A new malware called FinalDraft has been using Outlook email drafts for command-and-control communication in attacks against a ministry in a South American country.
The attacks were discovered by Elastic Security Labs and rely on a complete toolset that includes a custom malware loader named PathLoader, the FinalDraft backdoor, and multiple post-exploitation utilities.
The abuse of Outlook, in this case, aims to achieve covert communications, allowing the attackers to perform data exfiltration, proxying, process injection, and lateral movement while leaving minimal possible traces.
Attack chain
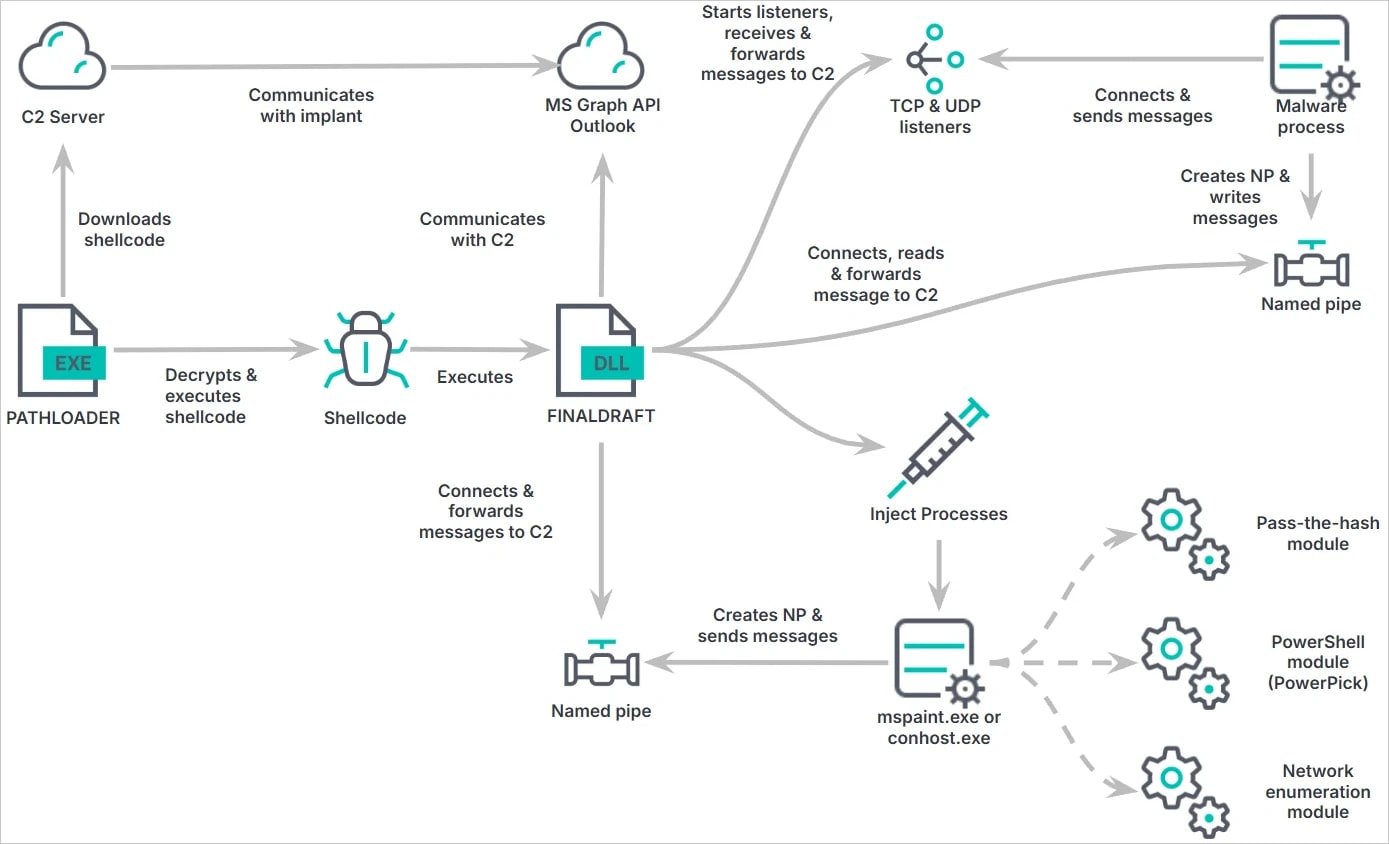
The attack begins with the threat actor compromising the targer’s system with PathLoader, a small executable file that executes shellcode, including the FinalDraft malware, retrieved from the attacker’s infrastructure.
