A newly discovered information-stealing malware called Arcane is stealing extensive user data, including VPN account credentials, gaming clients, messaging apps, and information stored in web browsers.
According to Kaspersky, the malware has no links or code that overlaps with the Arcane Stealer V, which has been circulating on the dark web for years.
The Arcane malware campaign started in November 2024, having gone through several evolutionary steps, including primary payload replacements.
All conversations and public posts by its operators are in Russian, with Kaspersky’s telemetry showing that most Arcane infections are in Russia, Belarus, and Kazakhstan.
This is particularly notable, as most threat actors based in Russia typically avoid targeting users within the country and other CIS nations to prevent conflicts with local authorities.
Arcane stealer infection chain
The campaign distributing Arcane Stealer relies on YouTube videos promoting game cheats and cracks, tricking users into following a link to download a password-protected archive.
These files contained a heavily obfuscated ‘start.bat’ script that fetched a second password-protected archive with malicious executables.
The downloaded files add an exclusion to Windows Defender’s SmartScreen filter for all drive root folders or turn it off completely through Windows Registry modifications.
.jpg)
Source: Kaspersky
Previously, the attacks used another stealer malware family called VGS, a rebranded version of the Phemedrone trojan, but they switched to Arcane in November 2024.
Kaspersky also found recent changes in the distribution method, including the use of a fake software downloader, supposedly for popular game cracks and cheats, named ArcanaLoader.
ArcanaLoader has been heavily promoted on YouTube and Discord, with the operators even inviting content creators to promote it on their blogs/videos for a fee.
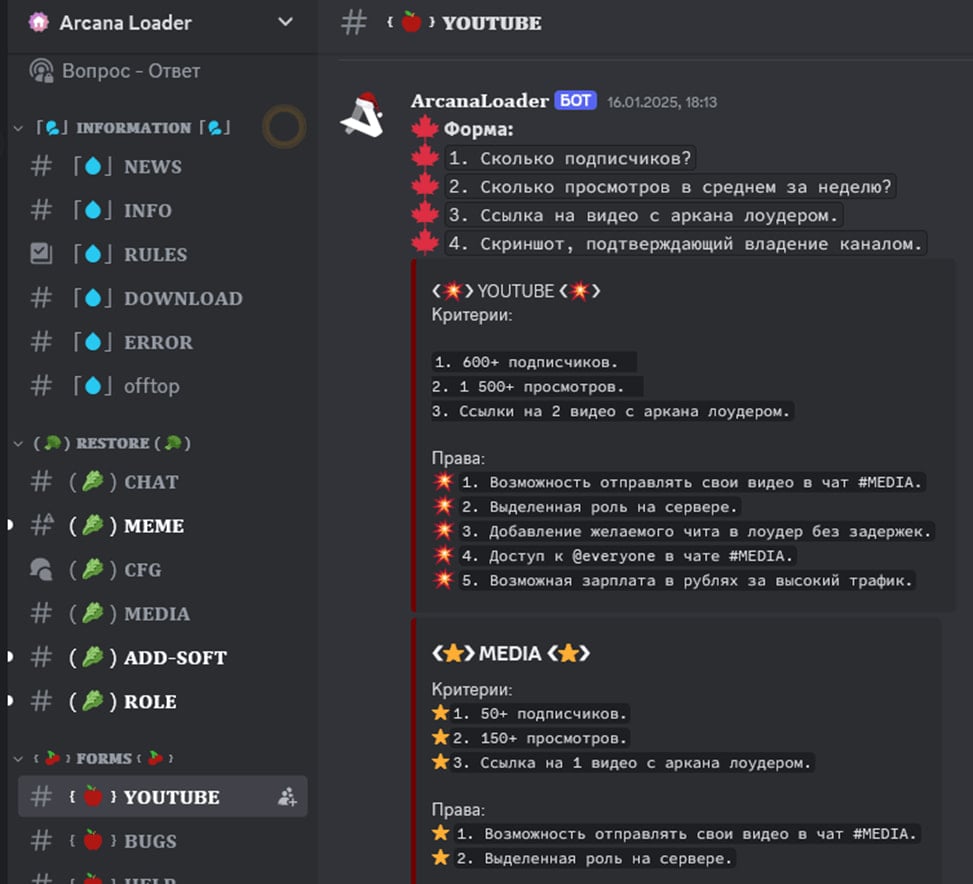
Source: Kaspersky
Stealing a ton of data
Kaspersky comments that Arcane’s broad data theft makes it stand out in the populous infostealer space.
First, it profiles the infected system, stealing hardware and software details such as OS version, CPU and GPU details, installed antivirus, and browsers.
The current version of the malware targets account data, settings, and configuration files from the following apps:
- VPN clients: OpenVPN, Mullvad, NordVPN, IPVanish, Surfshark, Proton, hidemy.name, PIA, CyberGhost, ExpressVPN
- Network tools: ngrok, Playit, Cyberduck, FileZilla, DynDNS
- Messagers: ICQ, Tox, Skype, Pidgin, Signal, Element, Discord, Telegram, Jabber, Viber
- Email clients: Outlook
- Gaming clients: Riot Client, Epic, Steam, Ubisoft Connect (ex-Uplay), Roblox, Battle.net, various Minecraft clients
- Cryptocurrency wallets: Zcash, Armory, Bytecoin, Jaxx, Exodus, Ethereum, Electrum, Atomic, Guarda, Coinomi
- Web browsers: Saved logins, passwords, and cookies (for Gmail, Google Drive, Google Photos, Steam, YouTube, Twitter, Roblox) from Chromium-based browsers.
Arcane also captures screenshots that can reveal sensitive information about what you are doing on the computer and retrieves saved Wi-Fi network passwords.
Even though Arcane currently has specific targeting, its operators could expand it to cover additional countries or themes.
Becoming infected with an infostealer is devastating, leading to financial fraud, extortion, and future attacks. Cleaning up after these attacks is a massive time sink as you need to change the passwords on every website and application you use and ensure they are not compromised.
Therefore, users should always keep in mind the risks of downloading unsigned pirate and cheat tools. The risk from these tools is too high, and they should be avoided entirely.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.
