A threat actor exploited a zero-day vulnerability in Samsung’s Android image processing library to deploy a previously unknown spyware called ‘LandFall’ using malicious images sent over WhatsApp.
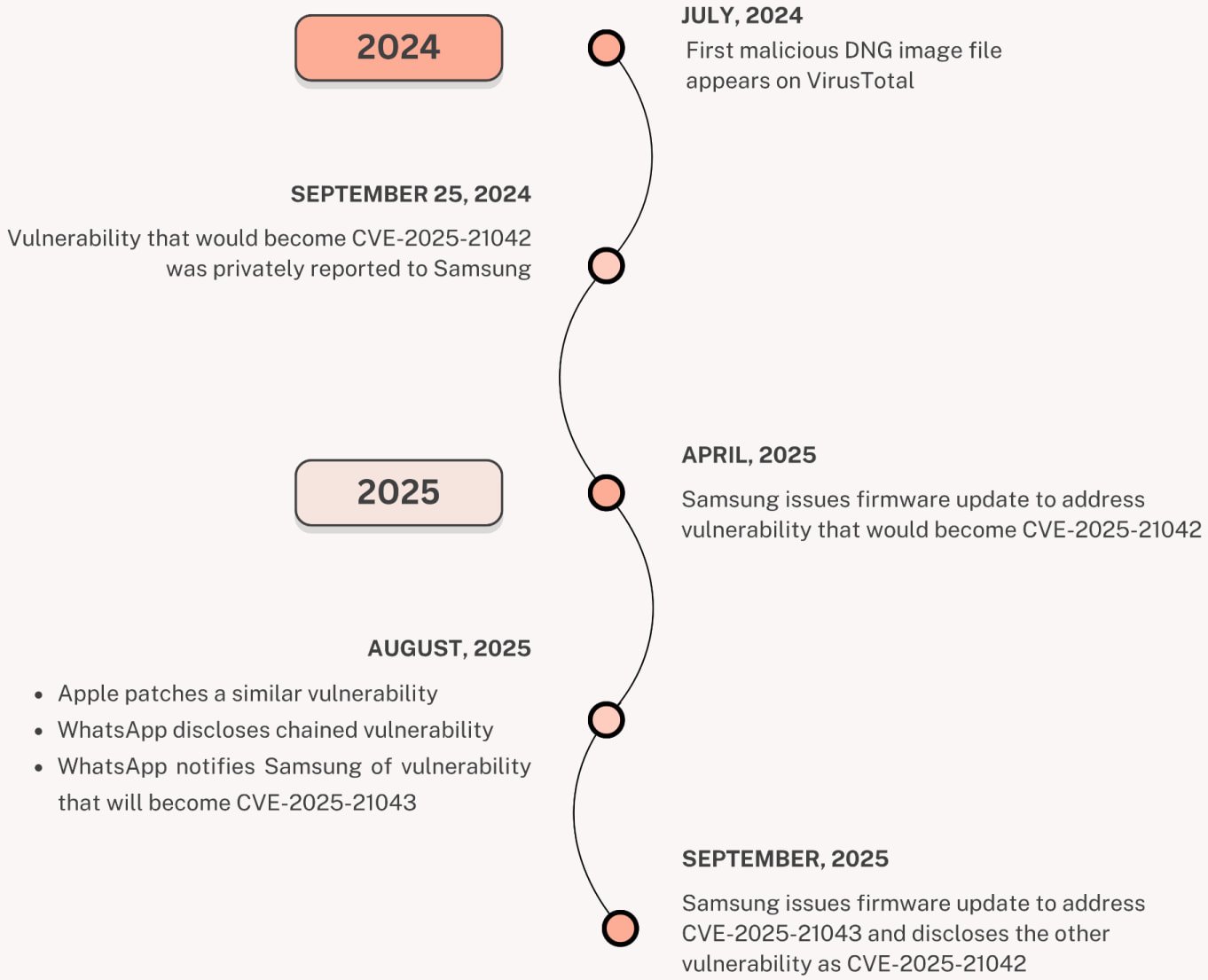
The security issue was patched this year in April, but researchers found evidence that the LandFall operation was active since at least July 2024, and targeted select Samsung Galaxy users in the Middle East.
Identified as CVE-2025-21042, the zero-day is an out-of-bounds write in libimagecodec.quram.so and has a critical severity rating. A remote attacker successfully exploiting it can execute arbitrary code on a target device.

