Uptycs threat research team recently discovered “MacStealer,” a new information-stealing malware designed to target Apple’s macOS operating system. It aims to steal various sensitive information, including credentials stored in the:-
- iCloud KeyChain
- Web browsers
- Cryptocurrency wallets
- Potentially sensitive files
MacStealer is a malware-as-a-service (MaaS) distributed for $100, including premade builds enabling purchasers to spread the malware via Telegram as a command-and-control (C2) platform, making it a significant threat for exfiltrating data.
Specifically, this bug affects macOS versions Catalina and later runs on CPUs with M1 and M2 cores, which are the latest lineups from Apple.
In short, the latest macOS malware, capable of running on versions from macOS Catalina (10.15) to the latest Ventura (13.2), is reportedly being updated by malware authors to incorporate data capture functionalities from Apple’s Safari browser and Notes app, making it a significant threat to Apple users.

Capabilities of MacStealer
Discovered by Uptycs analysts on a dark web hacking forum at the beginning of the month, MacStealer is being promoted by the developer for a low price of $100. With this low price tag, they justify its affordability due to the lack of a builder and panel while promising the addition of advanced features in the future.
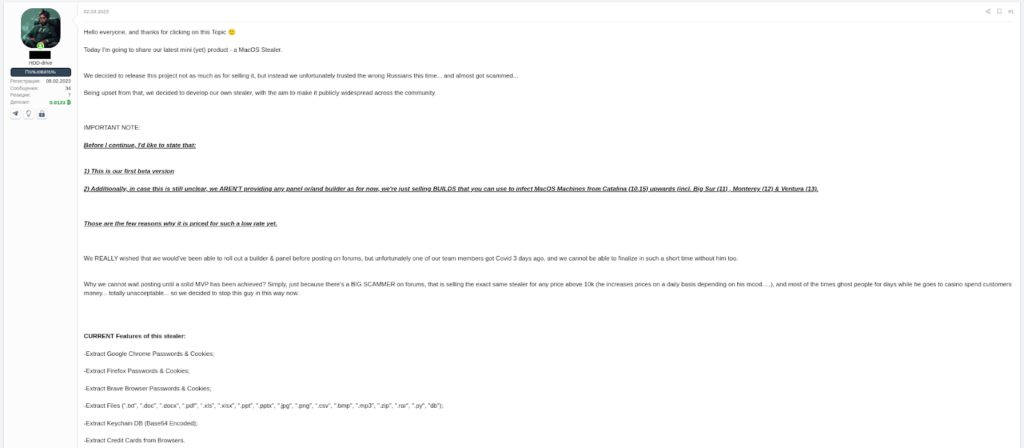
From compromised systems, MacStealer is capable of stealing the following information:-
- Account passwords from Firefox, Chrome, and Brave
- Cookies from Firefox, Chrome, and Brave.
- Credit card details from Firefox, Chrome, and Brave
- TXT files
- DOC files
- DOCX files
- PDF files
- XLS files
- XLSX files
- PPT files
- PPTX files
- JPG files
- PNG files
- CSV files
- BMP files
- MP3 files
- ZIP files
- RAR files
- PY files
- DB files
