A previously undocumented Linux backdoor dubbed ‘Auto-Color’ was observed in attacks between November and December 2024, targeting universities and government organizations in North America and Asia.
According to Palo Alto Networks’ Unit 42 researchers who discovered the malware, it is highly evasive and difficult to remove from infected systems, capable of maintaining access for extended periods.
The malware features some similarities with the Symbiote Linux malware family, which was first documented by BlackBerry in 2022, but the two are distinct from each other.
Evasive Linux threat
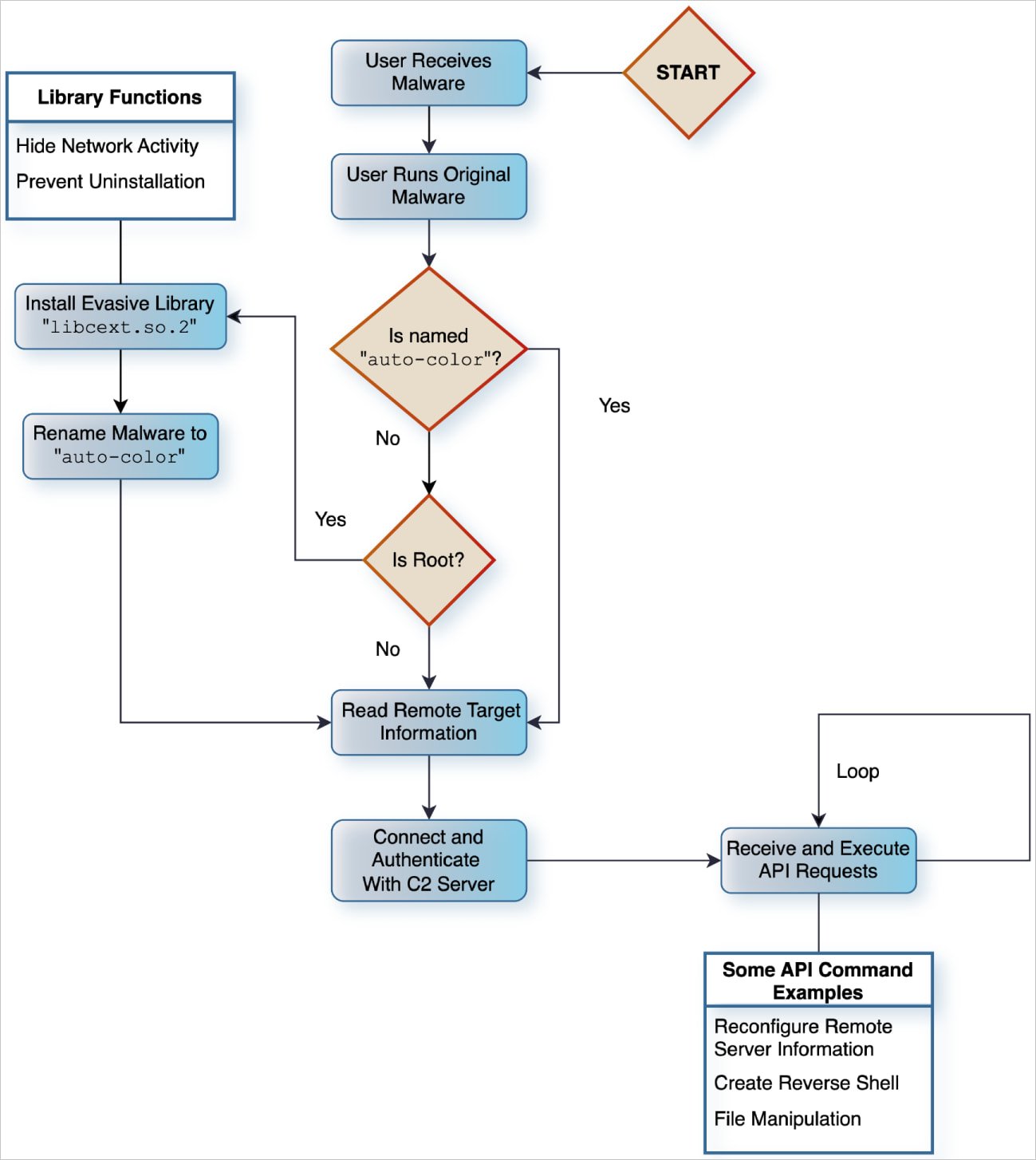
Unit 42 does not have visibility into the initial infection vector, but the attack begins with the execution of a file disguised with benign names like”door”, “egg”, and “log.”
