A pair of malicious Rust crates masquerading as the popular fast_log library have been uncovered, harvesting private Solana and Ethereum keys from developers’ environments.
The impostor crates include legitimate-looking logging functionality to evade detection, while a hidden routine scans source files for wallet keys and exfiltrates them to a hardcoded command-and-control (C2) endpoint. Between them, the two crates accumulated 8,424 downloads before being removed from crates.io.
On May 25, 2025, the threat actors uploaded faster_log version 1.7.8 and async_println version 1.0.1 to crates.io, copying the README, repository links, and naming conventions of the genuine fast_log package.
Socket’s Threat Research Team identified two counterfeit packages—faster_log and async_println—published under the aliases rustguruman and dumbnbased.
Socket’s AI Scanner flagged faster_log as known malware after detecting typosquatting indicators and the presence of exfiltration code.
Within hours of Socket reporting the incident, Crates.io security—which operates in coordination with the Rust Security Response WG and the Rust Foundation—preserved the malicious files for analysis, removed the listings to block further downloads, locked the rustguruman and dumbnbased publisher accounts, and published an official advisory detailing their investigation and remediation steps.
Anatomy of the attack
Although the crates compile and function as basic logging libraries, they contain a “packer” module that:
- Scans Rust source files for three patterns:
- Bracketed byte arrays that could encode raw key material.
- Quoted Base58 strings of 32–44 characters, matching Solana key formats.
- Quoted 0x-prefixed 64-hex strings, typical of Ethereum private keys.
- Packages each match with its type, exact value, file path, and line number into a JSON payload.
- Sends the payload via an HTTP POST request to a Cloudflare Workers subdomain styled as a Solana RPC endpoint (hxxps://mainnet.solana-rpc-pool.workers.dev/).
Because the malicious crates depend only on standard libraries and the popular reqwest HTTP client, they operate identically across Linux, macOS, and Windows, and they can run both at application runtime and within CI pipelines.
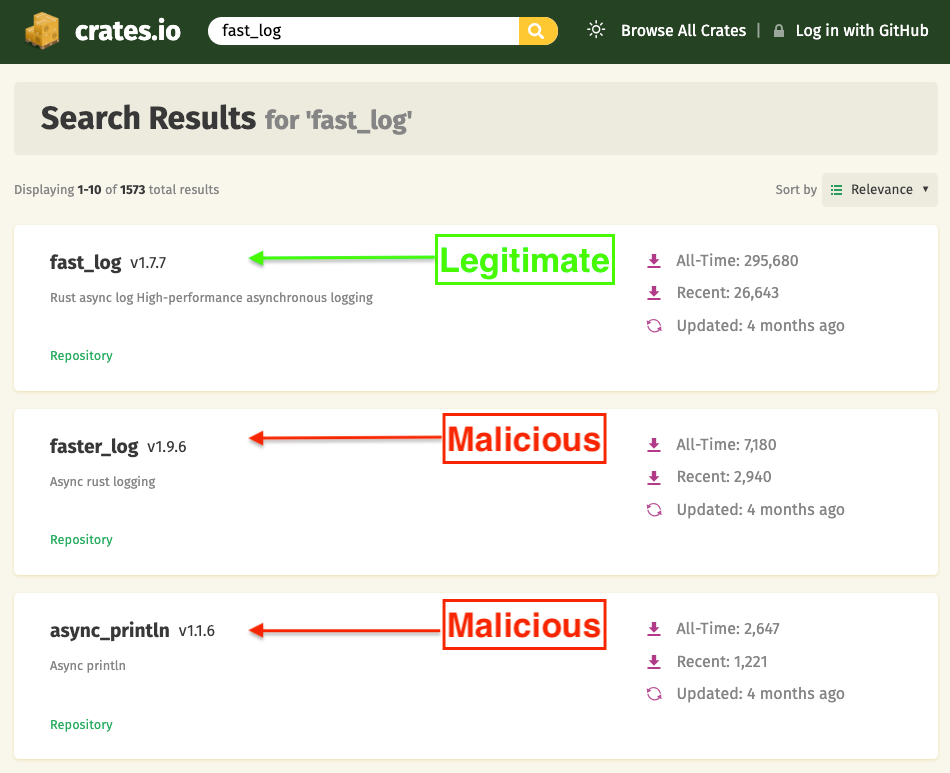
By copying the legitimate fast_log’s metadata and preserving core logging behavior, the attackers increased the likelihood of casual acceptance by developers.
Recommendations and outlook
This incident highlights the growing risk of supply-chain attacks driven by minimal code changes and name impersonation. Even a small malicious routine hidden in an otherwise benign library can compromise developer workstations and CI environments.
Organizations should treat this as a supply-chain security incident and take the following actions immediately:
- Remove any installations of faster_log or async_println from projects and build systems, and suspend any related CI runs.
- Rotate any secrets that might appear in source repositories, test fixtures, or configuration files, including Ethereum private keys, Solana seeds, and other credentials represented as quoted strings or byte arrays.
- Implement file-level secret scanning across developer laptops, CI servers, and repository hosting systems to detect the patterns observed in this campaign.
- Restrict egress traffic from development and CI networks, allowing only trusted outbound destinations.
- Create detection rules for HTTP POSTs to anomalous endpoints containing JSON payloads with “item_type” fields matching key-harvest patterns.
To defend against future impostor packages, security teams can deploy multi-layered solutions:
- Real-time pull-request scanning with tools like the Socket GitHub App to flag malicious code before merges.
- Pre-installation checks using CLI scanners that warn on impersonation and risky behavior.
- Browser extensions to annotate crates.io pages, highlighting suspicious metadata and typosquatting attempts.
- AI-assisted coding protections that intercept malicious package suggestions from language models and IDE plugins.
As ecosystems mature, attackers will refine their techniques—embedding malicious logic in build scripts or macros, rotating C2 endpoints, and leveraging geofencing to blend exfiltration with normal RPC traffic. Vigilance, strict secret hygiene, and layered defense-in-depth remain essential to securing modern development supply chains.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
