Chinese threat actors are weaponizing NFC technology to steal funds from victims’ bank remotely accounts through sophisticated Android malware campaigns, with security researchers identifying at least $355,000 in fraudulent transactions from a single operation.
Group-IB researchers have uncovered a sprawling cybercrime ecosystem centered around NFC-enabled Android applications that enable criminals to conduct unauthorized tap-to-pay transactions remotely.
Dubbed “Ghost Tap,” these malicious applications exploit Near Field Communication technology to relay payment data from victims’ devices to attackers’ devices, allowing them to drain bank accounts without physical access to payment cards.
How the Attack Works
The Ghost Tap scheme operates through a sophisticated relay mechanism involving two specialized applications: a “reader” installed on the victim’s device and a “tapper” installed on the attacker’s device.
Criminals lure victims through smishing (SMS phishing) and vishing (voice phishing) campaigns, convincing them to install malicious APK files and tap their bank cards against their Android devices.
Once the victim’s card contacts the compromised phone, the malware captures the NFC payment data and relays it to the attacker’s device via command-and-control servers.
The cybercriminals then use fraudulently obtained point-of-sale terminals to cash out the stolen funds, completing transactions as if the victim’s card were physically present.
In alternative scenarios, criminals preload mobile wallets with compromised card details and deploy networks of mules across the globe to make purchases at physical retail locations using the modified tap-to-pay applications.
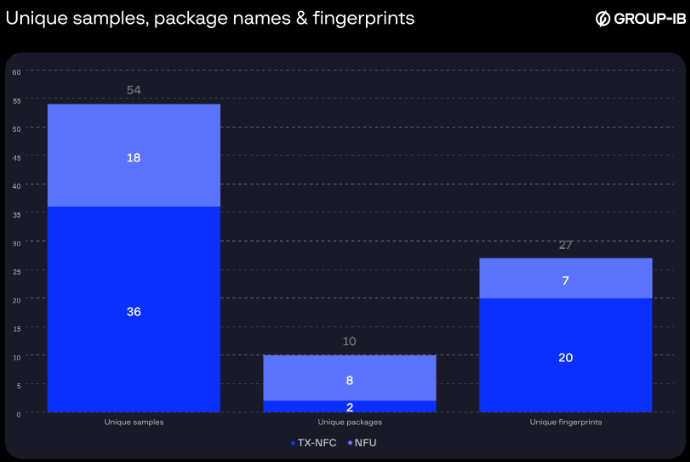
Group-IB’s investigation identified over 54 APK samples, with some malware variants masquerading as legitimate banking applications.
The research uncovered three major malware vendors operating within Chinese cybercrime communities on Telegram: TX-NFC, X-NFC, and NFU Pay.
TX-NFC, the largest vendor identified, established its Telegram channel in January 2025 and rapidly accumulated over 21,000 subscribers.
The group offers customer support in English and prices its malware from $45 for one-day access up to $1,050 for three-month subscriptions.
X-NFC emerged in December 2024 with over 5,000 members, while NFU Pay, despite having fewer subscribers, has its application redistributed by other vendors under different names.
These vendors continuously evolve their offerings, with NFU Pay reportedly providing customized builds for specific countries like Brazil and Italy, including modifications that remove login requirements to facilitate faster victim targeting.
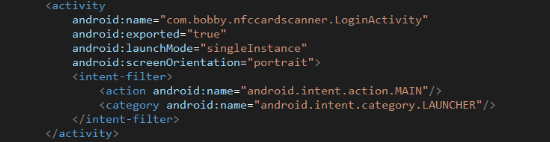
The application has two activity components, the first of which; “LoginActivity” handles user authentication and serves as the application’s main entrypoint:
Complementing the malware ecosystem is a thriving market for illegitimately acquired POS terminals.
Oedipus, a Telegram channel affiliated with TX-NFC vendors, openly advertises POS terminals from financial institutions across the Middle East, Africa, and Asia.
Since November 2024, this single operation has processed approximately $355,000 in fraudulent transactions using these stolen terminals.
Authorities worldwide have begun responding to this emerging threat. Notable arrests include 11 Chinese nationals apprehended in Knoxville, Tennessee in March 2025 for purchasing gift cards worth tens of thousands of dollars using these Android applications marking the first arrests of their kind in the United States.
In November 2024, Singapore authorities arrested five individuals conducting contactless payments at high-value stores without physical cards. Czech police, Malaysian authorities, and Chinese law enforcement have also made arrests related to these NFC relay attacks.
The Visa Payment Ecosystem Risk and Control team’s Spring 2025 Biannual Threats Report specifically highlighted the continued use of NFC-enabled malicious applications for relay fraud, while Credit China issued advisories detailing cases where victims lost at least $13,000 to these schemes.
Technical Analysis
Security researchers analyzing the malware discovered that applications like TX-NFC are obfuscated and packed using 360 Jiagu, a Chinese commercial packer.
Based on Group-IB Fraud Protection data tracked from May 2024 to December 2025, we can observe a steady increase in the detection of tap-to-pay malware samples.
The malware requests critical permissions including NFC hardware access, internet connectivity, and foreground service capabilities to maintain persistence even when users aren’t actively using their devices.
The applications specifically target ISO 14443 contactless payment cards and various NFC tag types.
Upon discovering an NFC-enabled payment card, the malware sends the “2PAY.SYS.DDF01” command to initiate communication with the Proximity Payment System Environment, storing available application identifiers before relaying all data through WebSocket services to the attackers’ command-and-control infrastructure.
Code analysis revealed that some variants are based on NFCProxy, an open-source project available on GitHub, demonstrating how cybercriminals adapt legitimate technologies for malicious purposes.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