According to researchers at Palo Alto Networks’ Unit 42, the LandFall spyware is likely a commercial surveillance framework used in targeted intrusions.
The attacks begin with the delivery of a malformed .DNG raw image format with a .ZIP archive appended towards the end of the file.
.jpg)
Source: Unit 42
Unit 42 researchers retrieved and examined samples that were submitted to the VirusTotal scanning platform starting July 23, 2024, indicating WhatsApp as the delivery channel, based on the filenames used.
From a technical perspective, the DNGs embed two main components: a loader (b.so) that can retrieve and load additional modules, and a SELinux policy manipulator (l.so), which modifies security settings on the device to elevate permissions and establish persistence.
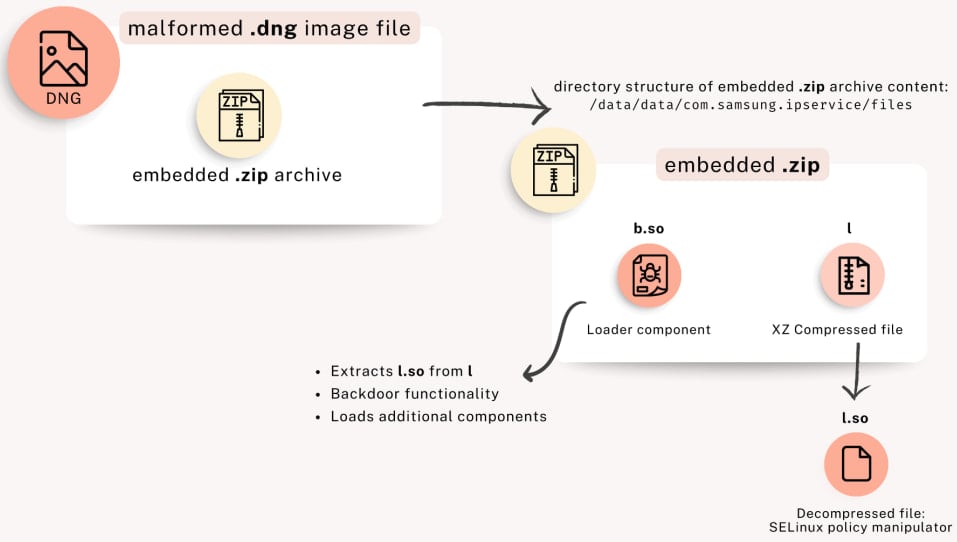
Source: Unit 42
According to the researchers, LandFall can fingerprint devices based on hardware and SIM IDs (IMEI, IMSI, the SIM card number, user account, Bluetooth, location services, or the list of installed applications.
However, additional capabilities observed include executing modules, achieving persistence, evading detection, and bypassing protections. Among the spying features, the malware counts:
- microphone recording
- call recording
- location tracking
- accessing photos, contacts, SMS, call logs, and files
- accessing the browsing history
According to Unit 42’s analysis, the spyware targets Galaxy S22, S23, and S24 series devices, as well as Z Fold 4 and Z Flip 4, covering a broad range of Samsung’s latest flagship models, excluding the latest S25 series devices.
It’s worth noting that LandFall and its use of DNG images is another case of broader exploitation seen recently in commercial spyware tools.
There have been exploitation chains in the past involving the DNG format for Apple iOS, with CVE-2025-43300, and also for WhatsApp, with CVE-2025-55177.
Samsung also fixed CVE-2025-21043 recently, which also impacts libimagecodec.quram.so, after WhatsApp security researchers discovered and reported it.
Source: Unit 42
Attribution murky
The data from the VirusTotal samples that the researchers examined indicate potential targets in Iraq, Iran, Turkey, and Morocco.
Unit 42 was able to identify and correlate six command-and-control (C2) servers with the LandFall campaign, some of them flagged for malicious activity by Turkey’s CERT.
C2 domain registration and infrastructure patterns share similarities with those seen in Stealth Falcon operations, originating from the United Arab Emirates.
Another clue is the use of the “Bridge Head” name for the loader component, a naming convention that is commonly seen in NSO Group, Variston, Cytrox, and Quadream products.
However, LandFall could not be confidently linked to any known threat groups or spyware vendors.
To protect against spyware attacks, apply security updates for your mobile OS and apps promptly, disable automatic media downloading on messaging apps, and consider activating ‘Advanced Protection’ on Android and ‘Lockdown Mode’ on iOS.

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