- Extract the Keychain database in base64 encoded form
- Collect System information
- Collect Keychain password information
- Coinomi cryptocurrency wallet data
- Exodus cryptocurrency wallet data
- MetaMask cryptocurrency wallet data
- Phantom cryptocurrency wallet data
- Tron cryptocurrency wallet data
- Martian Wallet cryptocurrency wallet data
- Trust wallet cryptocurrency wallet data
- Keplr Wallet cryptocurrency wallet data
- Binance cryptocurrency wallet data
Technical Analysis
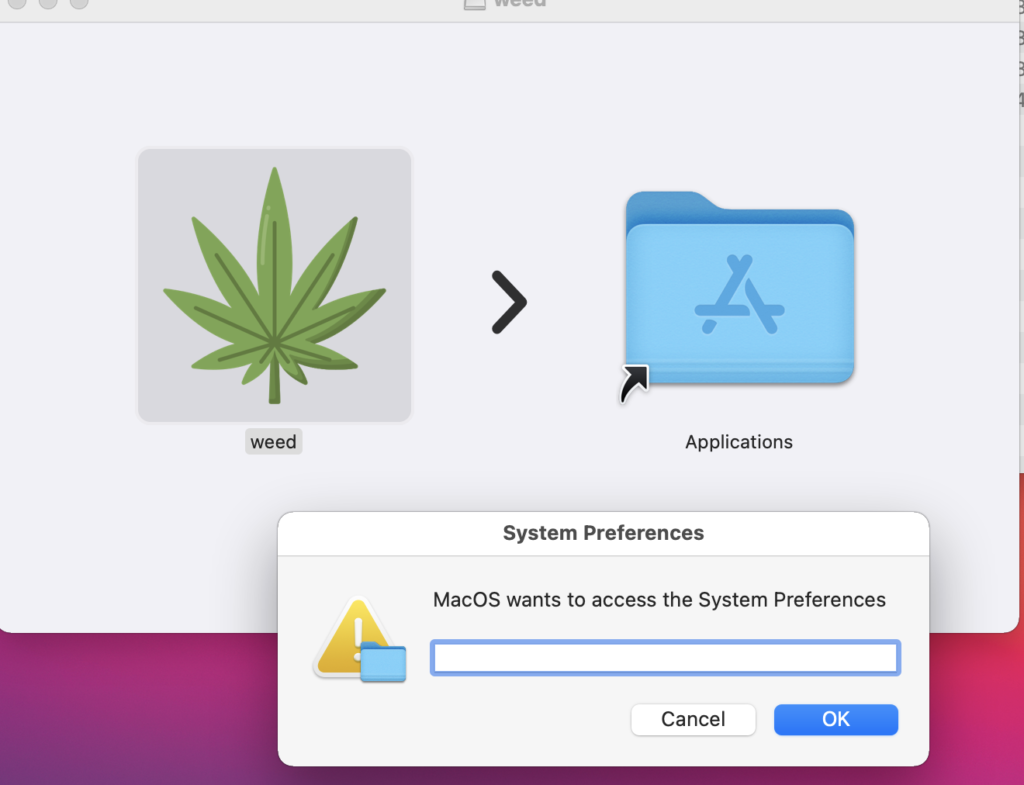
MacStealer, one of several recent info-stealers, is spread via a DMG file named “weed.dmg” and tricks macOS users into entering their passwords by posing as a fake prompt for accessing the System Settings app, further contributing to the already significant number of similar tools in circulation with the exact method of delivery remaining unknown.
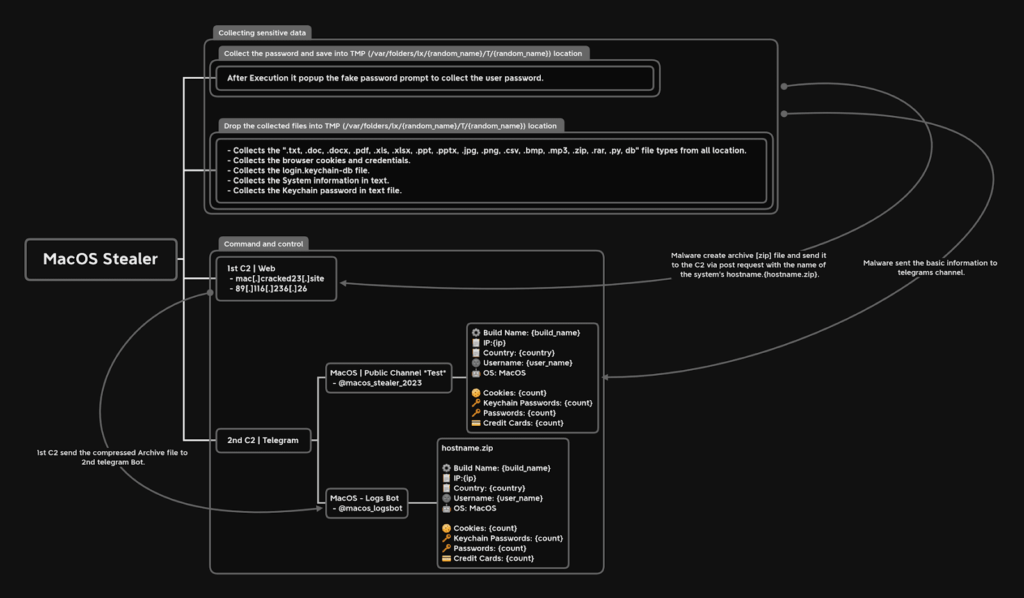
After collecting the mentioned data, MacStealer compresses the information into a ZIP file and sends it to remote command and control servers for retrieval by the threat actor while simultaneously alerting the operator of new data via a pre-configured Telegram channel, providing a quick and convenient way to download the ZIP file.
Recommendations
Here below, we have mentioned all the recommendations offered by the security researchers:-
- It is imperative that users remain vigilant and do not download files from untrusted websites.
- As a security precaution, it is recommended that users keep their operating systems and security software up to date.
- Do not use any used or basic passwords.
- Make sure to enable two-factor authentication.
- If you come across a link that appears to come from an unknown source, do not click it.
Building Your Malware Defense Strategy – Download Free E-Book
Related Read:



