The recently uncovered Gunra ransomware is the family to weaponize leaked Conti source code, unleashing rapid-fire double-extortion attacks against Windows endpoints worldwide.
First seen on dark-web leak sites in April 2025, Gunra moves with blistering speed, pressuring victims to negotiate within five days and threatening public data dumps to multiply the pain.
Unlike spray-and-pray spam campaigns, the operators favor hands-on intrusion, typically breaching networks through stolen RDP credentials or unpatched VPN gateways before pivoting laterally to domain controllers.
Once administrative footholds are secured, the malware is pushed to dozens of machines in minutes via PsExec or Group Policy, triggering simultaneous encryption that hobbles business operations.
ASEC analysts noted that more than a dozen enterprises across manufacturing, healthcare, and logistics reported interruptions traced to Gunra in its first three months of activity.
Internally, the strain mirrors Conti’s multithreaded model: it spawns as many encryption threads as there are logical CPU cores, maximizing disk throughput while minimizing dwell time.
.webp)
Each thread generates an RSA-2048 key embedded in the binary to derive a ChaCha20 session key for file scrambling, then appends the “.ENCRT” extension.
Crucially, the Trojan skips executable, driver, and system files to preserve OS stability, ensuring victims can still read the ransom note “R3ADM3.txt” left in every directory.
.webp)
Gunra’s parting shot is a surgical removal of Windows Shadow Copies. By driving WMI through WMIC, it enumerates every snapshot and deletes them via the following command:-
cmd.exe /c C:WindowsSystem32wbemWMIC.exe shadowcopy where "ID={GUID}" deleteInfection Mechanism
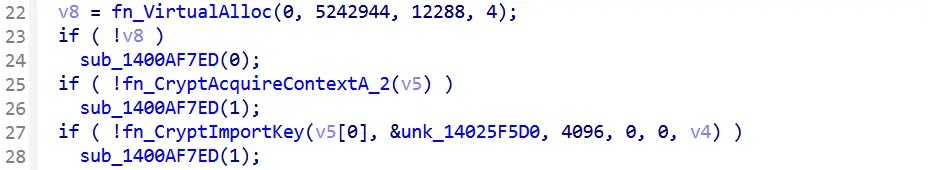
At launch, Gunra creates a unique mutex, then calls GetNativeSystemInfo to size its thread pool.
.webp)
If the host sports 16 CPU cores, the malware spawns 16 encryption routines, each carving 5 MB file chunks to feed the fn_FileCrypt function that wraps the ChaCha20 rounds shown below:-
for(int j=8;j>0;j-=2){
v7+=v11;
v19=((v7^v19)>>16)|((v7^v19)>20)|((v15^v11)<<12);
/* …additional quarter-rounds… */
}Because the RSA public key is hard-coded and never leaves memory, network traffic remains minimal, preventing perimeter-based detection.
Endpoint defenses must therefore monitor abnormal thread fan-out and aggressive WMIC shadow-copy deletions to spot Gunra before backups vanish.
Experience faster, more accurate phishing detection and enhanced protection for your business with real-time sandbox analysis-> Try ANY.RUN now
