A sophisticated ClickFix campaign targeting Facebook users has been identified, leveraging social engineering to extract live session credentials directly from victims’ browsers.
Unlike traditional phishing exploits that rely on software vulnerabilities, this campaign guides victims through a guided credential-harvesting process disguised as account verification.
Researchers identified 115 webpages across the attack chain and eight distinct exfiltration endpoints, primarily targeting creators, monetized pages, and businesses seeking verification badges.
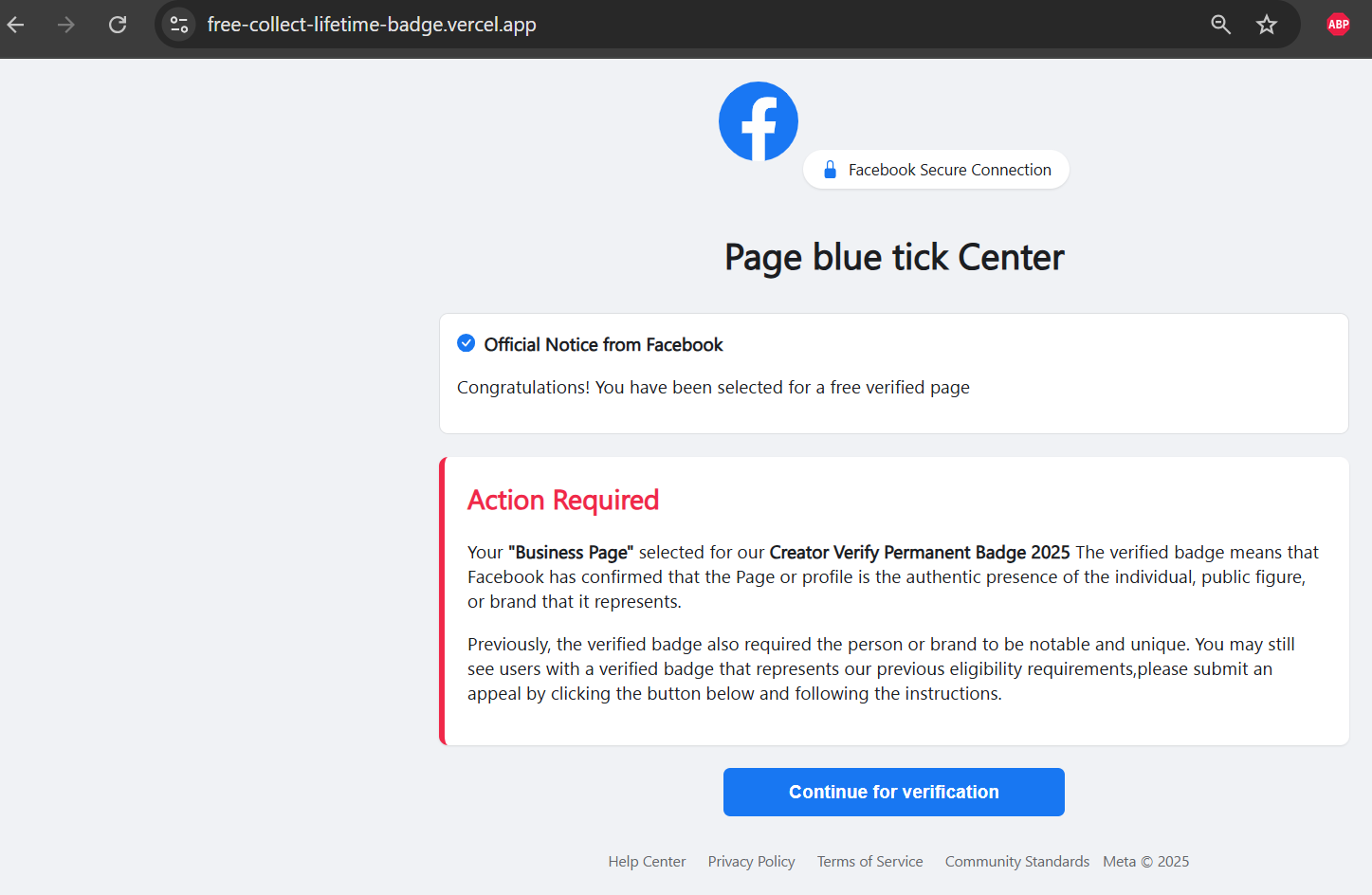
The campaign initiates with a fake Facebook verification or appeal page promising free verified badges or account recovery assistance.
