A new malicious campaign mixes the ClickFix method with fake CAPTCHA and a signed Microsoft Application Virtualization (App-V) script to ultimately deliver the Amatera infostealing malware.
The Microsoft App-V script acts as a living-off-the-land binary that proxies the execution of PowerShell through a trusted Microsoft component to disguise the malicious activity.
Microsoft Application Virtualization is an enterprise Windows feature that allows applications to be packaged and run in isolated virtual environments without being actually installed on the system.

While App-V scripts have been leveraged in the past to evade security solutions, this is the first time this type of file has been observed in ClickFix attacks that deliver an information stealer.
According to BlackPoint Cyber, a company providing threat hunting, detection, and response services, the attack begins with a fake CAPTCHA human verification check that instructs the victim to manually paste and execute a command via the Windows Run dialog.
.jpg)
Source: BlackPoint
The pasted command abuses the legitimate SyncAppvPublishingServer.vbs App-V script that is typically used to publish and manage virtualized enterprise applications.
The script is executed using the trusted wscript.exe binary and launches PowerShell.
During the initial stage, the command verifies that the user executed it manually, that the execution order went as expected, and that the clipboard contents remained unchanged, to ensure that the malware loader does not run on sandbox machines.
BlackPoint Cyber researchers say that if an analysis environment is detected, the execution silently stalls using infinite waits, possibly to waste automated analysis resources.
When the conditions are met, the malware retrieves configuration data from a public Google Calendar file that contains base64-encoded configuration values in a specific event.
In the later stages of the attack, a 32-bit hidden PowerShell process is spawned via the Windows Management Instrumentation (WMI) framework, and multiple embedded payloads are decrypted and loaded into memory.
The infection chain then shifts to hiding payloads using steganography, where an encrypted PowerShell payload is embedded in PNG images hosted on public CDNs and retrieved dynamically via resolved WinINet APIs.
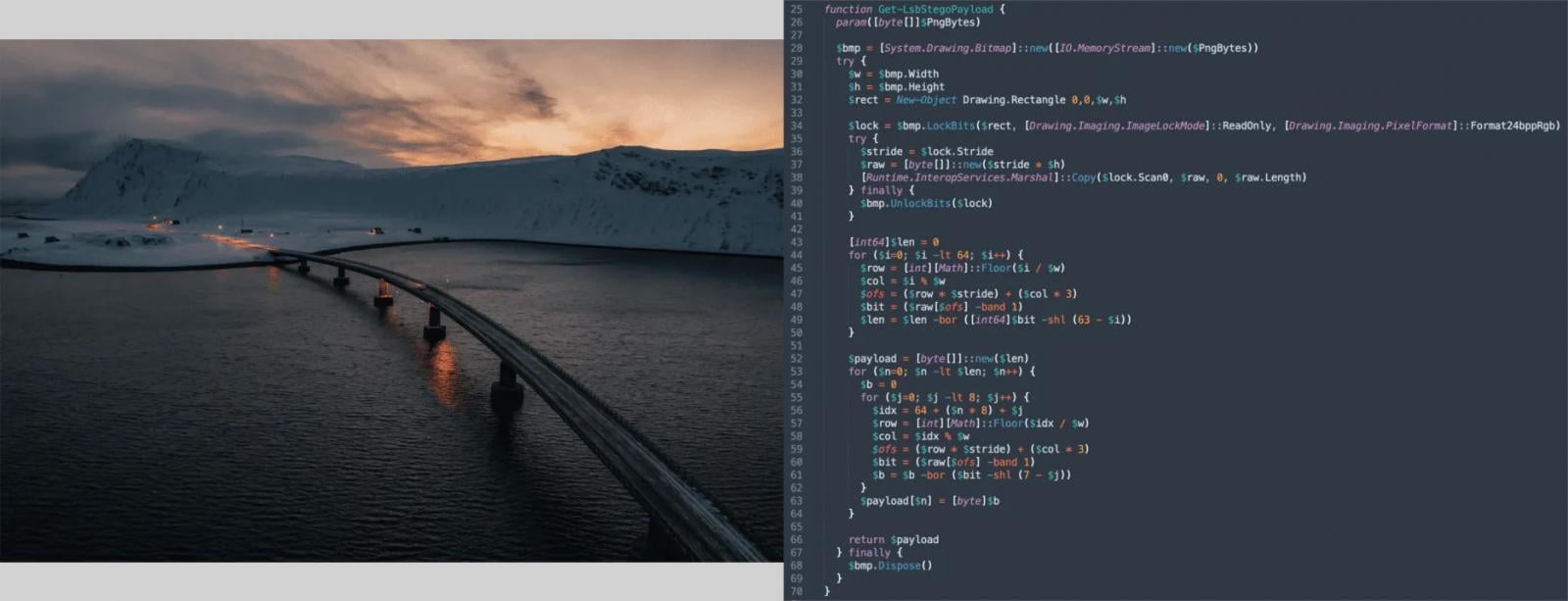
Source: BlackPoint
The payload data is extracted via LSB steganography, decrypted, GZip-decompressed, and executed fully in memory. The final PowerShell stage decrypts and launches native shellcode, which maps and executes the Amatera infostealer.
.jpg)
Source: BlackPoint
Once active on the host, the malware connects to a hardcoded IP address to retrieve endpoint mappings and awaits additional binary payloads delivered via HTTP POST requests.
BlackPoint Cyber classifies Amatera malware as a standard infostealer that can collect browser data and credentials from infected systems, but does not go into many details about its data-theft capabilities.
Based on code overlap, Amatera is based on the ACR infostealer and is under active development, available as malware-as-a-service (MaaS). Proofpoint researchers say in a report last year that Amatera has become more sophisticated from one update to another.
Amatera operators have delivered it in the past via the ClickFix method, where users were tricked into directly executing a PowerShell command.
To defend against these attacks, the researchers propose restricting access to the Windows Run dialog via Group Policy, removing App-V components when not needed, enabling PowerShell logging, and monitoring outbound connections for mismatches between the HTTP Host header or TLS SNI and the destination IP.

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.




