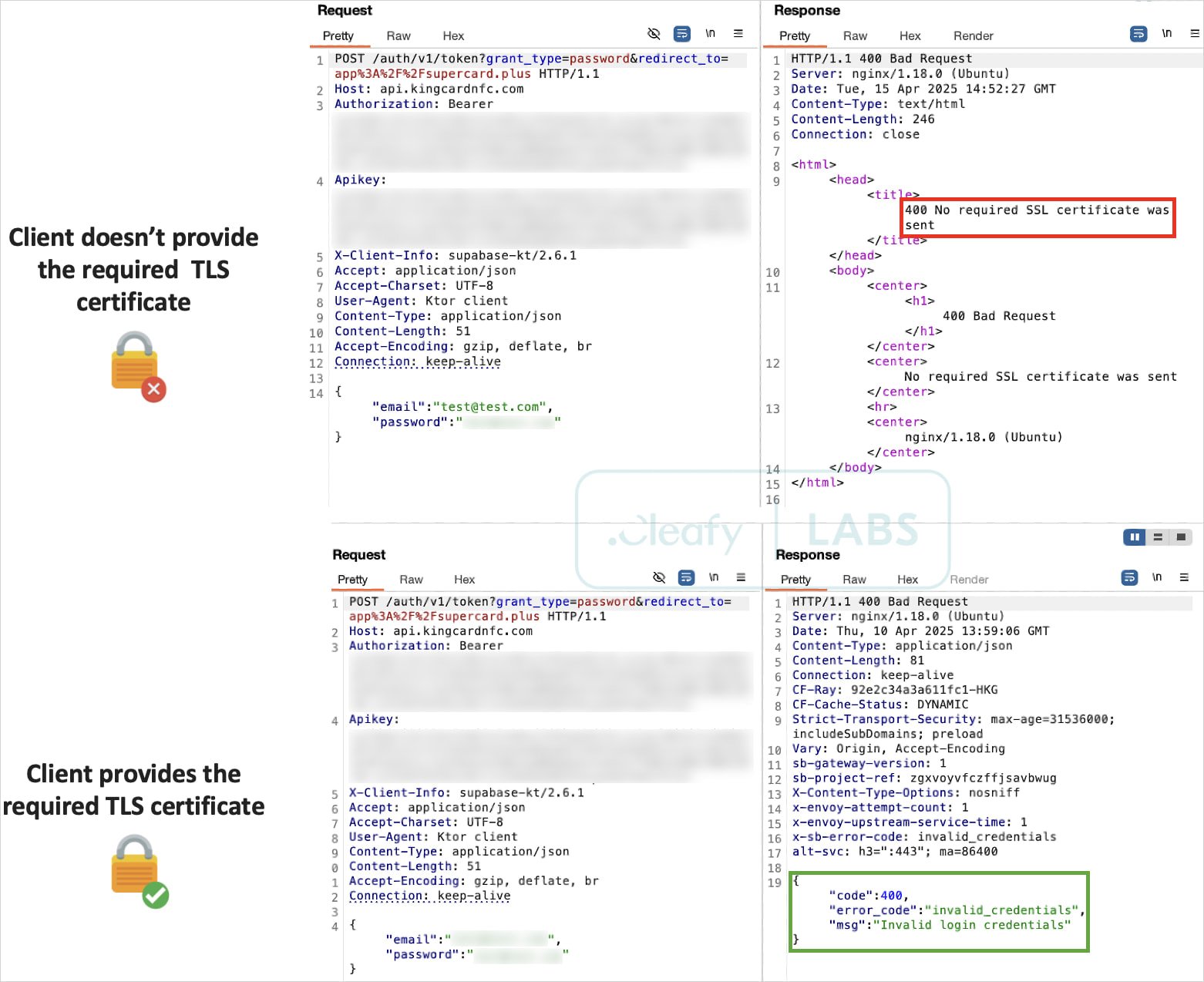
Source: Cleafy
BleepingComputer contacted Google to comment on the SuperCard X activity and a spokesperson sent the below statement.
“Based on our current detection, no apps containing this malware are found on Google Play. Android users are automatically protected by Google Play Protect, which is on by default on Android devices with Google Play Services. Google Play Protect can warn users or block apps known to exhibit malicious behavior, even when those apps come from sources outside of Play.” – A Google spokesperson
