MetaStealer is a popular piece of malware that came out in 2022, levering previous code base from RedLine. Stealers have become a very hot commodity in the criminal space, so much so that there is competition between various groups.
Threat actors have primarily used malspam as an infection vector to drop MetaStealer as well as cracked software via stolen YouTube accounts, but it was at least once previously seen in a malvertising campaign.
In the past week, we observed some malicious ads that weren’t dropping FakeBat or PikaBot, but rather a different payload that we recognized as MetaStealer. Interestingly, in early December, the malware authors behind MetaStealer gave an interview and announced that they were about to release a new and improved version of their tool.
Distribution
We captured two different ads for Notepad++ and AnyDesk via Google searches:
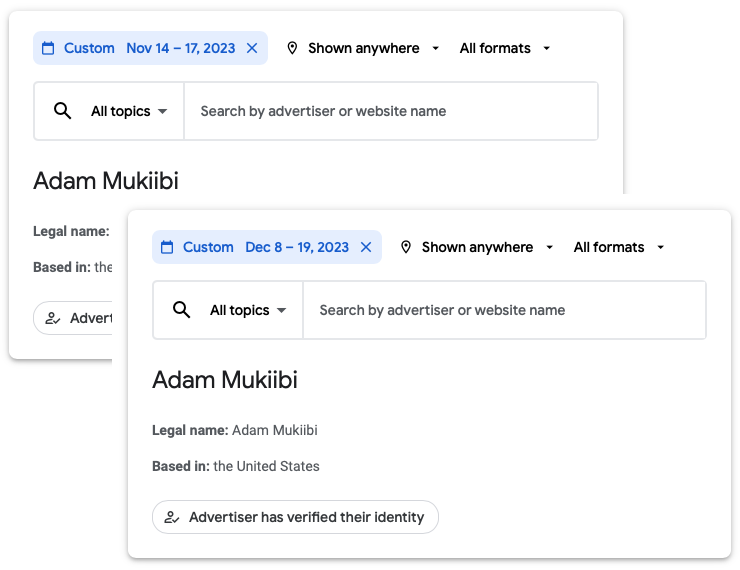
According to the Google Ads Transparency Center, one of the campaigns ran in November and December, during specific dates:
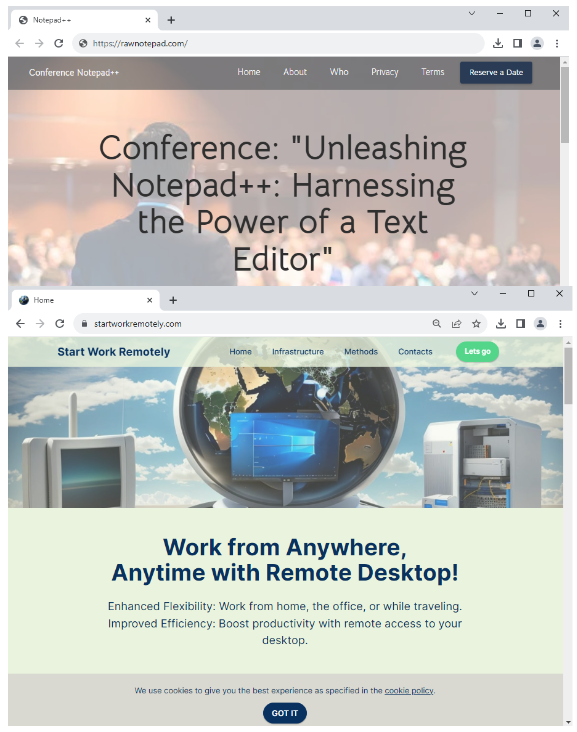
Two domains have been setup as both decoy and landing pages. If you were to browse to those sites directly, you would see content that looks like it was generated automatically. Note how the two pages have a similar template.
