Cybersecurity researchers have uncovered a sophisticated phishing campaign that exploits compromised hotel booking accounts to defraud travellers worldwide.
The campaign, which has been active since at least April 2025, leverages stolen credentials from hotel administrators to impersonate legitimate Booking.com communications and direct unsuspecting customers toward fraudulent billing pages.
Security analysts from Sekoia.io, in partnership with threat detection researchers, discovered that the operation begins with a multi-stage attack targeting hotel establishments.
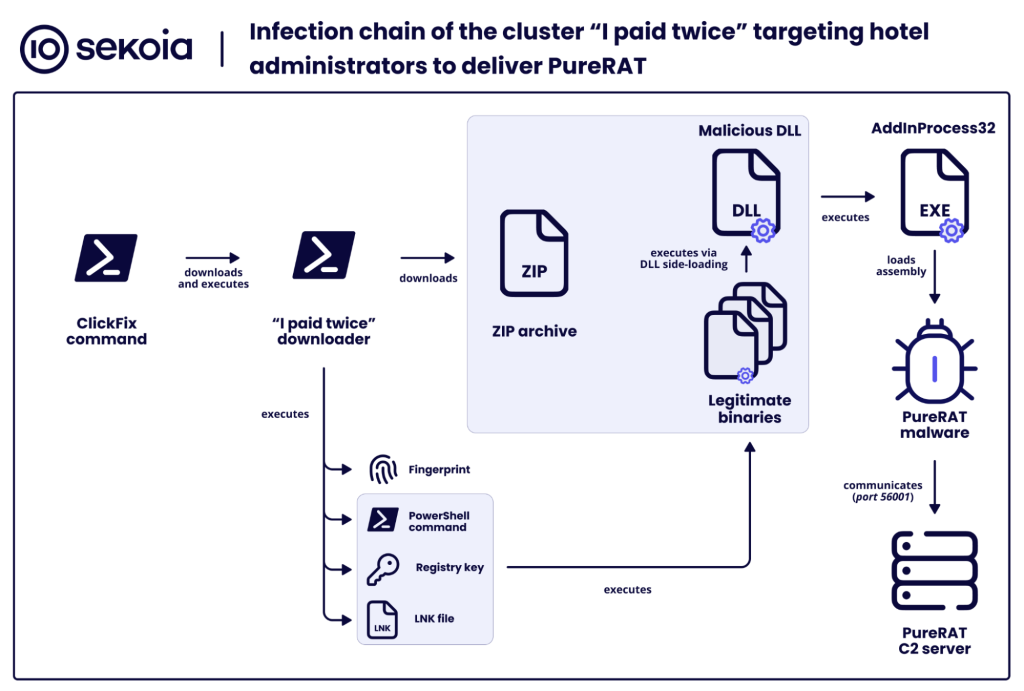
Threat actors first compromise hotel administrators’ systems via malicious emails that use the ClickFix social engineering tactic, ultimately installing PureRAT malware.
Once attackers gain control of a hotel’s Booking.com account, they exploit the established trust between the platform and customers to execute targeted banking fraud against guests.
The initial compromise phase involves spear-phishing emails sent to hotel reservation and administration email addresses.
These messages masquerade as Booking.com communications, complete with authentic branding and URLs that appear legitimate to hotel staff.
At the time of writing, we continue analysing this loader, which does not match any known malware family in our databases. It appears to operate like QuirkyLoader, a .NET loader compiled Ahead-of-Time (AOT).
The emails reference customer requests or booking notifications, creating a sense of urgency that encourages recipients to click suspicious links.
When victims click the provided URL, they encounter a sophisticated redirection infrastructure designed to obscure the attackers’ true objectives.
The initial redirect leads through multiple pages before landing on a malicious website hosting a JavaScript-based ClickFix attack.
This page displays Booking.com branding and prompts users to copy and execute a command under the guise of verifying administrative access to the hotel’s booking extranet.
The copied command executes PowerShell instructions that download and deploy PureRAT, a remote access trojan sold as malware-as-a-service.
Once installed, PureRAT establishes persistence on hotel administrators’ machines, granting attackers complete control over systems and access to booking platform credentials.
