Security researchers have uncovered a novel Bluetooth tracking vulnerability in Apple’s Find My network – the system powering AirTags and device-finding capabilities across iPhones, iPads, and Macs.
Dubbed “nRootTag,” the attack transforms nearly any Bluetooth-enabled computer or smartphone into an invisible tracking beacon using Apple’s infrastructure.
With over 1.5 billion active Apple devices globally, this exploit threatens to weaponize the world’s largest device-locating network for unauthorized surveillance.
Exploiting Find My’s Offline Finding Protocol
The attack exploits foundational design choices in Apple’s Find My offline finding system, originally developed to help recover lost devices anonymously.
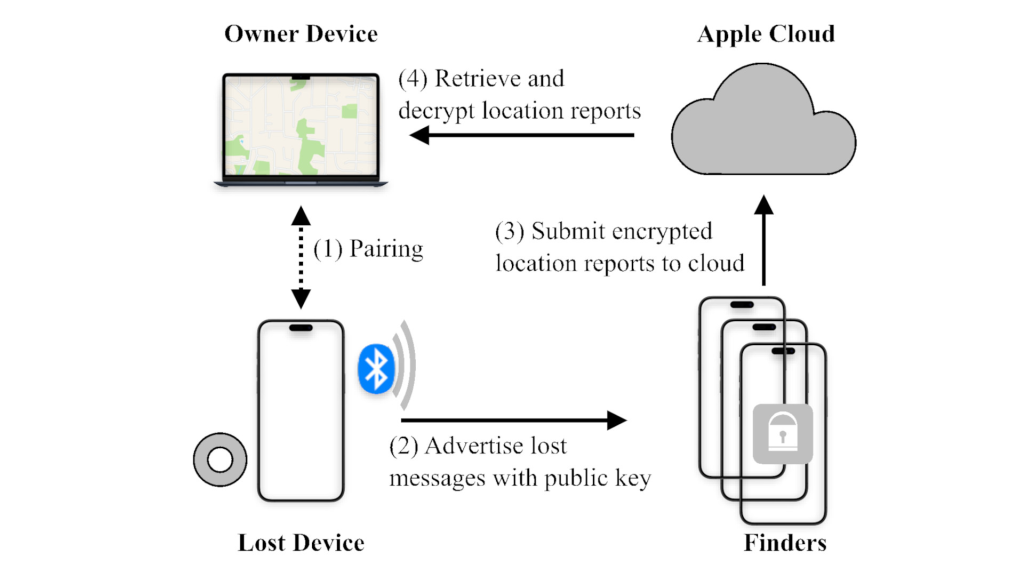
When an AirTag separates from its owner, it broadcasts encrypted Bluetooth Low Energy (BLE) “lost messages” containing public key hashes.
Nearby Apple devices automatically relay these signals to Apple’s servers along with location data, creating a crowd-sourced tracking network.
Researchers discovered that Apple does not authenticate whether lost messages originate from genuine Apple devices.
This oversight allows malicious actors to inject spoofed BLE advertisements into the network.
“Any device broadcasting these signals becomes trackable through Find My, regardless of manufacturer,” explains the research team behind nRootTag.
How nRootTag Bypasses Security Measures
The attack architecture operates through three stages compromised devices, server infrastructure, and cryptographic brute-forcing.
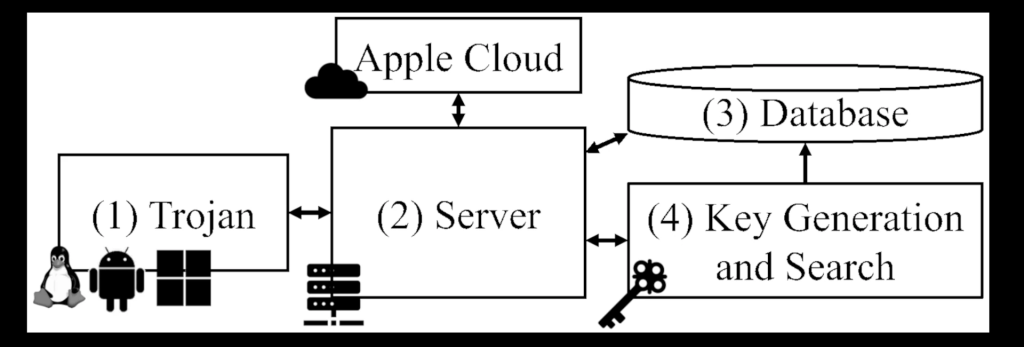

First, malware running on a target computer (requiring no special permissions) harvests its Bluetooth MAC address and requests a matching public/private key pair from an attacker-controlled server.
This server either precomputes possible combinations using rainbow tables or performs on-the-fly brute-force searches at scale.
Once paired, the compromised device broadcasts spoofed Apple-compatible BLE signals. Nearby iPhones then unwittingly relay its location to Apple’s servers.
Attackers retrieve this data by querying Apple’s API with the public key hash and decrypting reports using their held private key.
Testing showed a 90% success rate in pinpointing devices within minutes at an operational cost under $5.
Cross-Platform Vulnerability and Computational Power
nRootTag’s danger stems from its platform-agnostic nature. While demonstrated on Linux, Windows, and Android systems, researchers warn that smart appliances, medical devices, and other IoT products with Bluetooth capabilities could also be co-opted.
The team benchmarked GPU clusters to determine attack feasibility, finding consumer-grade hardware like NVIDIA’s RTX 3080 sufficient for rapid key generation.
However, data center-grade A100 and H100 GPUs reduced search times from hours to minutes.
Apple addressed the vulnerability in recent iOS, macOS, and watchOS updates (versions 15.2–18.2). Patches now validate device signatures in Find My network relays.
Nevertheless, researchers emphasize that billions of unpatched devices remain vulnerable. “As long as one outdated iPhone exists near a tracked device, the attack succeeds,” the paper notes.
They urge enterprises to audit Bluetooth-enabled assets and implement network monitoring for anomalous BLE traffic.
The researchers credited Apple’s security team for their collaborative response but warn that third-party tracking networks could replicate similar exploits.
Funded by NSF and cybersecurity initiatives, the study underscores growing privacy risks in crowd-sourced location services.
With Bluetooth permeating modern tech, nRootTag highlights how convenience-focused designs can inadvertently enable mass surveillance.
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free
