Here’s a look at the most interesting products from the past week, featuring releases from Absolute Security, Catchpoint, Nagomi Security, Neon Cyber, and QuSecure.
![]()
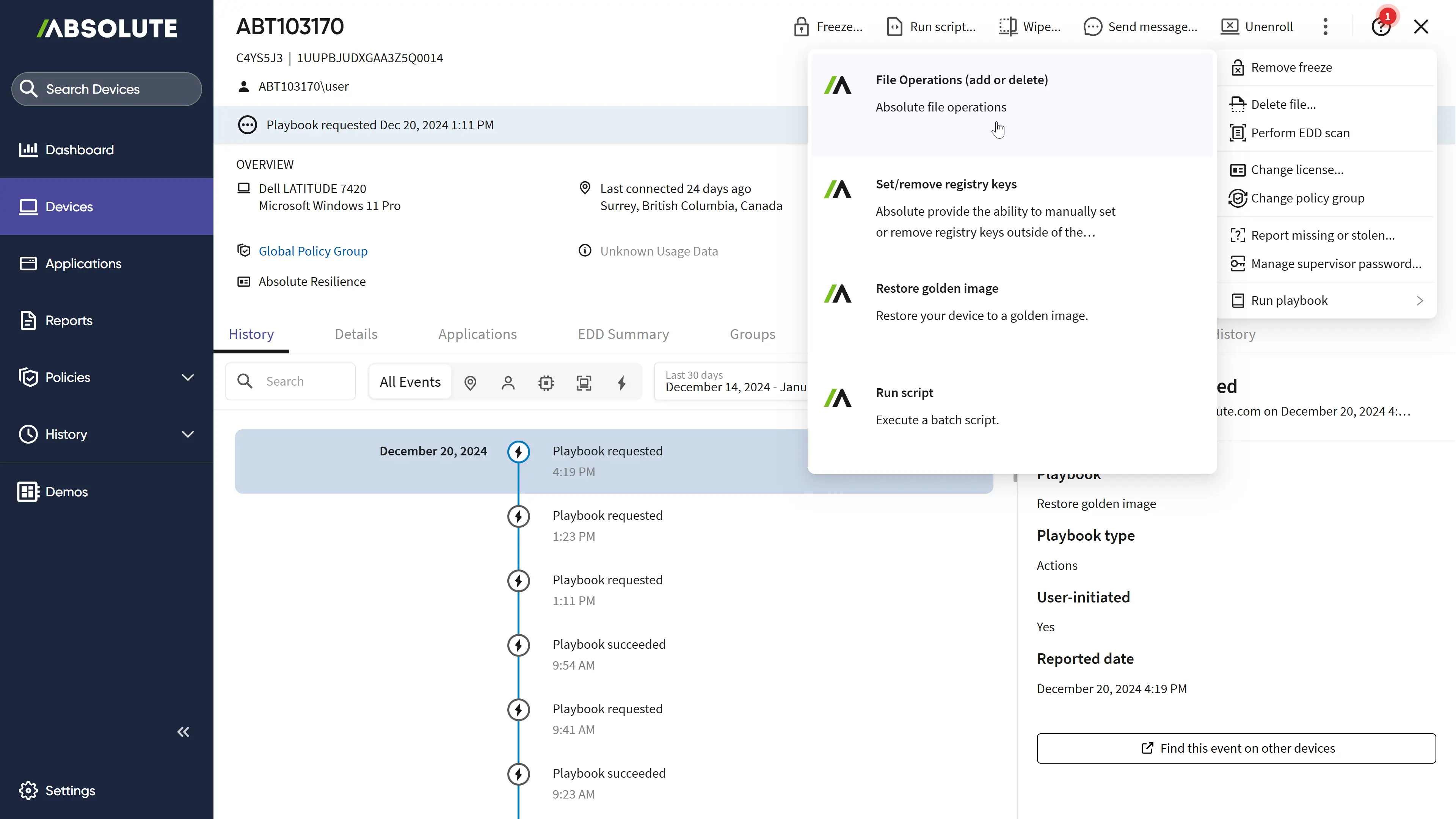
Absolute Security Rehydrate restores compromised endpoints
Rehydrate delivers business continuity endpoint restoration through a fully remote, single-click process. When your remote, mobile, and hybrid Windows PCs go down, recovery playbooks ranging from targeted remediations to full OS recovery can be executed across connected devices at enterprise scale.
