Security researchers have discovered a sophisticated phishing technique that weaponizes invisible Unicode characters embedded within email subject lines using MIME encoding—a tactic that remains largely unknown among email security professionals.
The discovery reveals how attackers are evolving their evasion methods to bypass automated filtering systems while maintaining complete readability to end users.
During routine malware analysis of messages intercepted in recent days, security analysts observed a peculiar phishing email whose subject line displayed normally when opened in Outlook, yet contained hidden anomalies when examined in the message list view.
Initial inspection suggested the presence of invisible characters, a hypothesis that email header examination quickly confirmed.
Decoding the Hidden Threat
The email subject employed RFC 2047 MIME encoded-word formatting, a standard mechanism for transmitting non-ASCII text in email headers.
The malicious subject consisted of two separate encoded-word segments, each containing UTF-8 character set data processed through Base64 encoding.
When decoded, the strings revealed multiple instances of the soft hyphen character—Unicode code point U+00AD—strategically interspersed throughout the text.
The soft hyphen, more commonly recognized as the HTML entity, serves legitimate purposes in document formatting for controlling hyphenation points.
However, most email clients including Outlook render soft hyphens as invisible characters, making them imperceptible to human readers while remaining technically present in the message structure. This created an ideal obfuscation vector for threat actors seeking to evade detection mechanisms.
The attackers employed a dual-layered evasion strategy by combining MIME encoding with soft hyphen insertion across multiple encoded-word segments.
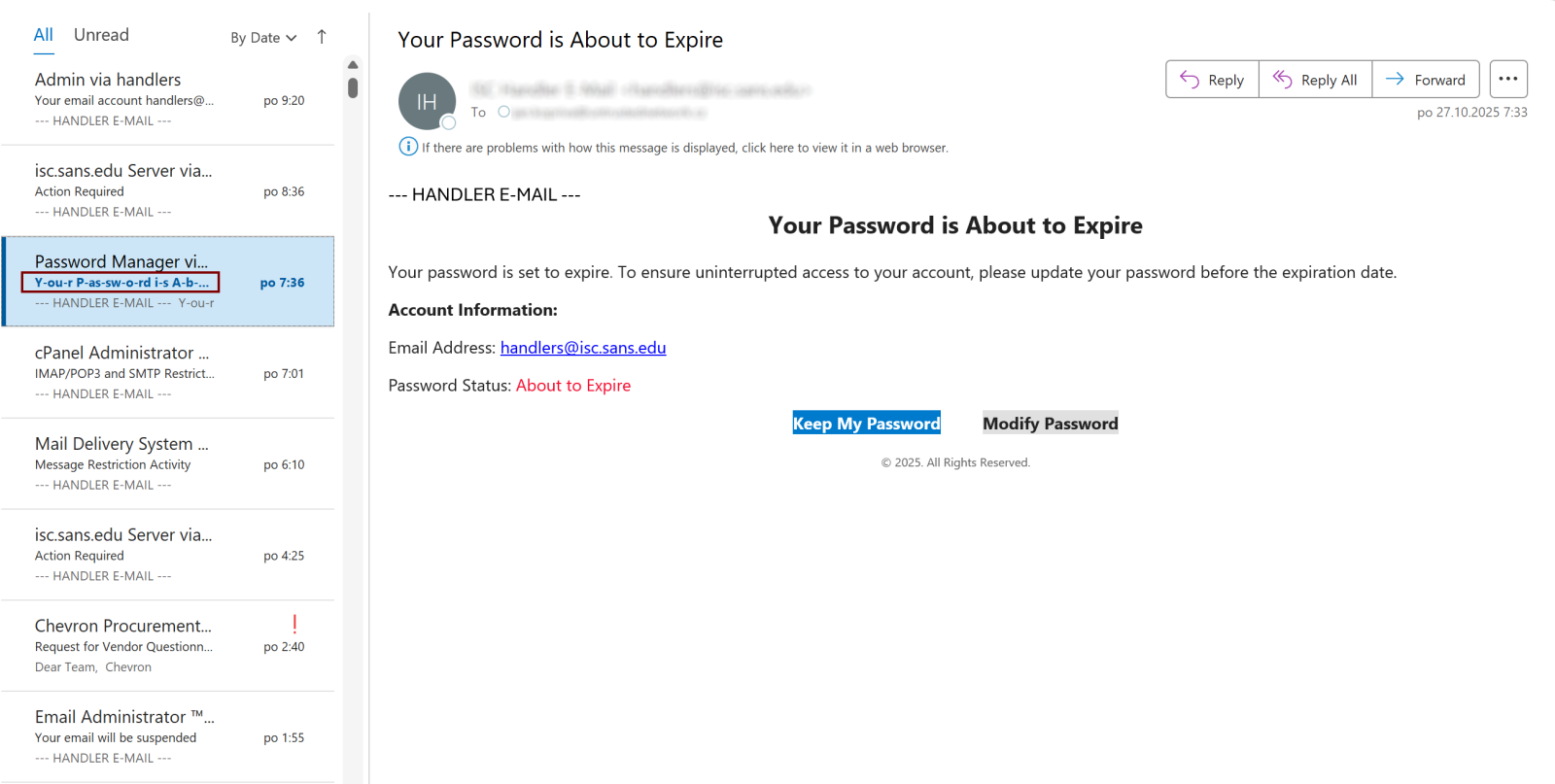
This approach fragments potentially malicious keywords into visually unrecognizable patterns that bypass signature-based filtering rules designed to detect known phishing indicators.
