A sophisticated new ransomware strain named KAWA4096 has emerged in the cybersecurity landscape, showcasing advanced evasion techniques and borrowing design elements from established threat actors.
Named after the Japanese word for “river,” this malicious software first surfaced in June 2025 and has already claimed at least 11 victims across multiple regions, with the United States and Japan serving as primary targets.
The ransomware demonstrates a concerning trend among cybercriminals of adopting successful elements from proven threat groups to enhance their credibility and operational effectiveness.
KAWA4096’s operators have strategically modeled their ransom note format after the notorious Qilin ransomware group while designing their data leak site to mirror the distinctive green-on-black terminal interface characteristic of the Akira ransomware operation.
Trustwave analysts identified this emerging threat through comprehensive monitoring of global ransomware activity, noting its sophisticated technical capabilities and deliberate mimicry of established ransomware families.
%20vs%20QILIN%20(right)%20ransom%20note%20(Source%20-%20Trustwave).webp)
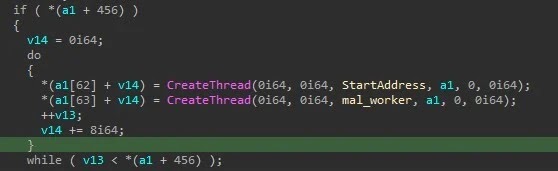
The malware’s multithreaded architecture enables efficient encryption across infected systems while implementing robust evasion mechanisms to avoid detection by security solutions.
KAWA4096 employs particularly noteworthy persistence and anti-recovery mechanisms that distinguish it from typical ransomware variants.
The malware creates a unique mutex named “SAY_HI_2025” to prevent multiple instances from running simultaneously, ensuring operational stability during the encryption process.
Shadow Copy Elimination Through WMI
The ransomware’s most significant technical innovation lies in its systematic elimination of Windows shadow copies using Windows Management Instrumentation.
KAWA4096 leverages WMI’s Win32_Process::Create method to execute two critical commands that completely remove system recovery options.
.webp)
The malware first runs vssadmin.exe Delete Shadows /all /quiet to silently delete all volume shadow copies, followed by wmic shadowcopy delete /nointeractive to ensure comprehensive removal without user interaction prompts.
.webp)
This dual-command approach effectively prevents victims from recovering encrypted files through Windows’ built-in backup mechanisms, significantly increasing the pressure to pay ransom demands.
.webp)
The technique represents a sophisticated understanding of Windows recovery systems and demonstrates the threat actors’ commitment to maximizing operational impact while maintaining stealth throughout the attack process.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now