Victims are presented with animated verification sequences that create legitimacy before being redirected to second-stage pages impersonating the “Facebook Blue Tick Center.”
Here, attackers introduce instructional videos explicitly guiding victims to extract session tokens (c_user and xs values) from their browser’s developer tools and cookie storage.
Once victims submit these session credentials, real-time JavaScript validation ensures only valid Facebook tokens are accepted, reducing attacker-side noise.
Unit42 first highlighted this campaign on December 19, 2025, while infrastructure analysis reveals related phishing pages have been active since January 2025.
The validated tokens are immediately exfiltrated via JSON POST requests to third-party collection endpoints like submit-form[.]com, Formspark, and shiper[.]app.
Instead of a fake login page, the flow starts with a badge or appeal pretext and pushes victims into submitting session tokens from their browser.
If the session token cannot be replayed, the workflow falls back to harvesting security backup codes and passwords through subsequent phishing pages.
Infrastructure and Collection
The attackers employ a multi-layered infrastructure strategy to maintain resilience. Phishing pages are hosted across abuse-friendly platforms, including Netlify, Vercel, Wasmer, GitHub Pages, Surge, Cloudflare Pages, and Neocities enabling rapid redeployment when pages are taken down.
Exfiltration is decoupled from hosting through serverless form backends, allowing attackers to separate visible phishing infrastructure from data collection endpoints.
Analysis reveals extensive infrastructure reuse through page-title pivots. A single title like “Facebook Security Confirmation” appears across 14 distinct URLs, while 103 unique hostnames serve Facebook verification-themed content since January 2025.
Hostname naming conventions show strong clustering around “blue tick,” “verified badge,” “appeal,” and “free verification,” indicating centralized content templates and coordinated operations.
Advanced variants introduce environment-profiling logic to dynamically branch the attack flow based on victim geolocation and proxy status.
One observed variant queries https://handle[.]gadgetsdecory[.]xyz:3000/anotherdc to profile IP intelligence, geolocation, and proxy usage.
Non-proxy users outside Pakistan receive different instructional videos and expanded harvesting workflows, including direct email-based exfiltration to hardcoded attacker inboxes ([email protected], [email protected], [email protected]).
Commented-out code reveals additional operator identities including “sajjad boss,” “sajjad,” and “waseem,” suggesting a small but organized threat group managing multiple attack chains simultaneously.
Defense Implications
This campaign demonstrates why ClickFix attack remains highly effective: it bypasses the need for software exploits entirely, relying instead on social engineering and trust manipulation.
The Meta page is designed to create urgency by warning users that their account or page is scheduled for deletion due to violations of community guidelines.
