A successful brute-force attack on a PostgreSQL database exploited a feature that allowed command execution, where the attacker created a superuser role, dropped files to eliminate competition and gain persistence, and ultimately deployed cryptocurrency miners.
The attack demonstrates the severe consequences of weak passwords and the potential for unauthorized access to a database to lead to significant security breaches.


An attacker successfully breached the system through a brute-force attack on the PostgreSQL database. After gaining access, they created a new superuser account with elevated privileges to maintain persistence.
Free Webinar on Detecting & Blocking Supply Chain Attack -> Book your Spot
They then stripped the initial compromised user of superuser rights to limit potential damage from future attacks.
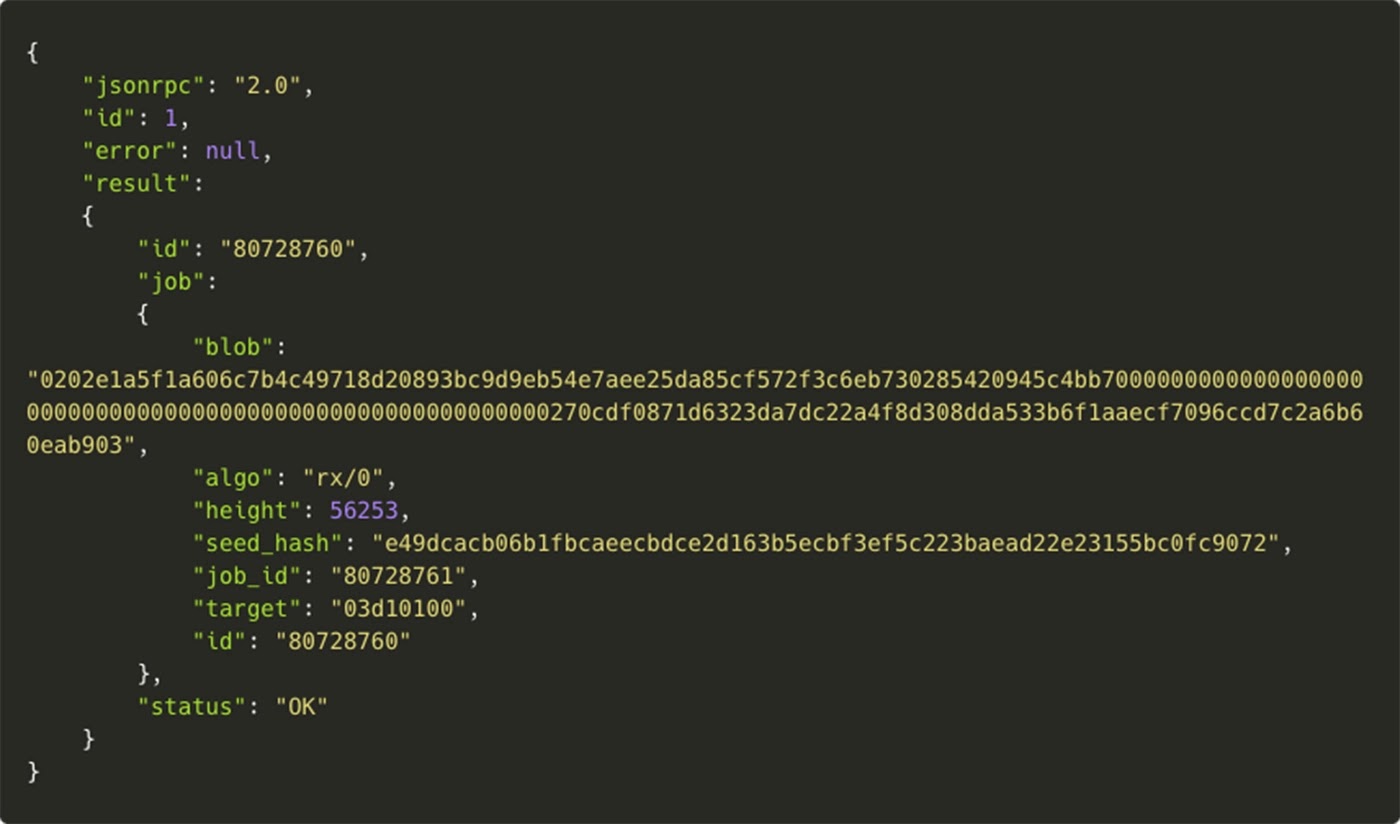
To gather information about the system, the attacker executed commands to locate the authentication configuration file, determine the PostgreSQL server version, and run system commands like `uname` and `whoami`.

The threat actor leverages a temporary table to execute shell commands and store the output by establishing a TCP connection to a remote server to download two malicious payloads, pg_core and pg_mem.
The first payload, pg_core, is a cryptominer that mines cryptocurrency, while the second payload, pg_mem, is a dropper that deploys the XMRIG cryptominer, memory.
Both payloads are designed to evade detection by removing logs, killing competing malware processes, and creating persistence through cron jobs. The threat actor also modifies the pg_hba configuration file to allow unauthorized connections.
A recent Shodan search revealed over 800,000 publicly accessible PostgreSQL databases on the internet, highlighting a significant security risk and making them vulnerable to brute-force attacks and potential exploitation.
This discovery underscores the urgent need for organizations to implement robust security measures to protect their database servers from unauthorized access.
The attackers exploited a vulnerability in the Postgres database to gain initial access to the target system, which aligns with the T1190 technique, which involves exploiting public-facing applications to compromise systems.
According to AquaSec, by leveraging this vulnerability, the attackers were able to bypass security measures and establish a foothold within the target environment.

The attacker initiates a targeted attack against a PostgreSQL database server by exploiting a vulnerability in the database to execute shell commands, create a new user account with elevated privileges, and manipulate existing user roles.
To maintain persistence, they schedule a task to run a malicious script and delete evidence of their activity, and then leverage the elevated privileges to execute commands as a superuser.
By guessing the database credentials, they gain unauthorized access by collecting sensitive data, and the attacker downloads malicious files from a remote server and uses web protocols to establish communication, ultimately hijacking system resources for cryptocurrency mining.
Are you from SOC and DFIR Teams? Analyse Malware Incidents & get live Access with ANY.RUN -> Get 14 Days Free Acces


