The zLabs research team has identified a sophisticated new threat campaign targeting Spanish Android users through a malware strain called DroidLock.
Unlike traditional ransomware that encrypts files, this Android-focused threat employs a more direct approach locking devices with ransomware-style overlays and demanding payment while maintaining complete control over compromised handsets.
DroidLock primarily spreads through phishing websites that host deceptive applications. Once installed, the malware leverages a two-stage infection process, beginning with a dropper that tricks users into installing a secondary payload containing the actual malicious code.
By exploiting accessibility services and device administrator privileges, DroidLock achieves near-complete device takeover, employing 15 distinct commands to communicate with its command-and-control (C2) infrastructure.
The infection chain starts with social engineering rather than technical exploitation. The dropper presents itself as a legitimate application, often masquerading as popular services such as Orange, to convince users to grant installation permissions.
Once executed, it requests accessibility services a consent that Android users often grant without understanding the implications.
With this access granted, the malware automatically approves additional permissions for SMS access, call logs, contacts, and audio recording without further user interaction.
The malware leverages both websocket and HTTP communication in order to talk with its C2 (Command & Control server).
This technique bypasses Android’s standard security restrictions by exploiting the accessibility service framework, which was designed to assist users with disabilities but remains a common attack vector for malicious applications.
Ransomware-Style Intimidation
Upon receiving the appropriate command from its C2 server, DroidLock displays a full-screen WebView overlay displaying a threatening ransomware message.
The overlay demands immediate contact with threat actors via email, requiring the victim’s device ID for identification.
Critically, the malware threatens complete data destruction within 24 hours if payment is not received creating psychological pressure that drives victims toward payment.
While this malware variant does not encrypt files like traditional ransomware, it possesses the technical capability to completely wipe the device, making the threat credible and alarming to average users unfamiliar with technical security concepts.
DroidLock’s command set reveals the extent of potential compromise. The malware can lock devices using device administrator privileges, change PINs and biometric authentication settings, perform factory resets, and remotely access device screens through VNC connections.
The malware also captures images using the front-facing camera, silences audio, and maintains persistent screen recording capabilities that convert captured content to base64-encoded JPEG format for exfiltration to remote servers.
Additionally, DroidLock implements credential-stealing mechanisms through two distinct overlay techniques.
The first presents fake lock-pattern screens, while the second uses WebView overlays loaded with attacker-controlled HTML content that mimics legitimate banking and authentication applications.
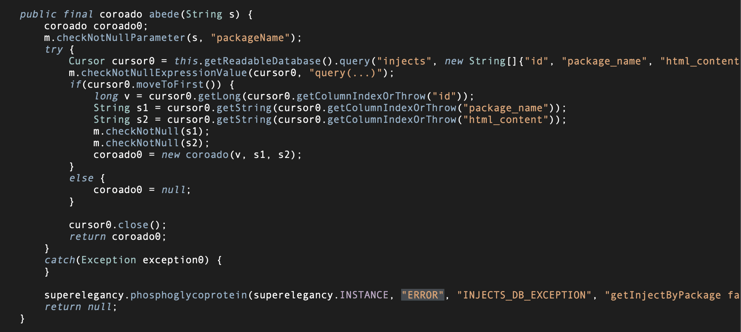
The malware maintains a database of targeted applications, dynamically retrieving and displaying appropriate overlays when victims open specific apps.
Enterprise Implications
Security researchers from Zimperium note that while DroidLock presents comprehensive device-takeover capabilities, their Mobile Threat Defense platform detects all identified samples through on-device dynamic detection engines operating in zero-day fashion.
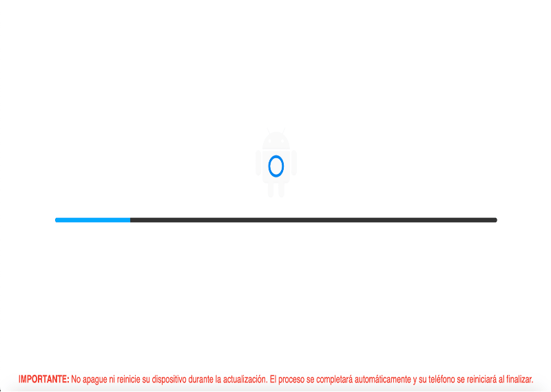
The overlay is put on top upon receiving the BLACK_SCREEN_UPDATE_SYSTEM command from the C2 server.
For enterprises, the implications are severe infected devices can intercept one-time passwords, change security credentials, and transform corporate handsets into hostile endpoints within managed networks.
The MITRE ATT&CK framework maps DroidLock across multiple tactics, from initial phishing-based access through credential access, collection, command-and-control, and eventual impact phases, demonstrating the sophistication of this emerging threat to mobile-dependent organizations.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