The subject line remained perfectly readable to recipients while appearing algorithmically corrupted to security systems.
An Underreported Vulnerability
What distinguishes this campaign is the unusual application of invisible character obfuscation specifically to email subject lines.
While Microsoft Threat Intelligence documented in 2021 that attackers occasionally inject invisible Unicode characters into email bodies and subject lines as an evasion technique, this method remains remarkably uncommon in observed phishing campaigns.
The broader security community has focused primarily on detecting invisible characters within message content rather than subject line headers.
This represents a notable blind spot in current email security implementations. Most content-focused filtering solutions concentrate on analyzing message bodies, URLs, and attachments, while subject line scrutiny often receives less granular examination.
By weaponizing this overlooked vector, attackers can potentially evade solutions that failed to implement comprehensive Unicode character filtering across all email components.
Campaign Details and Recommendations
In the intercepted campaign, soft hyphens appeared not only in the subject line but extensively throughout the email body, fragmenting individual words to further obscure meaning.
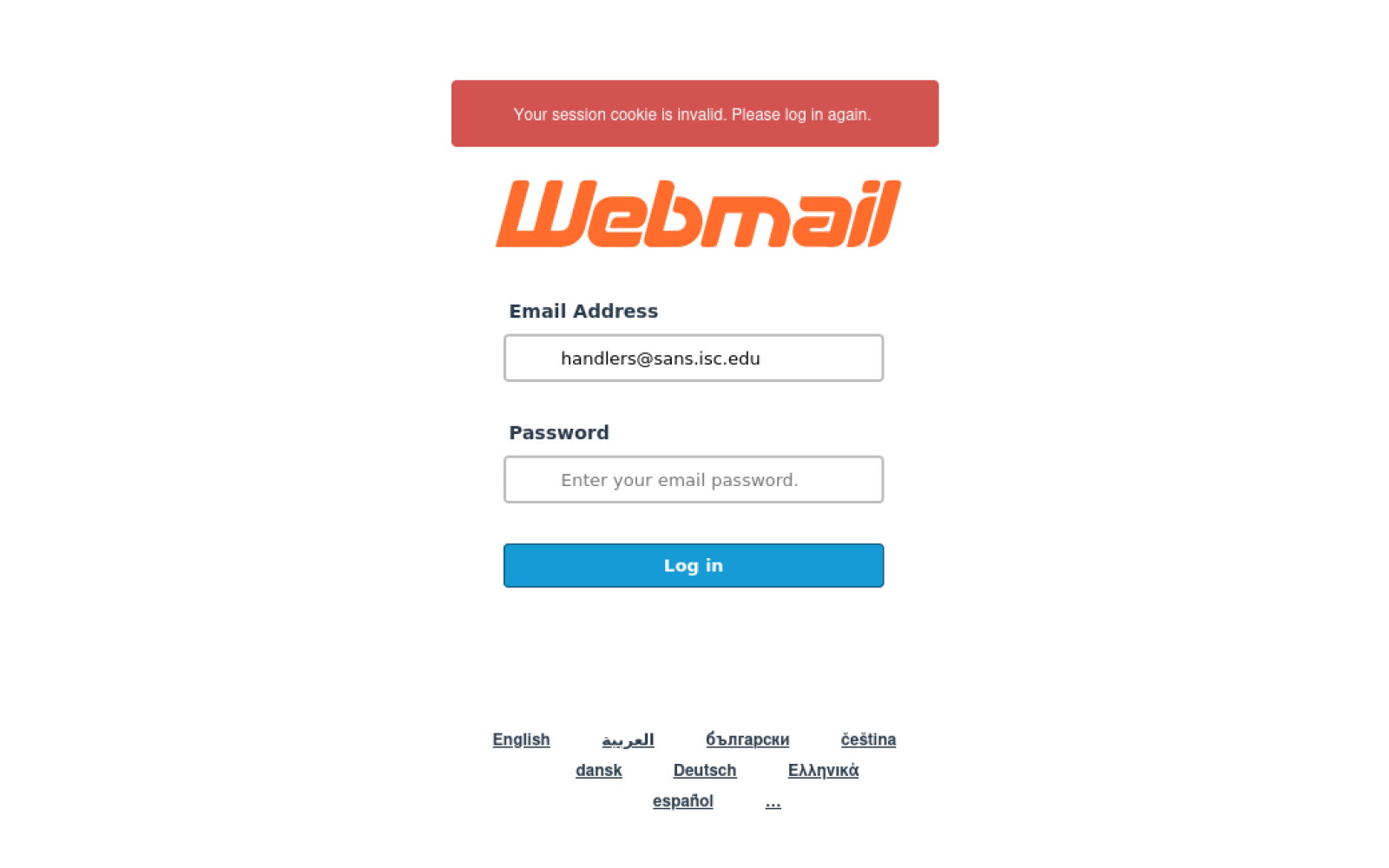
The phishing message directed recipients to a credential-harvesting webpage hosted on a compromised domain, specifically a generic webmail login portal designed to capture authentication credentials.

Organizations should immediately review their email filtering policies to implement comprehensive Unicode character detection across both subject lines and message bodies.
Security administrators are urged to examine MIME-encoded headers for suspicious character patterns and consider deploying more sophisticated content analysis systems capable of identifying obfuscation techniques beyond traditional keyword matching.
As threat actors continue refining evasion methodologies, defense strategies must evolve with equal sophistication.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.




