Securonix threat researchers have uncovered a stealthy malware campaign, tracked as PHALT#BLYX, targeting the hospitality sector with a sophisticated “ClickFix” social engineering tactic.
This ongoing campaign specifically targets European organizations during the busy holiday season, utilizing fake Booking.com reservation cancellations to deploy a Russian-linked DCRat payload.
The infection chain begins with a targeted phishing email masquerading as official correspondence from Booking.com.
The emails alert recipients to a reservation cancellation involving a significant financial charge, often exceeding €1,000, to create panic and urgency.
When the victim clicks the “See Details” link, they are redirected through an intermediate site to a fraudulent landing page that perfectly mimics the Booking.com interface.
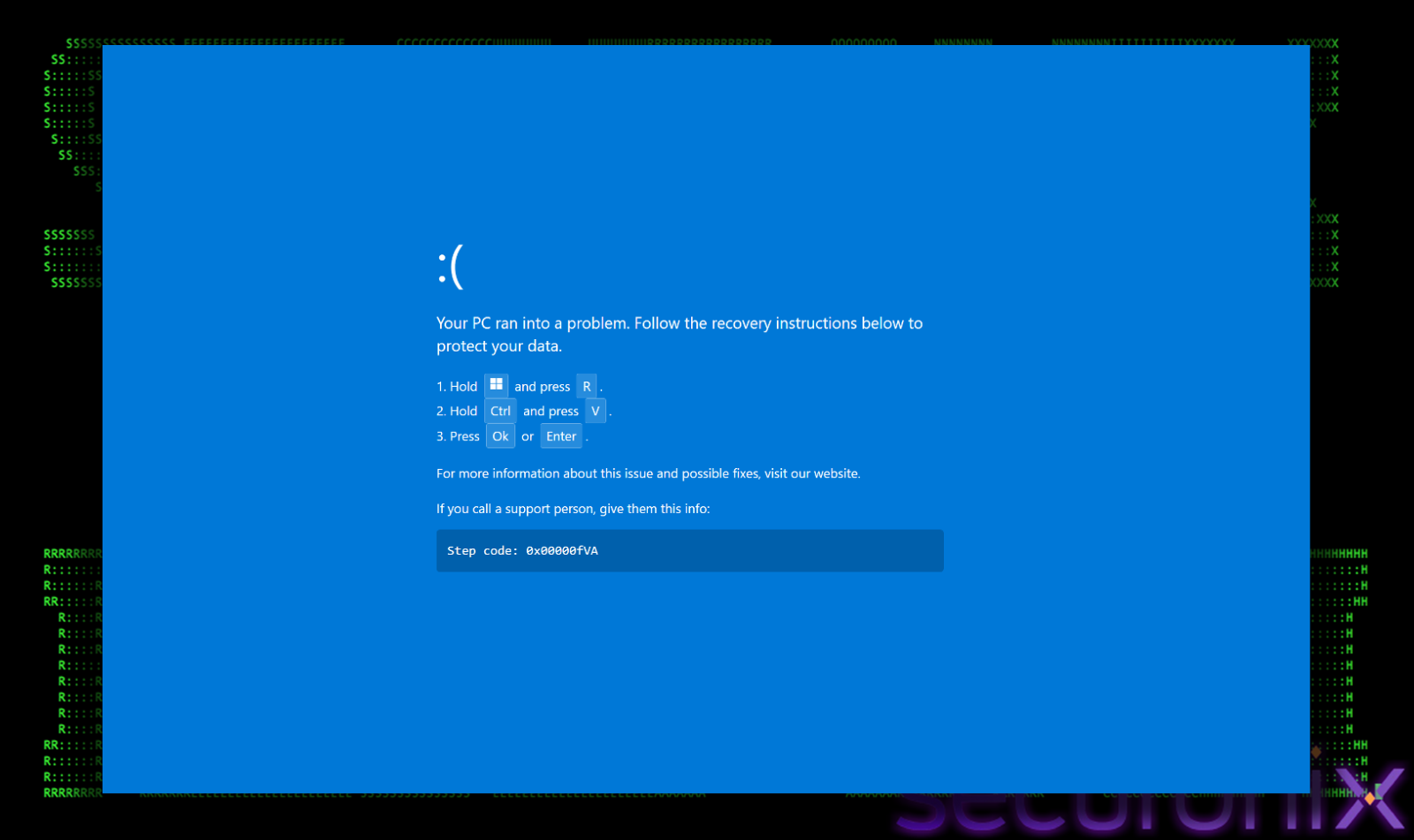
Rather than displaying reservation details, the page presents a fake “Loading is taking too long” error. If the user clicks “Refresh,” the browser simulates a full-screen BSOD crash, designed to shock the victim.
A deceptive overlay then instructs the user to perform a “fix” by pressing specific key combinations (Windows Key + R, then Ctrl + V).
Unknowingly, the victim pastes a malicious PowerShell script into the Windows Run dialog, initiating the infection without triggering automated email security filters.
The attack chain is noted for its use of the “Blue Screen of Death” (BSOD) deception and abuse of the legitimate Windows tool MSBuild.exe to bypass security defenses.
MSBuild Abuse and Russian Origins
Once executed, the PowerShell script downloads an MSBuild project file named v.proj. Unlike earlier campaigns that relied on easily detected HTML Application (.hta) files, this attack leverages “Living off the Land” techniques.
The attackers use the trusted Microsoft Build Engine (MSBuild.exe) to compile and execute the malicious code embedded within the project file. This method frequently bypasses application allowlisting and standard antivirus detection.
The malware immediately attempts to blind Windows Defender by adding exclusions for the ProgramData directory. It then establishes persistence by creating an Internet Shortcut (.url) file in the Startup folder, masquerading as a cleanup script named “DeleteApp.”
The final payload is a heavily obfuscated version of DCRat (AsyncRAT), capable of process hollowing, keylogging, and deploying secondary payloads. The RAT is injected into the legitimate aspnet_compiler.exe process to mask its activity.
Researchers found Cyrillic debug strings within the v.proj file, such as “Installation successfully completed” in Russian, linking the activity to Russian threat actors.
The use of DCRat, a commodity malware widespread in Russian underground forums, further supports this attribution.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.





