The Akamai Hunt Team has uncovered a new strain of malware that targets exposed Docker APIs with expanded infection capabilities.
First observed in August 2025 within Akamai’s honeypot infrastructure, this variant diverges from the June 2025 Trend Micro report by blocking other attackers from accessing the Docker API and delivering a modular payload rather than a cryptominer.
This advisory details the technical findings, contrasts the two variants, and provides indicators of compromise (IOCs) to support defensive measures.
As containerization proliferates, misconfigured Docker APIs have become an attractive attack surface.
Initial campaigns advertised in June 2025 used Tor-based downloads to deploy cryptocurrency miners.
The latest iteration shows the rapid evolution of threat actors: hijacking Docker hosts to gain SSH root persistence, evicting rival attackers, and potentially laying the groundwork for a botnet.
This report examines the infection chain, novel persistence mechanisms, and recommended detection and mitigation strategies. [Jump to detections]
Initial Threat Vector
In June 2025, Trend Micro’s Threat Intelligence Team reported malware exploiting unsecured Docker APIs on port 2375 to spin up an Alpine container, bind-mount the host filesystem, and execute a Base64-encoded downloader via Tor. That downloader fetched a shell script which:
- Installed
curlandtorsocks. - Retrieved an XMRig miner binary.
- Modified
/etc/ssh/sshd_configto permit root login. - Added an attacker’s public key to
/root/.ssh/authorized_keys. - Scheduled a cron job to ensure SSH persistence and miner execution.
This strain principally aimed to hijack compute cycles for cryptomining under Tor anonymity.
This identification is achieved by searching for ubuntu containers, as our data shows that many threat actors deploy ubuntu containers with cryptominers in them.
Akamai’s Variant: Expanded Capabilities
Persistent SSH Root Access and API Lockdown
During routine honeypot monitoring, the Akamai Hunt Team observed HTTP requests to a Docker API attempting container creation.
The decoded payload installed Tor, retrieved a docker-init.sh from an onion domain, and executed it on the host via a bind mount. Key distinctions include:
- SSH Persistence: The script appends an attacker’s ECDSA key to
/hostroot/root/.ssh/authorized_keysand reconfiguressshdto allow root logins. - API Access Denial: A cron job appended to
/hostroot/etc/crontabruns each minute, iterating throughfirewall-cmd,ufw,pfctl,iptables, andnftto block port 2375, preventing other attackers from exploiting the same Docker API. - Modular Payload Delivery: Instead of a miner, the script pulls a compressed Go-based dropper and secondary binaries via Tor, enabling further reconnaissance and lateral propagation.
The downloaded Go dropper parses utmp to identify logged-in users, while the secondary binary:
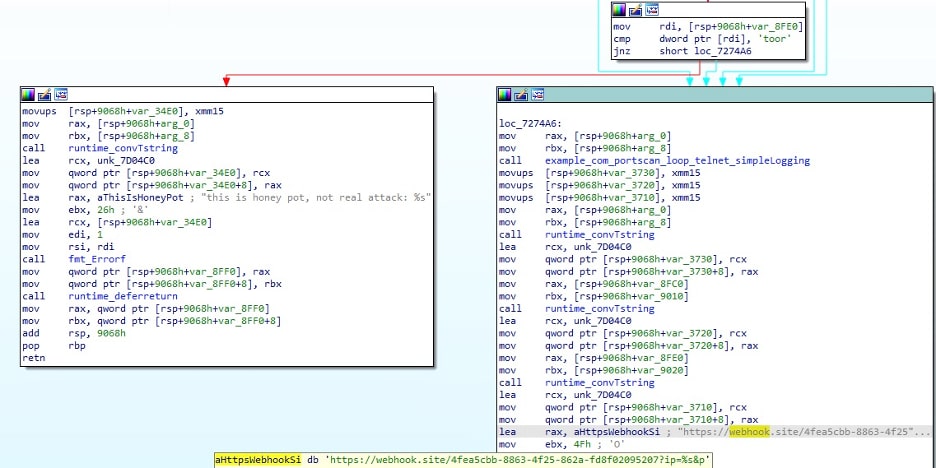
- Uses Masscan to scan for additional exposed Docker APIs (port 2375)
- Includes dormant Telnet (port 23) and Chrome Debugging (port 9222) modules for future expansion
- Posts scan results to a Tor-hosted C2 endpoint, suggesting a modular botnet architecture
Mitigations
Detection techniques for this malware and similar API-based threats include:
- Monitoring Docker API interactions for immediate use of installer and downloader commands.
- Alerting on inbound connections to ports 2375, 9222, and 23 from untrusted networks.
- Inspecting new containers for host filesystem mounts or Base64-encoded commands.
- Tracking abnormal Tor or onion-domain network traffic.
- Detecting sudden cessation of service listeners on expected ports (e.g., Docker daemon).
To reduce exposure and risk:
- Network Segmentation: Restrict Docker API access to trusted management subnets.
- Minimize Exposed Services: Avoid binding Docker, Chrome debugger, or Telnet ports to public interfaces.
- Secure Default Credentials: Rotate default passwords on new devices and change Telnet/SSH defaults immediately.
- Least Privilege: Run Docker daemons under non-root users where possible and enforce strict API authentication.
This new Docker-API malware variant underscores the speed at which adversaries adapt known exploits to deepen persistence and prevent competing intrusions.
By combining SSH root backdoors, API lockdown tactics, and modular payloads, the threat actor has elevated a simple cryptominer campaign into a multi-stage intrusion framework.
Defenders must audit container environments rigorously, enforce network controls, and monitor behavioral anomalies to stay ahead of such evolving threats.
Continuous threat hunting—as exemplified by Akamai Hunt—remains critical for early detection and remediation.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.