If the malware runs with root privileges, it installs a malicious library implant (libcext.so.2), disguised as the legitimate libcext.so.0 library, copies itself to a system directory (/var/log/cross/auto-color), and modifies ‘/etc/ld.preload’ to ensure the implant executes before any other system library.
If root access isn’t available, the malware still executes but skips the persistent mechanisms. Although this limits its long-term impact, it still provides remote access to threat actors who may be able to achieve root through other means.
Source: Unit 42
Auto-Color decrypts command-and-control (C2) server information using a custom encryption algorithm and validates the exchange via a random 16-byte value handshake.
Custom encryption is used for obfuscation of C2 server addresses, configuration data, and network traffic, while the encryption key changes dynamically with each request to make detection more difficult.
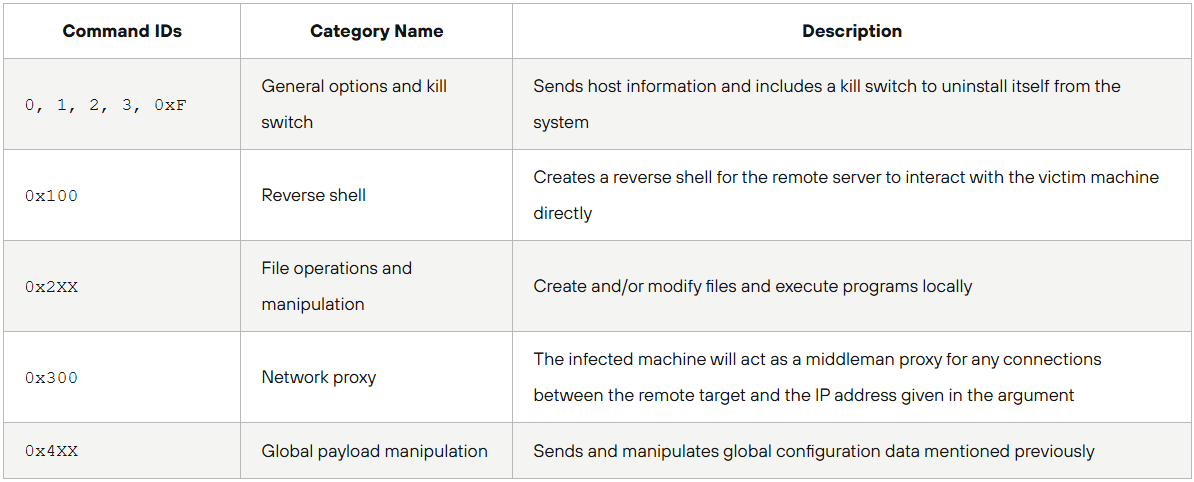
Once the connection has been established, the C2 may order Auto-Color to perform one of the following actions:
- Open a reverse shell, allowing the operators full remote access.
- Execute arbitrary commands on the system.
- Modify or create files to expand the infection.
- Act as a proxy, forwarding attacker traffic.
- Modify its configuration dynamically.
Source: Unit 42
Auto-Color also has rootkit-like features like hooking libc functions to intercept system calls, which it uses to hide C2 connections by modifying the /proc/net/tcp file.
Unit 42 says Auto-Color also features a built-in “kill switch,” which allows the attackers to immediately delete infection traces from the compromised machines to impede investigations.
How to defend
Given its stealth, modular design, and remote control features, Auto-Color is a serious threat to Linux systems, particularly those in government and academic environments targeted in the observed attacks.
Unit 42 suggests monitoring changes to ‘/etc/ld.preload,’ which is a key persistence mechanism, checking ‘/proc/net/tcp’ for output anomalies, and using behavior-based threat detection solutions.
The researchers have also listed indicators of compromise (IoCs) at the bottom of the report, so inspecting system logs and network traffic for connections to the listed C2 IPs is also crucial.