The Fraud Targeting Guests
With compromised Booking.com accounts in hand, threat actors shift their focus to hotel customers. Victims receive phishing messages via WhatsApp or email containing legitimate reservation details harvested from the hacked accounts.
These messages claim a security verification issue requires updating banking information, directing guests toward phishing pages that mimic Booking.com’s authentic billing interface.
Unsuspecting travellers who enter their banking credentials become victims of second-billing fraud. Guests discover unauthorized charges matching their legitimate hotel reservations, essentially paying twice for accommodations already booked.
According to its advertisements, moderator_booking purchases Booking logs that include affiliate program access and active reservations at prices from $30 to $5000 for high-value entries.
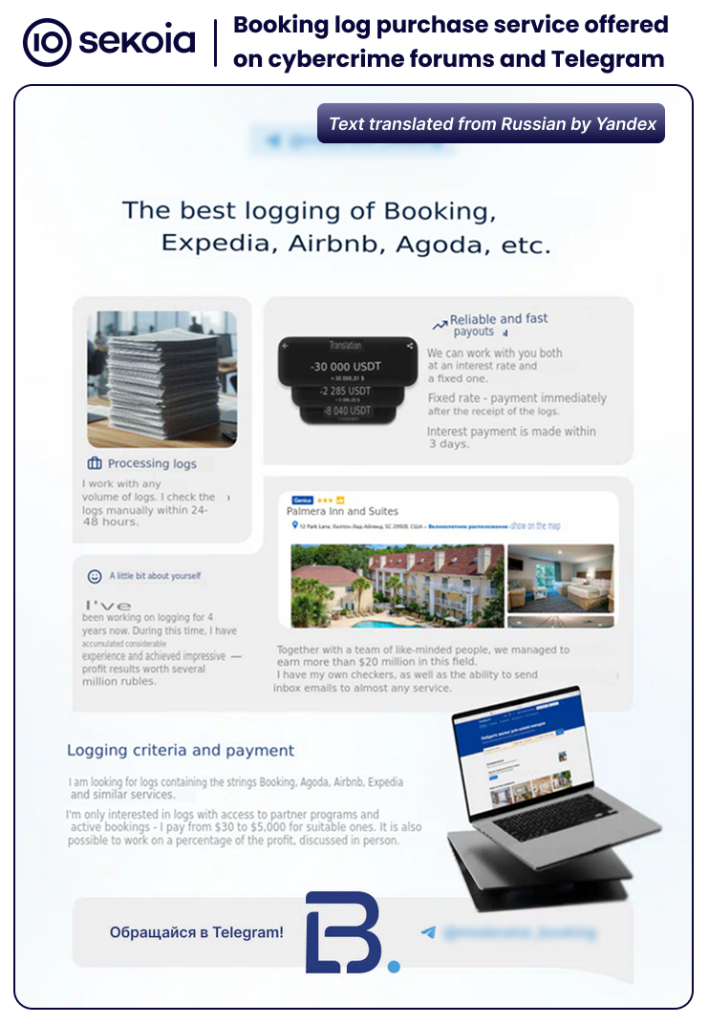

Researchers identified extensive criminal marketplace activity supporting this operation. Threat actors openly advertise compromised Booking.com accounts, infostealer logs, credential checkers, and malware distribution services on Russian-speaking cybercrime forums.
High-value accounts managing multiple hotels in developed countries command prices reaching several thousand dollars, reflecting the substantial profits available through this fraud model.
The proliferation of specialized services including traffers recruiting other criminals to spread malware, log checkers validating stolen credentials, and dedicated marketplaces demonstrates the industrialization of hospitality-targeted fraud.


The operation reflects broader trends in cybercriminal professionalization, where attackers outsource components of attacks to specialized services, lowering entry barriers while maximizing returns.
The campaign poses significant risks to both hospitality businesses and travellers. Hotels face credential theft, unauthorized account access, and reputational damage, while guests suffer direct financial losses. The attackers’ persistence and sophisticated infrastructure suggest the operation remains highly profitable and likely to continue targeting the sector.
Sekoia.io continues monitoring this threat, tracking adversary infrastructure and developing detection capabilities to protect organisations from similar campaigns.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
