The cybersecurity researchers at Cisco Talos recently affirmed that threat actors are targeting the widely-used Microsoft 365 cloud-based productivity platform through the Greatness phishing platform, and not only that, even they also noticed an uncertain surge between December 2022 and March 2023.
Experiencing a notable surge in operations, the ‘Greatness’ Phishing-as-a-Service (PhaaS) platform has set its sights on organizations utilizing Microsoft 365 in the countries like:-
- The United States
- Canada
- The U.K.
- Australia
- South Africa
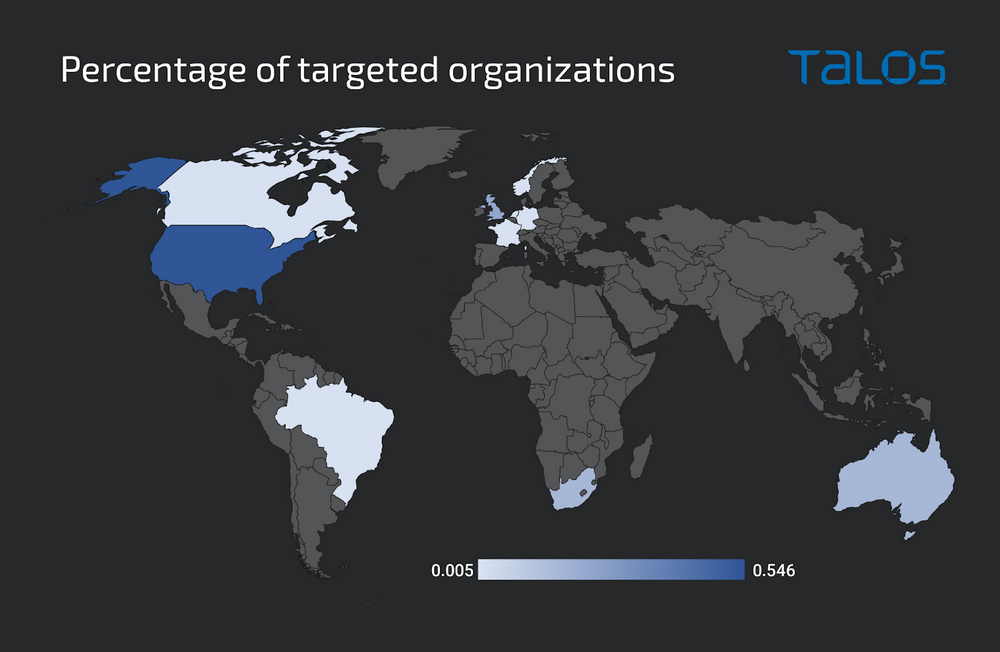
Here below, we have mentioned the sectors and industries from where the victims are mainly targeted, and the majority of them are located in the United States:-
- Manufacturing
- Healthcare
- Technology
- Education
- Real estate
- Construction
- Finance
- Business services
Attack Flow of Greatness
A complete Phishing-as-a-Service named “Greatness” offers all the necessary tools to effectively carry out a phishing campaign. Users only need to access its admin panel through an API key and provide the target email list to initiate an attack.


By providing the essential infrastructure, such as hosting the phishing page and generating the HTML attachment, the PhaaS platform empowers affiliates to customize email content and modify default settings.
After sending a phishing email with an HTML attachment, the service executes an obfuscated JavaScript code in the browser, which contacts the “Greatness” server to retrieve the phishing page.
Also, it injects the target company’s logo and background image from their authentic Microsoft 365 login page automatically.

After obtaining the victim’s password, the PaaS will simulate the victim’s identity to log in to Microsoft 365 and ask the victim to authenticate using the MFA method specified by Microsoft 365 if enabled.
The service receives MFA and completes the login process to collect session cookies, which are then delivered to the affiliate through Telegram or the web panel.
In total, there are three components that the service contains, and here below we have mentioned them:-
- A phishing kit
- The service API
- A Telegram bot or email address
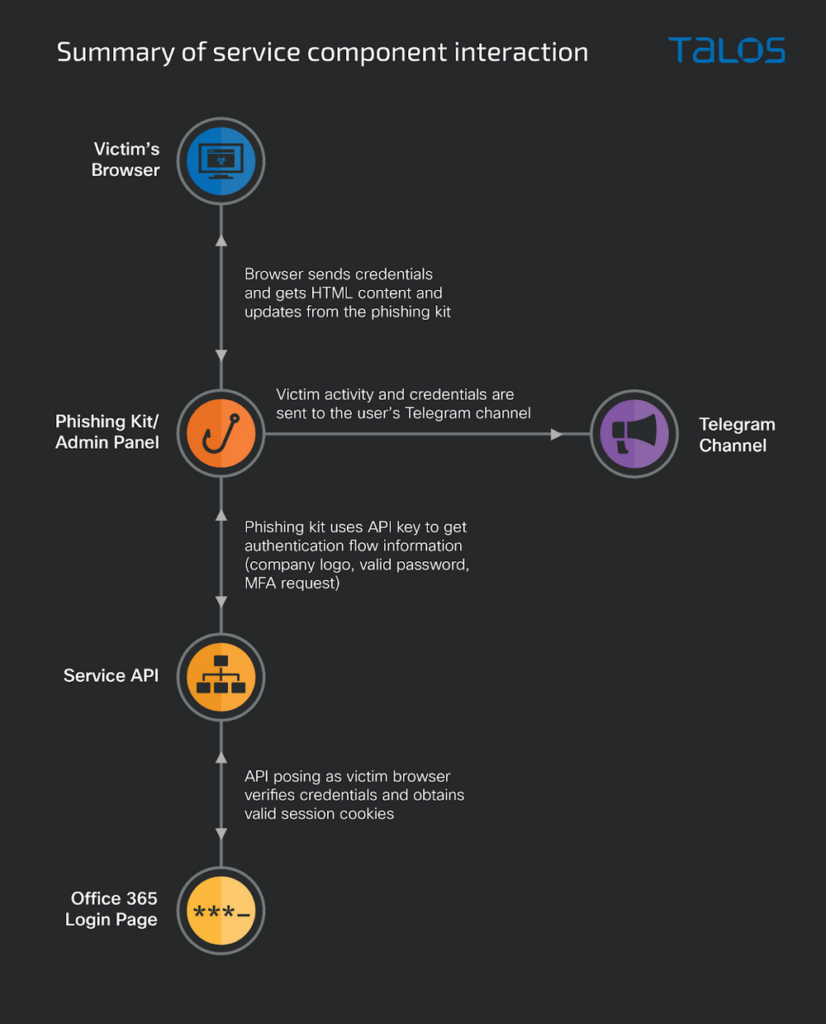
To utilize Greatness, affiliates require a valid API key, without which the phishing page won’t load, and they can configure their API key in the panel.
The service API collaborates with the phishing kit to execute a “man-in-the-middle” attack by validating the affiliate’s key, blocking unauthorized IP addresses, and facilitating seamless communication with the actual Microsoft 365 login page, enabling the collection of victim information in real-time.
By exploiting the PaaS affiliate’s ability to extract usernames, passwords, and even authenticated session cookies (especially in cases of MFA usage), the inclusion of a Telegram bot ensures swift notification of valid cookies, enabling prompt access for the attacker to high-value targets.
Moreover, the threat actors also use the stolen credentials to perform several other illicit activities like deploying ransomware or breaching corporate networks.
Struggling to Apply The Security Patch in Your System? –
Try All-in-One Patch Manager Plus

