In a year-end tradition that has become all too familiar for cybersecurity defenders, researchers have uncovered a novel attack vector targeting Microsoft Entra ID that weaponizes legitimate OAuth 2.0 authentication flows to harvest privileged access tokens.
The technique, dubbed “ConsentFix” by PushSecurity, represents an evolution of the ClickFix social engineering paradigm, enabling threat actors to bypass device compliance checks and Conditional Access policies by exploiting the authorization code flow in first-party Microsoft applications.
The attack methodology fundamentally subverts how native public applications like the Microsoft Azure CLI authenticate users.
When a victim visits a malicious website, the attacker generates a legitimate Microsoft Entra login URI targeting the “Microsoft Azure CLI” client application and “Azure Resource Manager” resource.
This initiates the standard OAuth 2.0 authorization code flow, where the application would typically create a listener on a random high port (reply URI) to receive the authentication response.
In legitimate scenarios, after successful authentication, Entra ID redirects the user to localhost with critical parameters: the code (authorization code) and optional state parameter.
The Azure CLI application captures this redirect and redeems the code for bearer tokens. However, in the ConsentFix attack, no application listens on localhost, causing a browser error but the URI still contains the sensitive authorization code, which the attacker manipulates the user into providing via drag-and-drop or copy-paste actions.
Security researcher John Hammond demonstrated an improved version within days of the initial disclosure, eliminating manual copy-paste requirements and enabling pure drag-and-drop extraction.
Once obtained, the attacker redeems the code from their infrastructure, acquiring access tokens, ID tokens, and potentially refresh tokens that grant unfettered access to Azure Resource Manager and other cloud resources.
Detection Through Anomaly Correlation
Forensic analysis reveals distinctive artifacts in Entra ID sign-in logs. Each successful attack generates two events: an initial interactive sign-in representing the victim’s authentication, followed by a non-interactive sign-in from the attacker’s infrastructure during token redemption.
While the authorization code UTI differs from the bearer token UTI breaking a potential correlation mechanism the SessionId remains consistent across both events.
Effective detection requires linking events sharing identical SessionId, ApplicationId, and UserId, with the second event occurring within approximately ten minutes of the first.
The temporal threshold proves critical: legitimate automated scenarios like GitHub Codespaces redeem codes within seconds, while social engineering attacks introduce human-delayed intervals.
Additionally, legitimate Azure CLI usage shows both sign-ins originating from the same IP address, whereas attacks exhibit geographic dispersion between victim and attacker infrastructure.
While initial reports focused on Microsoft Azure CLI (Application ID: 04b07795-8ddb-461a-bbee-02f9e1bf7b46), the vulnerability extends to numerous pre-consented first-party applications accepting localhost redirects.
High-risk targets include Microsoft Azure PowerShell, Visual Studio, Visual Studio Code, and MS Teams PowerShell Cmdlets. Security researchers at EntraScopes.com have cataloged the full spectrum of affected applications, including development and test URLs that lack public resolvability.
Mitigations
Organizations face a matrix of defensive options balancing deployment complexity against mitigation effectiveness.
The lowest-effort approach involves requiring explicit user assignment for affected service principals, limiting the attack audience but demanding comprehensive identification of legitimate CLI users.
Conditional Access policies can block CLI tool access entirely, excluding authorized personnel, though this requires meticulous baseline analysis in report-only mode.
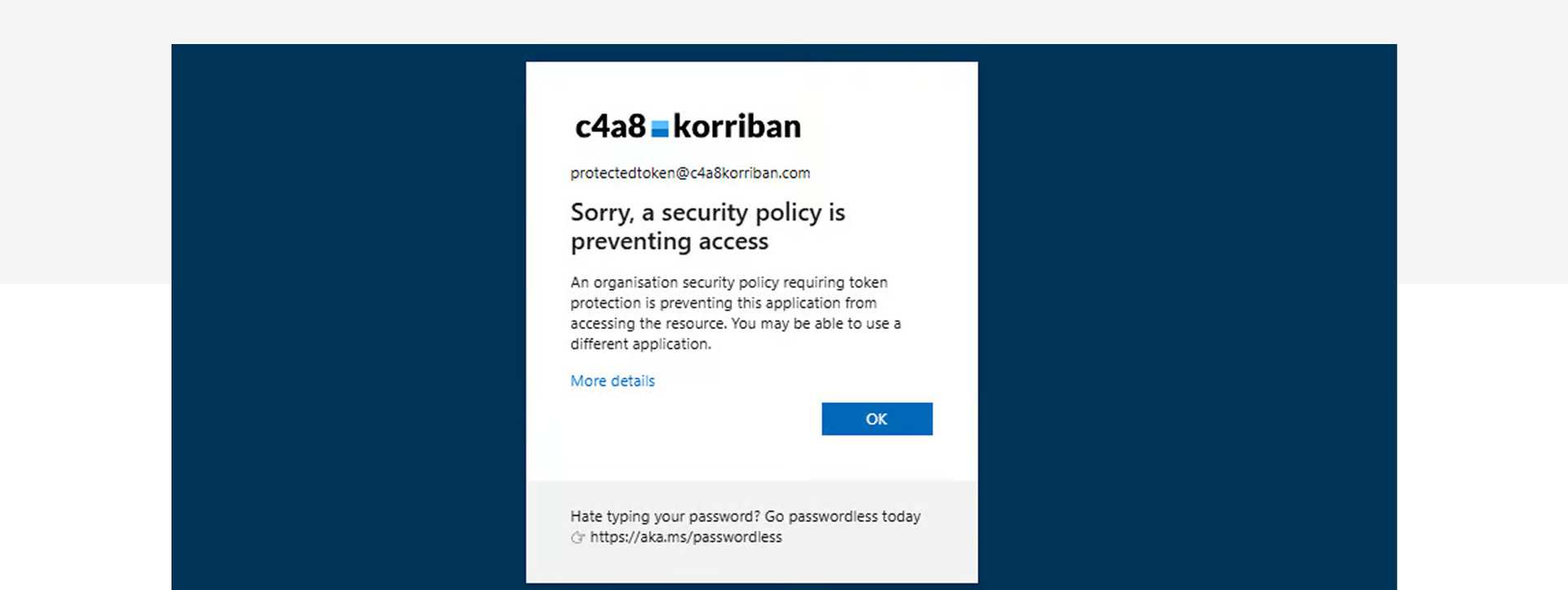
The most robust defense leverages Microsoft Entra ID’s Token Protection feature, requiring proof-of-possession through the Web Account Manager (WAM) broker on Windows platforms. When enforced, browsers cannot establish the secure channel necessary for code redemption, completely neutralizing ConsentFix attacks.
However, scope remains limited to specific Microsoft 365 resources, with Azure management scenarios still pending official support despite client-side WAM availability in current Azure CLI and PowerShell versions.
For broader protection, Global Secure Access with compliant network checks can block subsequent token issuance using stolen refresh tokens, though this fails to prevent initial code redemption.
The chicken-and-egg problem of device management requires careful exclusion policies for Intune and other management services.
As red teams rapidly weaponize these techniques and threat actors adapt them for phishing campaigns, defenders must immediately audit sign-in patterns for anomalous SessionId correlations, implement user assignment controls for CLI applications, and evaluate Token Protection readiness.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