PathLoader incorporates protections against static analysis by performing API hashing and using string encryption.
FinalDraft is used for data exfiltration and process injection. After loading the configuration and generating a session ID, the malware establishes communication through Microsoft Graph API, by sending and receiving commands through Outlook email drafts.
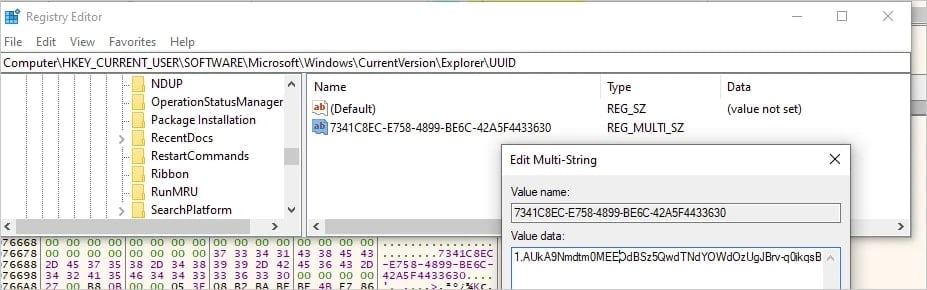
FinalDraft retrieves an OAuth token from Microsoft using a refresh token embedded in its configuration, and stores it in the Windows Registry for persistent access.
Source: Elastic Security
By using Outlook drafts instead of sending emails, it avoids detection and blends into normal Microsoft 365 traffic.
Commands from the attacker are hidden in drafts (r_
FinalDraft supports a total of 37 commands, the most important of them being:
- Data exfiltration (files, credentials, system info)
- Process injection (running payloads in legitimate processes like mspaint.exe)
- Pass-the-Hash attacks (stealing authentication credentials for lateral movement)
- Network proxying (creating covert network tunnels)
- File operations (copying, deleting, or overwriting files)
- PowerShell execution (without launching powershell.exe)
Elastic Security Labs also observed a Linux variant of FinalDraft, which can still use Outlook via REST API and Graph API, as well as HTTP/HTTPS, reverse UDP & ICMP, bind/reverse TCP, and DNS-based C2 exchange.
Source: Elastic Security
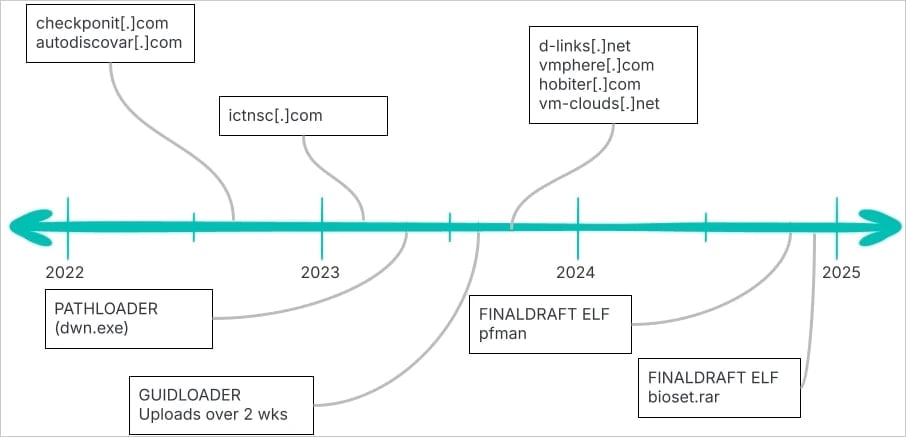
The researchers present the attack campaign, dubbed REF7707, in a separate report that describes several opsec mistakes that are in contrast with the advanced intrusion set used, and which led to the attacker’s exposure.
REF7707 is a cyber-espionage campaign focused on a South American foreign ministry, but analysis of the infrastructure revealed links to Southeast Asian victims, suggesting a broader operation.
The investigation also uncovered another previously undocumented malware loader used in the attacks, named GuidLoader, capable to decrypt and execute payloads in memory
Source: Elastic Security
Further analysis showed the attacker’s repeated targeting of high-value institutions via compromised endpoints in telecommunications and internet infrastructure providers in Southeast Asia.
Additionally, a Southeast Asian university’s public-facing storage system was used to host malware payloads, suggesting prior compromise or a supply chain foothold.
YARA rules to help defenders detect Guidloader, PathLoader, and FinalDraft, are available at the bottom of Elastic’s reports [1, 2].
