Recently surfaced Money Message ransomware group has claimed responsibility for targeting not only MSI but also several other companies across different countries including the US, the UK, and Bangladesh.
Micro-Star International or MSI, a Taiwanese multinational information technology corporation, has fallen victim to a ransomware attack by a relatively new group called Money Message.
The attack has been confirmed by MSI through postings on their website and the Taiwanese stock exchange. Money Message is now demanding a ransom of $4 million to prevent the leaking of MSI’s confidential data.
MSI’s press release, however, seems to downplay the severity of the situation, stating that the affected systems have resumed normal operations with no significant impact on financial business.
Regardless, Money Message currently claims to hold critical information about MSI’s hardware, including the BIOS source code for motherboards. If the ransom is not paid, the group has threatened to leak this data, which could have serious repercussions for MSI in the future.

The Money Message ransomware group, responsible for the recent attack on MSI, has made additional claims of compromising other companies. The following entities are reportedly among the victims:
- Hawaii Self Storage, USA
- Mid-American Glass, USA
- Biman Bangladesh Airlines
- LPA Group Plc, United Kingdom
- Golden Bear Insurance Company, USA
- Pharmerica.com & BrightSpring Health Services
Money Message has set a countdown timer for over 100 hours on their website, indicating that they plan to release the 27GB of data to the public once the timer ends.
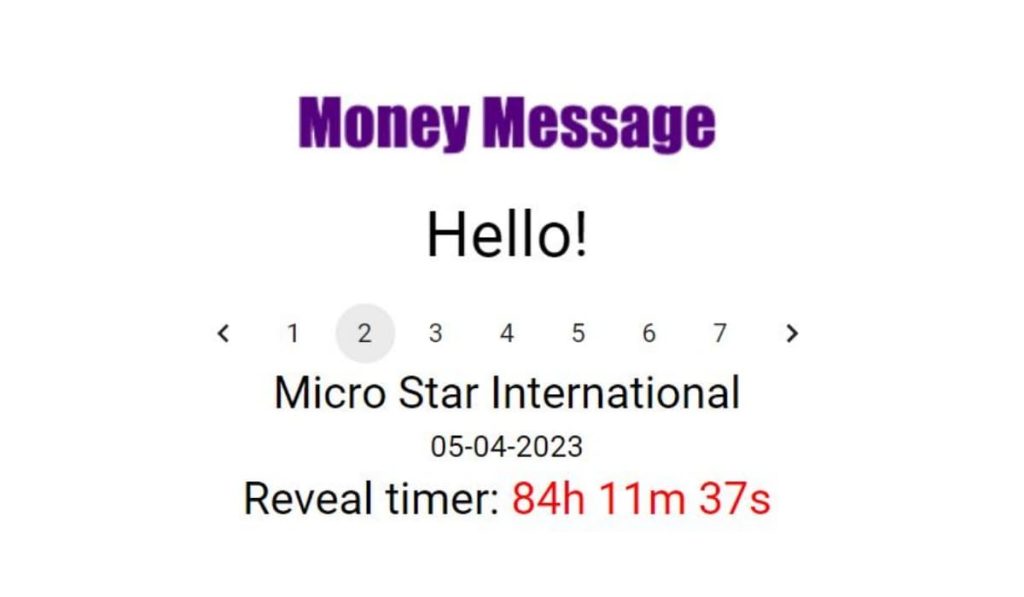

Money Message is a relatively new group, with their first major hack being reported by Zscaler’s Threat Labs on March 29th, 2023, just a day before MSI’s attack. The group’s website boasts a list of seven pages of successful ransomware attacks on various targets, ranging from small businesses to large firms, and even a Bengali airline.
It remains unclear whether Money Message will follow through with its threat to leak MSI’s data, or if MSI intends to pay the ransom. In the meantime, MSI has urged users to only download software from official links on their website, indicating heightened caution in the aftermath of the attack.
The situation continues to unfold, and MSI’s response to the ransomware attack will be closely watched by the cybersecurity community.
RELATED NEWS
- LockBit Ransomware Hits SpaceX Contractor
- New Rorschach Ransomware Targeting US- Firms
- Hackers Exploit MSI Afterburner to Deliver Coin Miner
- UK Criminal Records Office Hit by Ransomware Attack
- Western Digital Breach – Hackers Enter Internal Systems