FireScam, an information stealer malware with spyware capabilities, is being disseminated as a fake “Telegram Premium” application. The malware spreads through a phishing website on GitHub.io that imitates the legitimate RuStore app store.
The malware uses a multi-stage infection procedure that begins with a dropper APK and then does comprehensive surveillance once installed.
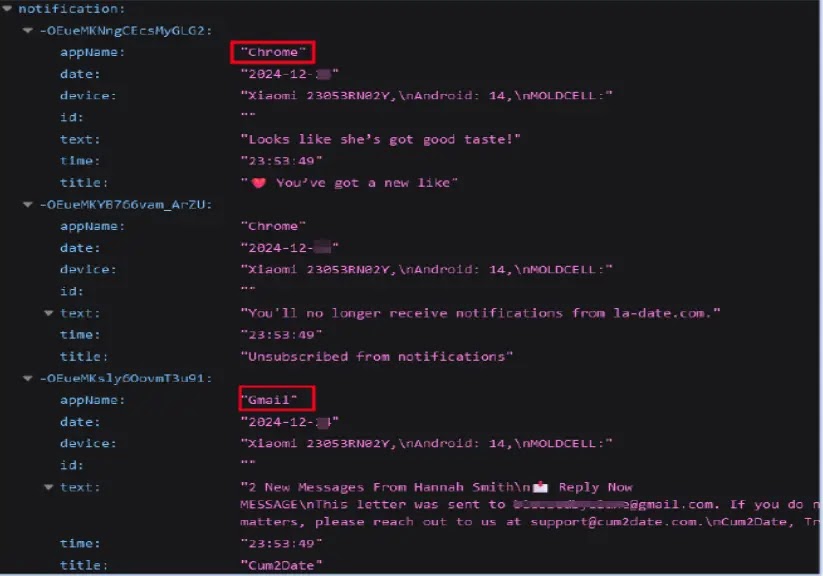
The malware steals sensitive data from a Firebase Realtime Database endpoint, including messages, notifications, and other app data.
FireScam secretly collects useful data by tracking device behaviors such as screen state changes, e-commerce transactions, clipboard activity, and user involvement.
It also obtains alerts from a variety of apps, including system programs, with the ability to steal sensitive information and track user activity. It uses obfuscation techniques to conceal its purpose and avoid being discovered by security tools and researchers.
FireScam Android Malware Abusing Firebase Services
FireScam, an information-stealing malware, masquerades as a legitimate application to deceive users into installing it, from which it takes sensitive information and exfiltrated data to the Firebase C2 endpoint.
Investigate Real-World Malicious Links, Malware & Phishing Attacks With ANY.RUN – Try for Free
“An APK is downloaded from this phishing website, acting as a dropper that subsequently installs the FireScam malware, disguised as the “Telegram Premium” application,” Cyfirma said in a report shared with Cyber Security News.

The exfiltrated data is temporarily stored in the Firebase Realtime Database at the URL “https[:]//androidscamru-default-rtdb[.]firebaseio[.]com” and is later erased after perhaps filtering and saving the vital content in another private storage place.
The dropper requests Extensive rights, including storage access, app administration, and the ability to update or remove programs without the user’s permission.
An application can manage its updates with the ENFORCE_UPDATE_OWNERSHIP permission, which helps with persistence by preventing others from updating and needing user consent for external updates.
Additional permissions that FireScam requests enable access to notifications on the infected device and unrestricted background activities (exclusion from battery optimization).
The spyware tracks and records USSD responses upload important events to the C2 server and steals private information such as account balances.
Additionally, it avoids analysis and detection by using sandbox detection measures, dynamic receiver access restriction, and obfuscation techniques.
These malicious websites take advantage of user confidence by imitating legitimate platforms, like the RuStore app store, to trick people into downloading and installing fake apps, such as “Telegram Premium.”
Because consumers frequently overlook the warning indicators of phishing or malicious intent, these phishing methods have a high success rate.
Organizations must put strong cybersecurity safeguards and proactive defensive tactics in place as attacks like FireScam continue to change.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!
