A sophisticated new botnet family has emerged in the cybersecurity landscape, demonstrating unprecedented innovation in malware design and attack methodologies.
The hpingbot malware, first detected in June 2025, represents a significant departure from traditional botnet architectures by leveraging legitimate online services and network testing tools to orchestrate distributed denial-of-service attacks while maintaining operational stealth.
Unlike conventional botnets that typically derive from leaked source code of established families like Mirai or Gafgyt, hpingbot stands out as a completely original creation built from scratch using the Go programming language.
This cross-platform threat targets both Windows and Linux/IoT environments, with variants compiled for multiple processor architectures including amd64, mips, arm, and 80386.
The malware’s developers have demonstrated remarkable resourcefulness by exploiting the popular text-sharing platform Pastebin for payload distribution and integrating the legitimate network diagnostic tool hping3 for launching DDoS attacks.
NSFOCUS Global analysts identified the botnet’s operations through their Fuying Lab Global Threat Hunting System, revealing that attackers have been continuously iterating and improving the malware since its initial deployment.
The threat actors behind hpingbot have shown particular focus on German targets, though the United States and Turkey have also experienced attacks.
What makes this botnet particularly concerning is its dual-purpose design—while capable of launching various DDoS attack vectors, its primary value appears to lie in its ability to download and execute arbitrary payloads, positioning it as a potential distribution platform for more dangerous malware including ransomware or advanced persistent threat components.
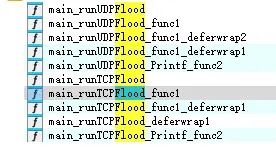
The botnet’s attack capabilities are extensive, supporting over ten different DDoS methods including ACK FLOOD, TCP FLOOD, SYN FLOOD, UDP FLOOD, and sophisticated mixed-mode attacks.
.webp)
Monitoring data indicates that since June 17, 2025, attackers have issued several hundred DDoS commands, though the botnet remains largely dormant between active campaigns, suggesting strategic operational planning rather than continuous assault patterns.
Pastebin-Based Payload Delivery Mechanism
The most innovative aspect of hpingbot lies in its sophisticated payload delivery system that exploits Pastebin’s legitimate infrastructure.
.webp)
The malware embeds four hard-coded Pastebin URLs within its binary, creating a dynamic command and control mechanism that bypasses traditional C2 detection methods.
This approach allows attackers to update instructions, distribute new payloads, and modify attack parameters without directly communicating with infected hosts through conventional channels.
The payload delivery process begins when hpingbot contacts its embedded Pastebin links to retrieve updated instructions.
These links frequently change content, ranging from simple IP addresses to complex shell scripts containing download instructions for additional malware components.
The malware includes a dedicated UPDATE module that processes these Pastebin-hosted instructions, enabling attackers to push new functionality or completely replace existing components remotely.
This system demonstrates remarkable operational security awareness, as attackers can modify their infrastructure rapidly while maintaining persistent access to compromised systems through the ubiquitous Pastebin platform.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