![]()
Catchpoint improves monitoring posture with AI capabilities
Catchpoint released two AI-powered capabilities designed to simplify digital resilience for critical applications: Catchpoint Root Cause Analysis (RCA) and Catchpoint Advisor, which improve monitoring posture and bring immediate insights into IT incidents, ending the guesswork.
![]()
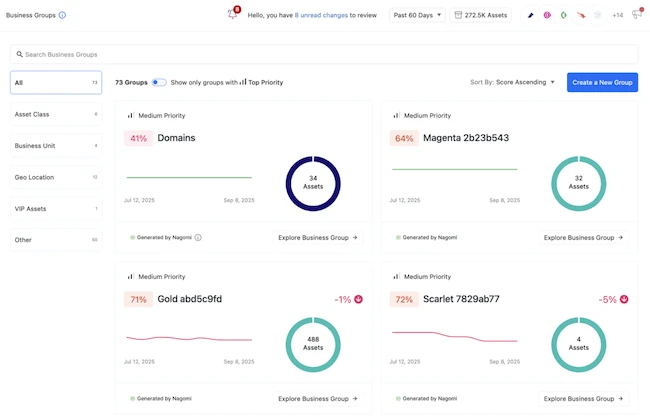
Nagomi Control reveals where organizations are most exposed
While CTEM has long provided a framework to identify risk, most cybersecurity programs stop at visibility. Nagomi Control fills this gap by delivering the execution layer of CTEM, enabling teams to automatically act on exposures faster, cut risk at scale, and do it with the stack they already have.
![]()
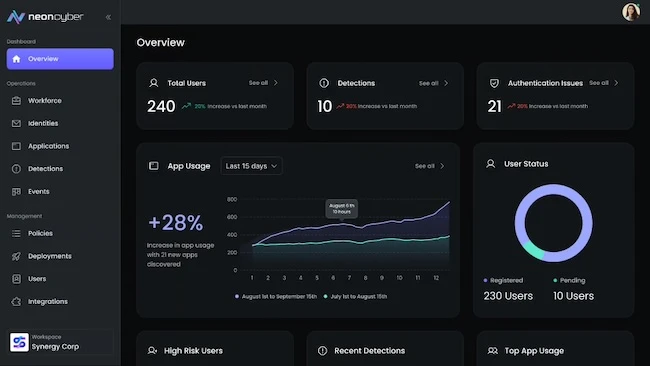
Neon Cyber exits stealth with Workforce Cybersecurity Platform
Neon Cyber announced its emergence from stealth and unveiled its Workforce Cybersecurity Platform (WCP). The platform offers AI-driven phishing protection at the browser level, visibility and governance for shadow SaaS applications, and behavior-based authentication and compliance management directly in the browser.
![]()
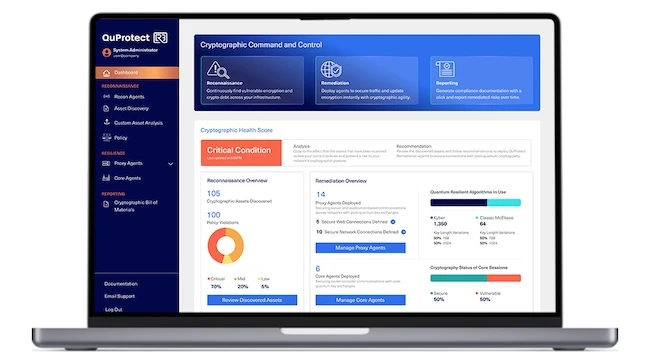
QuProtect R3 provides encryption visibility across systems
By identifying problematic cryptographic configurations before they impact operations, such as expiring certificates, unauthorized certificate authorities or weak encryption protocols, QuProtect R3 prevents security incidents and service disruptions. The platform’s standards-based approach makes it simple to replace weak algorithms, enforce encryption policies and prepare for both AI-driven threats and quantum attacks.
![]()
