A dangerous new iteration of the “Contagious Interview” campaign that weaponizes Microsoft Visual Studio Code task files to distribute sophisticated malware targeting software developers.
This campaign, which began over 100 days ago, has intensified dramatically in recent weeks with 17 malicious GitHub repositories identified across 11 distinct attack variants.
North Korean threat actors linked to the Lazarus Group continue their sustained assault on software engineers through elaborate supply chain attacks disguised as legitimate job recruitment processes.
The latest “Fake Font” campaign exploits VS Code’s task automation feature to execute JavaScript malware hidden within files masquerading as web fonts, ultimately deploying the InvisibleFerret Python backdoor designed for cryptocurrency theft and persistent system access.
The OpenSourceMalware research team has identified a new variation of the “Contagious Interview” campaign that uses malicious Microsoft VS Code.
Attack Methodology
The attack begins with social engineering on LinkedIn, where fake recruiters impersonating cryptocurrency or fintech companies contact targets with enticing job opportunities.
The repository looks legitimate a web application project with a React frontend, Node.js backend, proper README, even a CI/CD configuration.
Victims receive what appears to be a routine coding assessment a GitHub repository containing a seemingly legitimate web application project, complete with a React frontend, a Node.js backend, and professional documentation.
The malicious payload hides within the .vscode/tasks.json file, which VS Code uses for workflow automation.
Configured with “runOn”: “folderOpen” and “reveal”: “never” parameters, the task executes silently when developers open the project and click “Trust Workspace.”
The command node public/fonts/fa-brands-regular.woff2 launches what appears to be a font file but is actually heavily obfuscated JavaScript malware.
OSM’s investigation began with a community-submitted repository (github.com/Brio97/Assignment), revealing a user compromised during a fake recruiter scam.
Analysis of the malicious “font” file exposed JavaScript source code using Base91 encoding an advanced binary-to-ASCII encoding scheme that evades detection by security tools optimized for common formats like Base64.
The first-stage loader, known as BeaverTail, creates hidden directories in ~/.npm/, installs npm packages including axios and request, then contacts a command-and-control server at eth-mainnet-alchemy.com a typosquat domain mimicking the legitimate Alchemy Ethereum API service.
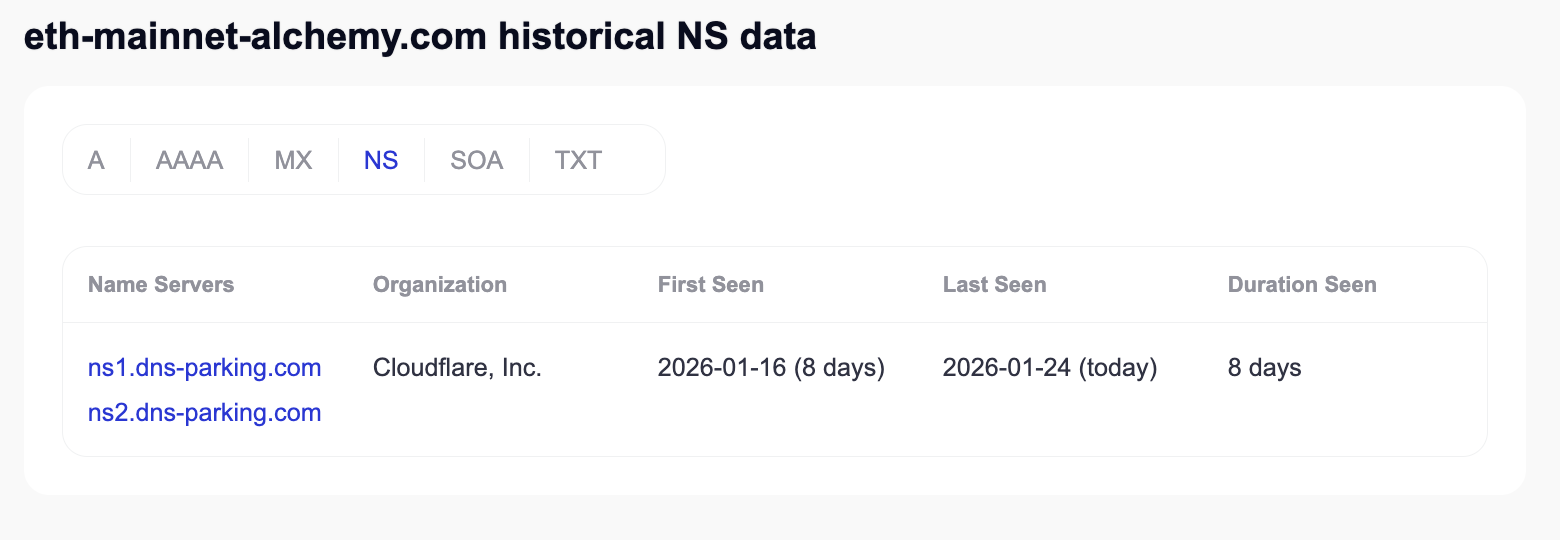
Registered on January 16, 2026, this fake domain delivers a 96KB JavaScript payload featuring triple-layer Base91 obfuscation.
InvisibleFerret Backdoor
The final payload is InvisibleFerret, a Python-based backdoor with extensive capabilities including theft of 13+ cryptocurrency wallet extensions (MetaMask, Phantom, Coinbase Wallet, Trust Wallet, Exodus, Ledger Live), browser credential harvesting, keylogging, and clipboard hijacking that replaces cryptocurrency addresses with attacker-controlled wallets.
The malware establishes persistence across Windows, macOS, and Linux systems, surviving reboots and maintaining remote access via WebSocket connections.
The complete infection chain executes in approximately 40 seconds often before victims finish reading the coding assessment instructions.
Many compromised developers remain unaware that the VS Code repository combination facilitated the theft until forensic analysis reveals the attack vector.
OSM successfully analyzed 14 of the 17 identified repositories, discovering 11 unique payload variants ranging from 1,489 bytes to 147,449 bytes a 99-fold size difference.
Only three repository pairs share identical payloads, suggesting either multiple independent Lazarus Group teams adopting the fake font technique or deliberate diversification of attack infrastructure to maximize operational security and target-specific customization.
OpenSourceMalware tracks this campaign under the #fake-font tag with all related indicators of compromise available at opensourcemalware.com.
The campaign represents the third sub-campaign of the ongoing “Contagious Interview” operation active since 2023, highlighting the persistent and evolving threat facing the software development community.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
