Multiple Fortinet FortiWeb instances recently infected with web shells are believed to have been compromised using public exploits for a recently patched remote code execution (RCE) flaw tracked as CVE-2025-25257.
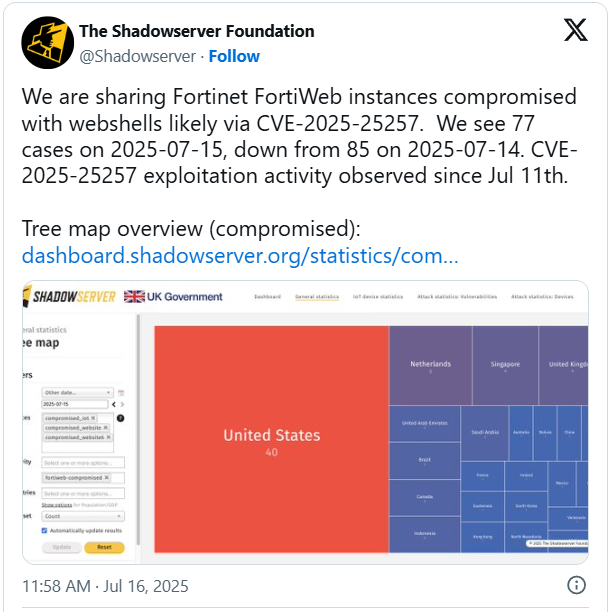
News of the exploitation activity comes from threat monitoring platform The Shadowserver Foundation, which observed 85 infections on July 14 and 77 on the next day.
The researchers reported that these Fortinet FortiWeb instances are believed to be compromised through the CVE-2025-25257 flaw.
CVE-2025-25257 is a critical pre-authenticated RCE via SQL injection (SQLi) affecting FortiWeb 7.6.0 through 7.6.3, 7.4.0 through 7.4.7, 7.4.0 through 7.4.7, and 7.0.0 through 7.0.10.
Fortinet released patches on July 8, 2025, urging users to upgrade to FortiWeb 7.6.4, 7.4.8, 7.2.11, or 7.0.11 and later versions of each branch.
“An improper neutralization of special elements used in an SQL command (‘SQL Injection’) vulnerability in FortiWeb may allow an unauthenticated attacker to execute unauthorized SQL code or commands via crafted HTTP or HTTPs requests,” explained Fortinet.
On July 11, exploits were made public by cybersecurity firm WatchTowr, and a co-discoverer of the flaw, “faulty *ptrrr.” These exploits demonstrated methods for planting webshells or opening reverse shells on unpatched endpoints.
The exploitation involves performing SQLi via crafted Authorization headers in HTTP requests sent to /api/fabric/device/status, which writes a malicious .pth file into Python’s ‘site-packages.’
A legitimate FortiWeb CGI script (/cgi-bin/ml-draw.py) is then accessed remotely, causing the code in the malicious .pth file to be executed and achieving remote code execution on the device.
At the time, there was no evidence of active exploitation in the wild, but the release of public exploits made patching critical for administrators.
Today’s confirmation of active exploitation by The Shadowserver Foundation can be seen as a wake-up call for those who have yet to install the latest software on their devices.
According to the threat intelligence organization, 223 FortiWeb management interfaces were still exposed as of yesterday, although there’s no visibility into the version they run.
Of the compromised endpoints, most (40) are located in the United States, followed by the Netherlands (5), Singapore (4), and the United Kingdom (4).
FortiWeb is a Web Application Firewall (WAF) used by large enterprises, government agencies, and managed security service providers to block and detect unwanted HTTP traffic.
If upgrading to a secure version immediately is impossible, it is recommended to turn off the HTTP/HTTPS administrative interface to restrict access to the vulnerable component (/api/fabric/device/status).

While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz’s detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.