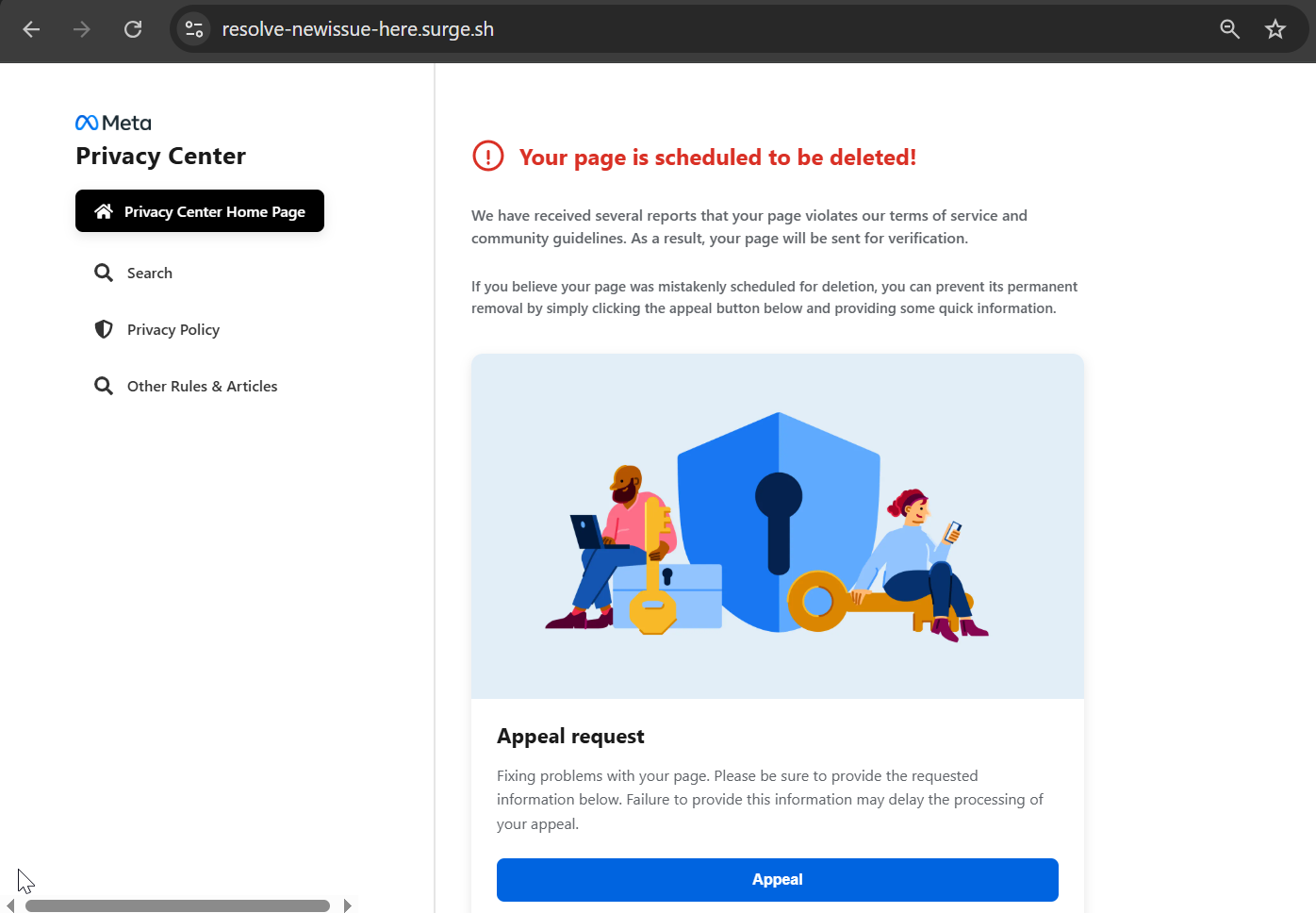
The “verification” narrative creates urgency and legitimacy, convincing users to surrender authenticated session access voluntarily the most valuable asset for account takeover.
Defenders should prioritize monitoring serverless form backends and collection endpoints rather than individual phishing pages.
Pages requesting c_user and xs values, especially when framed as “verification,” “appeal,” “badge,” or “security confirmation,” should trigger immediate alerts.
Tracking abuse-friendly hosting patterns and pivoting on reused page titles enables reliable expansion of campaign infrastructure.
With stolen sessions enabling immediate account takeover, rapid detection and collection endpoint blocking remain critical for reducing attacker success.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