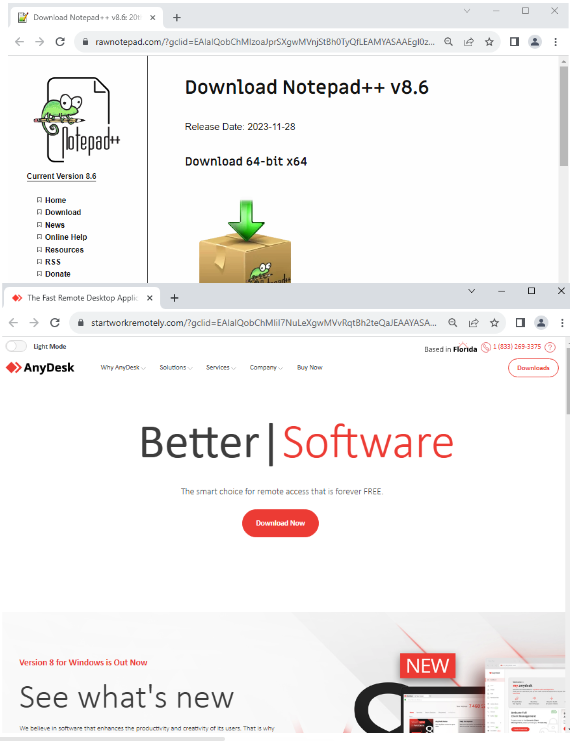
However, users that clicked on the ads and met the selection criteria will get a malicious landing page and a download link:
Payload
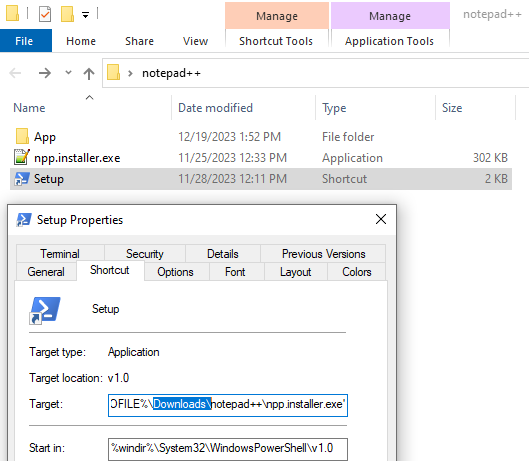
The November payload contained a shortcut launching PowerShell that used a hardcoded path to the Downloads folder (would fail if the file was extracted in another directory):
The December campaign got rid of the PowerShell and the malicious DLL was recompiled:
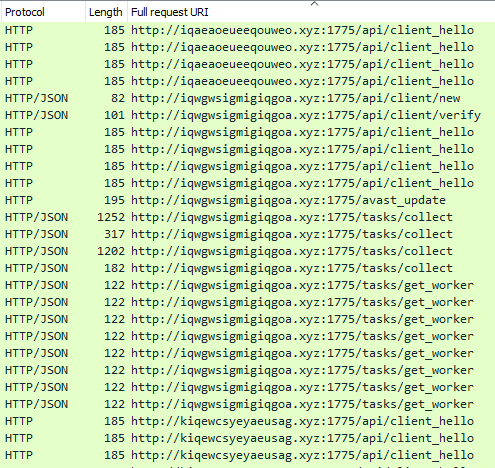
Based on network traffic activity alone, it appears that both payloads are still the MetaStealer from the 3.x branch:
For an in-depth look at MetaStealer, check out this article by Russian Panda.
Conclusion
The developers of MetaStealer are improving their product and we are likely to see more of their customers distributing it. Stealers can serve multiple purposes but tend to revolve around items that criminals can easily monetize. Crypto wallets are usually quite coveted, but so are credentials for various online services. And finally, stealers can also be used by initial access brokers, paving the path for ransomware actors.
We have reported the malicious ads to Google and have already blocked the infrastructure behind these campaigns.
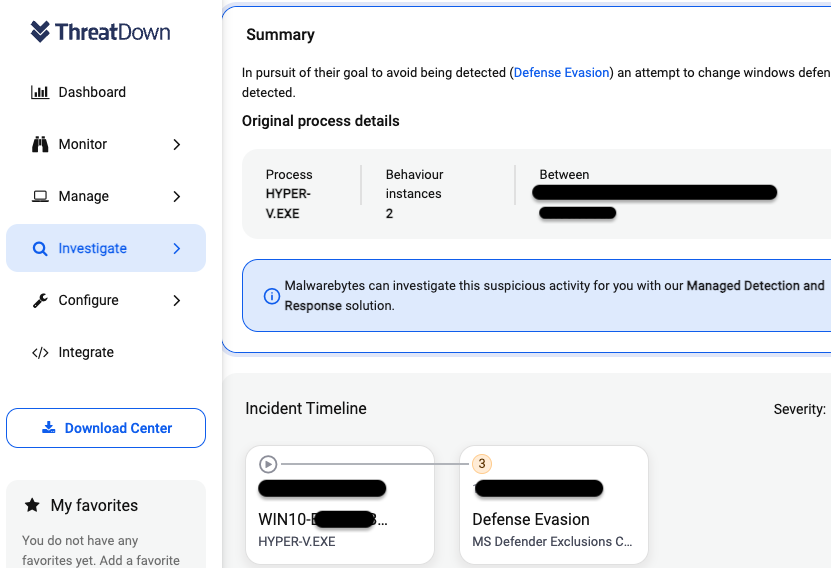
ThreatDown, powered by Malwarebytes, detects this threat as Trojan.MetaStealer.Generic. The Endpoint Detection and Response (EDR) can also see the process activity tied to this attack:

Additionally, the newly released Incident Timeline feature can alert you of an active intrusion attempt which our Managed Detection and Response team can assist you with.
Indicators of Compromise
Malicious domains
rawnotepad[.]com
startworkremotely[.]com
Payload URLs
rawnotepad[.]com/notepad++.zip
startworkremotely[.]com/Anydesk.zip
Payload hashes
949c5ae4827a3b642132faf73275fb01c26e9dce151d6c5467d3014f208f77ca
99123063690e244f95b89d96759ec7dbc28d4079a56817f3152834047ab047eb
c5597da40dee419696ef2b32cb937a11fcad40f4f79f9a80f6e326a94e81a90f
MetaStealer C2s
wgcuwcgociewewoo[.]xyz
ockimqekmwecocug[.]xyz
kiqewcsyeyaeusag[.]xyz
cewgwsyookogmmki[.]xyz
startworkremotely[.]com
csyeywqwyikqaiim[.]xyz
iqaeaoeueeqouweo[.]xyz
mmswgeewswyyywqk[.]xyz
accounts[.]google[.]com
iqwgwsigmigiqgoa[.]xyz
